Signatory Mobi Made Easy
Upgrade your document workflow with airSlate SignNow
Versatile eSignature workflows
Instant visibility into document status
Simple and fast integration set up
Signatory mobi on any device
Advanced Audit Trail
Rigorous protection standards
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Your step-by-step guide — signatory mobi
Adopting airSlate SignNow’s electronic signature any business can speed up signature workflows and sign online in real-time, providing an improved experience to consumers and workers. Use signatory Mobi in a few easy steps. Our mobile apps make work on the run possible, even while offline! eSign contracts from anywhere in the world and make tasks in less time.
Take a stepwise instruction for using signatory Mobi:
- Log in to your airSlate SignNow account.
- Find your document in your folders or import a new one.
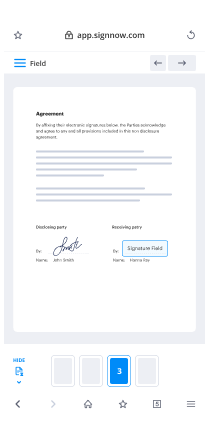
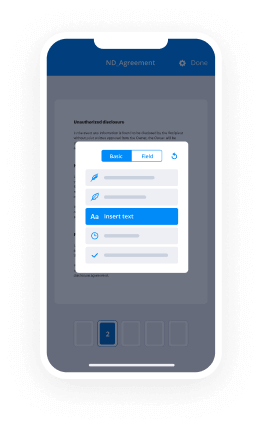
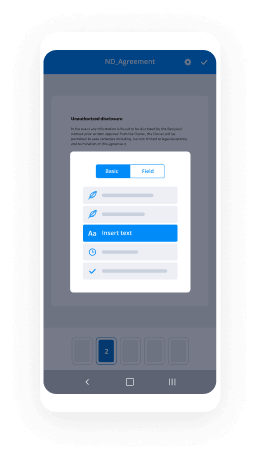
- Open up the record and edit content using the Tools menu.
- Drop fillable fields, add text and eSign it.
- Add numerous signers via emails and set the signing order.
- Specify which recipients will get an signed version.
- Use Advanced Options to limit access to the document add an expiration date.
- Press Save and Close when completed.
In addition, there are more enhanced functions available for signatory Mobi. Include users to your collaborative work enviroment, browse teams, and monitor cooperation. Numerous users across the US and Europe recognize that a solution that brings people together in one holistic workspace, is the thing that organizations need to keep workflows performing smoothly. The airSlate SignNow REST API enables you to integrate eSignatures into your application, website, CRM or cloud storage. Check out airSlate SignNow and enjoy quicker, smoother and overall more efficient eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results signatory Mobi made easy
Get legally-binding signatures now!
What active users are saying — signatory mobi
Signatory mobi
yes so in yesterday's class we have discussed about virus worms okay trojan hearts today we will discuss spyware adware spam mails there is spamming and the pc intrusion denial of services sweeping password guessing this type of unfishing and farming these type of things and all i mean types of threads and all we have seen correct so what is trojan hearts trojan hearts it's another type of virus or another type of malware what is the use are not sorry not used how it will be react means it look like a very original program it would be look like a very uh useful program okay so by seeing the trajan hearts how it will be means it will be download as suppose we are downloading many softwares now from different different websites but it is looking very useful but background it will collect the information and it will make us to damage the files or delete the files okay or else it will collect some basic information and send to the spyware okay then spyware it will collect again it will send to the owner who have sent it okay so trojan hearts it's a program that appears armless are you seeing no the slide i'm sorry in the screen you can see the trojan hearts is a program that appears armless armless means it's looking like a good program okay so but it will do the damage for our computer for our data okay that is which we have stored in our computer to corrupt the file i will damage the file or delete the file even okay so it will make us our computer to be marked uh small practice sorry malfunctioning very quickly okay which one trojan hearts okay it is another type of virus or another type of threats which we are facing in our day-to-day life have you got it so whenever you are scanning your computer you will come to know the anti-virus will tell this have this much of frozen heart is attacked this type of like that okay so have you got what is trojan hearts trojan hearts is a program it's look like a good program or it is look like a useful program but actually it is damaging literally it will damage the files which in our computer okay have you got it how do you understand what is the uh sorry how the closing hearts will affect hello i asked the question have you understood how the trojan hearts will the remaining things are we have discussed let me go to the next one next topic that is cookies we are going to see okay the cookies itself we have seen in the previous class nowadays also we are i mean this today also we are going to discuss a brief about the cookies okay the cookies also it's called as what what is cookie we have seen the last class we have seen on cyber safety what is cookie can you say it hmm what is mean cookie small piece of data from websites so it is a file or it is a text file or it may be whatever file it is a piece of information or else it is a file which we are content containing the activity which we have done on the browser so suppose today i open the chrome i download i just visiting some website okay what are all the activities i have done on the website that information stored as a file in our computer itself okay okay that is called as what cookie it is a information file related to the websites or webpages which we visited an activity which contains the activity which we have done on the websites which we visited on the day okay that is called cookies okay so in the cookie many things are there tracking cookies that is raising cookies means it will trace it as you can see the session data session data means for example we have used that one i will uh you can also come to know for example whenever we are not connected to the internet but if you try to open the page we will get the google image but it is not real have you seen no i have asked already the same question that is because of cookies so it will every sessions every every session means whenever you open the browser whenever you close the browser okay or else whatever the websites we are visiting okay so based on the thing it will automatically store there the data or the details which we have doing on over the website okay this is called session data cookie and second one is it taking tracking the information so information means what are all the websites we visited when we visited even time everything okay date time everything okay regularly when we are visiting for example two days once we are visiting the website hours daily we are visiting some websites okay so that information it will be stored okay so that will be used for some other purpose so some other purpose means it is a basic information it won't send to others but it will be stored in our computer only but what is the thing whenever the spyware or anything malwares we have seen no it will get the data and it will send to the others okay so from there others will gain the benefit what benefit they will come to know what are all the website we visiting for example how much bank transaction we are doing rlc what is every username and password for the login for the email id so all those things generally i'm saying okay suppose we are searching anything on the internet suppose i want to buy one new new mobile or new laptop something else means so it will tell that what we are doing what we done the search okay so based on the search we are receiving the popups ads no or else what we searched the flipkart if you open your account in flipkart immediately it shows that the things at first have you seen not only flipkart whatever e-commerce website or else whenever i have set another one example suppose we visiting on one songs or anything even videos on the youtube whenever we open the next time youtube what do not be visited that song is correct exactly so because of what because of the cookies okay so we should don't delete the cookies once we completed our information means that's what i am coming to tell this okay so that is very important and second one public computers we should delete the cookie once we have used it better to avoid to use your personal data and you know the public computer public computer means internet centers or schools or colleges or office okay these are not our place it is public place public placement in the sense of what for example in school suppose you are using one computer that is not your computer no so next day another person may come and sit on the computer no correct like this in office or okay that is called that in the sense i am saying it is not it is not our personal computer it is public computer so in order to operate yeah so in that the type of computer is better to avoid to do the important transaction or any confidential works at all we can avoid to do it okay suppose i want to do that there is no other go i i don't have a computer i want to open my mail id in the public computer only in the browsing center only likewise if your thing means then we can have to delete the system that is not a issue we have to as you said we have to log in and properly first we need to sign out and second thing we have to clear the browsing history and cookies we have to clear the cookies once we done mean then we will be in the safe better we can on the we can do all the transaction uh i mean opening or anything in the igna in car window mode if you open means that will be very personal browsing okay there is no history but cookies only we have to delete okay that's what we have to point have we got it so these things and all we have seen in generally in the last class itself no that is the last class means computer safety sorry cyber safety we have done correct yes yeah did you come to the things so we have seen what is thread what is malware what are the malicious content we have seen that is types of virus and pc encryptions okay uh trojan hearts where all those things we have discussed let me come to the thing so what is the solution sir suppose we are asking the question sir we know all the problems what is the solution very simple simple thing is i have said the two things for you first thing you have to use the original antivirus okay you have to install in your computer first thing second thing you have to daily at least once in a week we have to update our antivirus our antivirus should be in to the up to date it should be in the up to date then we have to do the scan we have to give the real time protection okay and we have to scan all the files especially all the computer i mean entire computers at least once in a week okay with real-time protection then it will find out some virus it will delete it it will save our uh it will save our computer as well as our data that is which we stored on the computer from the amp full contents like with this virus or bombs or anything have you got it so that is the thing active protection okay active protection mean that's what and preventing measures so how to prevent sir for example even i can sir i have installed the antivirus program shall i just go uh what is the thing shall i go to the malicious website sir shall i go to the wrong website shall i download the virus file sir is it any problem it will cause any problem if you're asking means definitely it will cause the problem okay it is not mean that if you are having original antivirus means it does not mean that we should not do whatever thing for example we are taking basin no correct isn't it or not rabbi is fashion yes yeah for example drab is seen or some other rails for example smallpox vaccine or chickenpox were seen if we are taken but wantedly shall we just inject the bacteria or virus which we have comes we should be safe no for example just for uh thing i'm saying suppose the coronaviasin is available suppose we have take the injection okay so we are vaccinated suppose then shall we contact to the corona person affected person do we do we contact do we have a very close contact with them awesome no because even correct even though we have vaccinated we should be the same for we should follow the same protections okay we should keep the distance social distancing and wearing the mask and gloves and often watching our hands okay and the face also everything okay so that will be giving the protection from there in the real time okay so that's what i'm i'm coming to tell preventive measure these are all the preventive measures sir i have installed the original antivirus in my mobile sorry in my laptop or desktop so i no need to worry about the virus that it is not certainly okay we should be very much careful and we should be very much sensitive in these things okay so these are all things active protection means use the antivirus program and we should update that that is very important okay and then preventive measures that's what we avoid to give the we should avoid whenever the site is the website is redirecting means better we can close the website or else if any virus is downloaded means we should delete that okay so we should not keep the files we should not keep the unfold files we should not go to the malicious pages web pages or websites that we can now that should be avoid suppose we are inserting the pen drive first we should do the scan then only we should open the pendrive okay so firstly we have to scan our computer at least once in a week as well as whenever we are inserting the pen drive or any memory card in your computer means we should scan with the original antivirus okay with the updated antivirus that is very important okay so if we are keeping mean then we have to these are i mean these are all the preventive measures from the what from the malwares okay virus bombs all those things have you all understood what is the point have you understood yes sir yeah good okay let me come to the next topic then that's what solution to the virus see i have said no that is there are thousands see i want to tell one thing daily n number of viruses are just spreading on over the internet for example yesterday maybe one virus today new virus okay so that's what i have made a point you should you people want to do watch that's what i have said two points but you forgot it antivirus that is and second thing what i have said refresh the antivirus yeah update it is update we should update the antivirus okay update then we have to do the scanning okay so that's what if you are up to date means then whatever virus or whatever thing it is means we should be get prevented from the things okay so we should scan and we should keep our data to be very properly we can maintain our computer properly okay these are all the things okay for the solutions for those things let me come to the next one and they have said no i have i have said what we discussed scan all the systems okay that is daily at least instead of it is not possible to do scan for daily at least once in a week we can scan it and we have to use only the genuine softwares genuine software's means not only antivirus windows or whatever software we are installing better we go to the genuine one means that is original one means we don't need to bother about much about the viruses or anything okay and disconnect from infected system from the network suppose if you are having the network the network virus is there but in your computer alone you have installed the antivirus means it is no use because network means connected to the many computers are connected no that's called as network for example lan local error network like it okay so even though if your computer is having the antivirus it will protect your computer only but whenever we are connecting yeah i want to say something okay okay so whenever we are connected to the network means network means any networks may be internet or whatever thing so our so from that we can very many targets are there that is many virus may be already there in the network so it will affect it may affect our computers okay so whenever we found it is infected networks means we can avoid it that and one more thing whenever we are inserting the uh any pen drive or memory card or whatever thing in our mobi sorry in your pc we must scan with our original and updated antivirus that's what we have seen know so this is the thing we have to do okay and then next one uh that is signature data basement that's what i have said we have to update up to date means we we need to daily we have to update our else once in a week at least we should check the updation we should check for updation if any updation versions is there or any signature database means patchworks that is any patch files okay that batch files we have to automatically whenever you click update means automatically it will be get updated okay in the antivirus i'm saying okay that's what the point run frequently full scan that is once in a week at least okay these are all their active protection so how to be protect from all the malwares of malicious content in the real time uh keep our computer on the data to be secured means this is the base okay let me go to the next one and preventive measures i have said again we have to keep our system up to date and one minute by one minute one minute [Music] yeah i'm audible hello yeah yeah because i get one phone call that's what okay come to the things okay next one use cautions and downloading files whenever we are visiting any websites means we should first alert whether it is the original website or fake website that way i have shown one live example know for example banking websites the last class i mean last class means last lesson chapter yes for example banking websites and all if you're going we should allot what are the things whether the green log symbol is there or not positive we have to ensure security yes yes then second thing whether it is original website or not we have to make sure it okay because many people they have created the fake websites also okay in order to gain the data okay so that's what whenever let me come to the point whenever we are downloading any files whatever file it may be okay especially maybe video or audio or any there is songs i'm saying or else any any files whatever image okay so we have to make sure whether the file contains any um on full content or not how to check sir once you download before you open the file we should run a scan for that that is we should scan the file okay so after once we done the scanning there is no virus if it is shows means then we can open the file the download downloaded file okay or else if it is contain any virus means better you have to delete that file because once we allowed that file in our computer what will happen it will automatic that's what you know whenever we open the file it's need human action which one virus need human action in order to replicate no so it will start to once we just open the file that is the action we are giving so once the human action is done means automatically it will started to spread that is by replicating itself so finally if you corrupt our computer it may slow down our computer or whatever the thing or it will just delete some files or damage some files okay so we are thinking that okay our system is smooth but slowly it will like a slow poison to slowly eat up all those things okay to damage your computer okay so this is the thing and be careful with the email that's what unsolicited email as you're seeing the word no i'm just uh highlighting open unsolicited email what is unsolicited means unknown emails are strange emails okay for example we don't know who's to send the mail if you are just if in in the mail contains any link means yesterday also we have discussed later to that isn't it so whenever the link is spamming mail we have seen could you remember can you remember that's what okay so spam fields or any mails it contains any link means don't click the link unless you have verified whether it is not authenticated mail or not if you know whether the mail has received from the known person or known website means then we can go ahead okay unknown spam mail center we are receiving no number of mails so just don't click on the link what will happen if you click the link means as we yesterday what we discussed later to that it will gain the information from the mail okay from the inbox it will spread slowly yeah like spy yeah it's not no it's not spying man that is different one that is different concept here what will do it will gain the information means in the sense of it will know that it will corrupt the mails it will delete the mails also okay and what are the things next thing it will or damage download files you know computer files i'm saying which we stored in our computer okay so these things and all we should be pretty much about the spamming mails and spacing camps and all we should be very much careful don't give it any information related to that link suppose you are that's what we have seen any links or whatever website unless it is important or authenticated don't give your details like mobile number email id from last chapter onwards we have discussed no that was the thing okay and just disable the running of scripts and cookies we have to disable i have shown no in the last chapter how to go to the for example if you open the chrome or any other browser whatever browser just disable the cookies some websites only needed there for authentication purpose it's required the cookies is very much enabled it's it's mandatory so for that site alone we can give watch we can allow the cookies okay i will know it or not i have shown once yes sir yeah could you remember could you all remember dear children this is a live video i have done yes yes that's fine okay let me come to the point yes okay that's what i have said no disable the cookies if it is possible for the things we can better you can disable the cookies or else we i have given the settings what disable the third-party cookies i have given that uh sorry i have done in my computer no i have shown to you correct so better we can do that okay then solution for spams and ever dropping that's what i have said no the mails okay don't go with that unknown mail just don't open the unknown mails uh if you simply open the mails also that don't go with the click sorry don't click the link which is given in there sent in the mail okay unknown links means unknown mails means that spam mails okay so these things and all we should have uh avoid in order to keep our system to be our data to be protected well protected okay that's what using the anti-spam software anti-spam software that is one minute bar one minute i'm getting one repeated phone call one more minute i'm so sorry uh uh sorry children let me come to the things okay so anti-spam software these softwares and all automatically for example let you you suppose you are using the uh google that is google account means already it has it has what is the thing it is protected with the antivirus okay they are having their own security they having their own firewall okay so have you downloaded any attachments from the mail so far have you downloaded any attachments no no my god have you sent in have you send any attachments to somebody have you sent a any file as attachment to the mail i'm asking is it no for that also or else you didn't get my question so how you sent your answer sheets how are you sending your answer to your teachers yeah that's what see that's what i'm coming to tell so whenever we are attaching the file will be get scanned before it is attaching to the uh our gmail sorry our account our email account the spy the file will be get scanned and if it is found there is no virus mean there is no malware any harmful content means then only the file will be get attached to the mail then only you are sending no you are just by clicking the send button so likewise whenever we are downloading any files that's what i'm going to tell whenever we are downloading any files from the email means as attachment automatically it will get scanned okay so when try to see that whenever you download any attachment from the mail it will just showing that scanning just a few minutes few seconds only it will show you immediately it will the scan will be completed and we can download the the file the file will be get downloaded okay let me come to the point okay so this is called anti-spam software the anti-spam software what it will do it will just send the filtering center filtering means so it only allows the proper mails suppose the mail contains some malicious content means that's what it will redirect to the spam folder yesterday i have said no for now have you seen i give given on task have you seen that spam folder in your mail in your account have you seen or not yesterday i have said you see that they said red color good good so that's what so in the spam folder when it will be dumped means that automatically the email our email provider will segregate whether it is proper mail means without any malicious content means the mail will be get delivered in our inbox okay suppose the mail contains the malicious content now the attachment contains some harmful content means if it is respectable male means the suspectable males fully it will be redirected it will be stored that's what it will be stored in the spam folder okay so once you open the spam folder we much very much alert don't click any links which is given in the spam mail that's what we have discussed no that's what have you understood that hello yes sir and digital certification so some other documents they are giving that they are providing the digital certification that is authenticated it is purely sent by the this center all those things will be verified that is called digital certification for the about the file which contains no harmful content okay that is the thing that is the digitally it will be certificate and next one is digital signatures okay so it is in the online payment journal if you're done means you can see the digitally signed have you seen the word digitally signed means that for example i will tell one thing have you paid the online eb bill or something else not shopping generally likewise any government bills or anything else eb bill or water tax or any property tax have you okay that's for example i will tell that whenever now the government is giving no not only government even many corporates also i'm saying okay so whenever we are doing any online payments online payments means in the case of these things i am saying not about e-commerce that is different case okay so whenever i am paying the water tax or property tax or anything else i will say what are the thing eb at this elder city board will ev will be are paying means you can you can download that uh file for receipt that's what no yeah immediately you can download the receipt in the receipt it will just giving the signature signatory authority of sign but sign is not mentioned but instead of that it is digitally signed digitally signed means it is approved from the concerned person okay that's what the thing okay just seeing that you can come to know that okay and next one is keyword filtering okay so that's what keywords are faced any abusive words or anything if you're trying to nowadays it has developed in our even all the mail providers even yahoo or gmail or other thing okay so it will filter it filter means it won't allow any unparliamentary word or any abusive words which suppose we are making the sentence have you typed the mail automatically it will suppose you are typing thank you means th only you will type remaining thing automatically you show the suggestion no in the email i am saying not in your phone phone that is different yes yeah that's what so it will predict what we are coming to type which one the mail provider will predict us what we are going to type okay so it will complete the phrase or complete the sentence or else the word okay so just by giving enter automatically it will be filled likewise it will filter the word any abusive words we are about to type means it will avoid that word that the word will be automatically will be deleted or else it will give the alert for us okay that is keyword filtering okay let me come to the point again what we have discussed the same thing keep your mail address private that is don't publicize your email id to everyone uh don't give the information that's what we have discussed from the last chapter onwards okay encrypted sites whenever we are visiting any website means make sure the website is encrypted or not encrypted means that is secured or not okay secured shell that is using my ssh okay then https http https http means you know hypertext transfer protocol yes there is no denoting watch it is a secured site one minute let us open some site okay one minute that i will open the chrome and i'll show it to you just a minute it is getting open um this is the my screen is visible now yes sir okay sbi simply i just run the search i will just click this this is the original website of sbi you can see the log same can you see this lock sign that is it is a connection yeah that is it is showing what it is digital certificate just now we have seen no valid certificate as given for this website okay for example this is what uh if you click that more means we can come to know that for example i'm just giving a lac okay one minute for example can you see this https can you see that that's what can you tell the full form [Music] that's what that's the main thing we are discussing now what is that yeah thank you secured okay let me come to the point you can see so that's what we have seen okay i will show that whether it is shown or not okay some other website it will be mentioned okay so another website it will tell that it is encrypted sites okay so you can see there's some other website you can come to know that okay uh dear children one more minute is there kindly rejoined okay so rejoin if the link has disconnected okay let it come to the thing so encrypted sites we will discuss oneness discuss disconnected means just rejoin it okay i think it's two seconds are there so just see the full form https and ssl yeah the last session we have start about that uh discuss about the https literally we have seen okay ssh means secured shell okay the the secure chill the website will be contained so it will not allow any malicious content inside inside the into the website as well as what it won't send any malicious content to some other website it won't spread it that's what okay so this type of thing this type of websites if you are visiting means we no need to worry okay let me come to the another thing install personal firewall on the computer that is in our default we have the firewall settings suppose if you are using the windows operating system means okay what is firewalls are if you're asking the question the firewall it have two types okay what is generally what is firewall means it is a security settings okay for filtering the data filtering the malicious content okay firewall is just act like a wall it will filter the malicious content uh getting inside to our computer as well as it won't allow any malicious content should not be travel from our computer to other computer also okay it's just like a wall or just like a filter okay have we got have you understand that what is firewall yes sir yeah in this firewall we have two type of firewalls that are there in detail if you want to come to know me one is program another one is hardware okay honest programming sometimes if you are visiting if you are seeing your book they may given like that firewall is a program so what does that program will do actually what is program can you say we have discussed uh sorry discuss a lot about that what is program can you say that this set of information is correct okay so it is that of instruction which we are given okay like with the firewall is a program that is it's a set of instruction what instructions are suppose we are asking means we have that is the who developed the firewall they have given already the instruction which file how to check the file or how to check the malicious content in that file if it is okay means what action want to be done if the file contains the malicious content means it will block it okay that is the firewall that is the software it is a program firewall and second one is it is a device firewall another thing we can set as a device device means it's the hardware it is another one device it will take all the data it will check the data if the data contains any malicious content means it won't allow if the data doesn't contain any malicious content then only it will allow to getting into our computer or else from our computer also too have we got it so where we can see this type of hardware firewalls are in our computer for example now i am using one compute no in this computer you are which you are general computers and all firewall will be a program only okay but when it will be a hardware device means whenever we are going with the big networks okay big number of land networks or number of metropolitan area network are very big institution if you are going means they will keep one device as a firewall so for example let me tell one example in your room 10 computers are there in the network okay so any one of the computer want to receive any mail means otherwise any on file means so it will pass through that device then the device will check the file if it is contain any malicious content or not if it is not contents means then only it will allow to our uh to the computer to our network have you got it likewise from our computer if you want to send any data to some other computer or some somebody's in the world means the data first would want to pass through the device then the device will check whether it is contained any malicious or wrongful content or not if it is no means then only it will allow have you got it this is like as a physical firewall rls hardware firewall two type of firewalls devices are there let me come to the point okay so that's what internet security software that's again come coming to the point uh we have to install the proper antivirus program that is internet security then we have to keep on up to date and everything we have discussed and avoid public wi-fi it's also we have seen in the last chapter okay in regulation our airport like this we are getting the free wi-fi even some buses that's i have said no even some bus nowadays they are providing the wi-fi whenever we are getting into the bus okay so i don't know whether it is in some other places i have seen okay so in these things don't use such type of wi-fi so just for downloading some things are means that's up to you but what are the thing it is insecure that's what i'm coming to tell okay but i am strictly i am saying that don't do any confidential works using the public wi-fi sir i want to transfer some amount sir i want to use google placer or else i want to use phone pager this is very confidential no correct or not so we are giving our pin everything no not only bank transaction our email checking or any login any credential oriented works should not be done should not be carried over on the public wi-fi that's avoided okay so these things now we have discussed once again we have just to have a recap with that okay let me come to the things solution to pc inclusion what are the pc intuition we have seen three type of intuition we have seen sweeping the second thing is what denial of services that we have seen no would you remember hello i will show the content we have seen like a classification things no the starting of the chapter one minute yeah as you're seeing no password guessing i forgot it see delay of service sweeping and password guessing can you get it i'm just so let me highlighting to the point one minute okay okay let me come to the things so in in order to avoid the pc intrusion that is uh delay of services or password guessing or sweeping sweeping means what is the thing completely to destroy all the data to delete all the files from your computer okay so how to uh how to protect this from this malware for asking the question authorization authentication and firewall just now we have discussed about the firewall no so what is authorization we should use the proper email id and password okay so authorized user only that means what don't share your email id or password not only email id i'm saying whatever login id may be related to the bank or some other website or anything else okay so don't give your personal credentials that is any login information to your friends also or even somebody else also have you got it so that person only want to come and they have to come in the sense of i'm saying they only have to log in don't reveal to your anybody that's what i'm say community that is called authorization whether that person is open the mail id or not for others if you know for example if you come to know my mail id what you will do for example you will open it but it will be taken my account only now so it will showing what i only open it because i have revealed my password means have you got it have you understand or not hello see just to say that at least whether you got the point or not okay let me come to the next one authentication okay the password should be very much protected and whenever uh i want to tell on another one information for you for example whenever we have the password or whenever we are giving the first time as password it should be very tough don't use your name don't use your father name mother name okay don't use the date of birth okay are some important names are important numbers or your favorite numbers such type of things and i'll avoid it whenever you are giving us a password you can set a password for whatever thing it should be minimum eight digits okay it should be minimum eight digits and you know it should contain one alphabets that is you should contain minimum one uppercase letter what is upper case uppercase lowercase means what can you say what is uppercase uppercase character and one lowercase character one special symbol one number one number okay minimum i'm saying i'm not saying it is a it's coming in four digits but when i or what i'm going to tell minimum you should use this one and you should avoid what giving your name or your parents name something else don't always just avoid to give this a type of names or anything that of birth as you are well i should yeah yeah why should we avoid this a good question rajesh good for example i will tell one thing you know my name or not okay for example if for my mail id if i keep my name as a password means you can able to open suppose you are for example you means not you i'm not intentionally i'm saying suppose you want to hack my mail okay you know my mail sorry you know my name and you know my date of birth or something else you know you will try or not correct yes suppose i set my name as a as my password then what will happen you can easily open no have you got it yes sir excuse me that's what it's a good question see remaining children also try to understand so for example you may think that sir i'm you about to use part of my name only sir or else i'm using part of my father's name only sir how they will come to know this null not better avoid okay if anyone can easily know your name your parents name and all it is everyone it is visible and you are dead off but everything is visible okay so if you are keeping that as a password means then the anyone that's what i have we have seen the last point what is the last point of peace intrusion sir last threat of peace inclusion sorry last threat yeah they will try to guess the password okay for example his name is bhaskaran so he will keep bass or baskaran like they may think it is absolutely not correct no so that's what i'm coming to tell so don't keep your parents name or your date of birth or anything else related to your information don't set as as that is the password for the uh any account not only i'm talking about email whatever account whatever login information you are keeping just give a secured thing that is called authenticated one you have to use okay and firewall we have discussed this watch what is firewall you know it is a it's giving protection from all the malicious content it's act as a filter it will check the incoming data as well as outgoing data okay so firewall having two types what are the things physical firewall and virtual firewall the virtual firewall is called as program firewall program okay and physical firewall means it's a device that is a hardware that we have seen no i mean seen means just now we have discussed have you got it hello yes sir try to answer okay did you come to the point and prevent you measure that what i have said so whenever we are sharing any file suppose you are sharing the files in the drive so maximum now we are sharing our files in the drive only so whenever we are shared any file in the network means you should know the three type of permissions i'm highlighting i'm just i'm highlighting now in these things read permission write permission execute permission okay what is the rate permission means if you're giving if you shared any one folder from your drive or any file to your friends means if you give read permission only means they can only read they cannot modify it they cannot open and they cannot do anything all over it that is read permission right permission means they can read as well as they will write execute permission means that is again in the execute permission it will not for the general files some some matured files some other more extendable files they may use the executable permission like we said programming like that online programming modules are there okay for example online itself we can run the program have you seen such platform or not have you seen online interpreter say yes or no okay one minute i will show it to you for example i'm just giving i'm just typing python program online compiler i have said no interpreter compiler for example in this things it is one of the website we can get it one minute i will show it lively it will get bloating i think it will take some time one minute i will show then you can easily understand that what is executable permission means okay instead of reading that see for example this is the file i can type whatever thing for example i'm just giving print on minutes it's loading power one minute okay so i'm just now print one okay now you have to tell again we are coming to the python if i want to get one number from user can you tell what is the statement to get the number from user how to get a number from the user input i'm asking do you know it or not input in yeah that is any one variable no so for example i'm just using q equal to input integer i want to get into input of no you people still you are very lag in the program are you practicing or not nowadays we are just doing the networks this theoretical contents but program is very important i have said many times to you okay the total standard theory concept and all will not work out just to ten percentage they may ask remaining full of program only okay let me come to the point for example i'm just giving enter number okay where where the number will be get stored q correct q so i am printing q what will be get printed again i am running this one it is asking the number i'm just giving 67 it will print 67 that's what this is called executable permission whenever we are running any script on over the internet it is executable permission read only means for example some some websites have you seen we cannot able to copy the content have you come to the sites some sites we cannot copy that content okay fine fine i also not in remember if i know the whenever you are searching for anything you will come to know okay so that is read only permission we can read only we cannot copy it we cannot use the data for we have manipulated manipulation okay write means we can read as well as write there is a normal file executable means just how i have said okay so file permission again warner others group three type of permission for the files warner means they have full access they can do whatever thing that means what warner means who have created the file that's what okay group means we are sharing to somebody else with the permission read permission or write permission or executable permission with that others means we can by seeing giving on the read permission this is the generally things so why means in order to keep our file to be secure that's what i'm going to tell okay fishing and farming attack i have said these things we will see in the next tomorrow class because you may have another class it should not affect your other class also okay so now it is four one okay tomorrow class we will uh see these things seeing farming attacks what are the preventive measures for this type of right from the attacks okay and physical protection how to keep our system to be protected physically as well as the virtual things okay firewall again i have come to the point again what we have discussed i have said no software firewall hardware firewall so remaining things channel we will see in the tomorrow's class have you came to know something else today from the today's class what we have discussed have we come to the point what are the things we have discussed we have seen cookies session data cookie tracking cookie and public computers in order to avoid we can delete the cookies so some proventy measures we have seen and active protection preventive measures these things and all we have seen okay keep our antivirus to be up to date spamming mails don't download from uh unauthenticated websites okay at last we have seen authorization of mail and authentication of not only mail generally log in any plugin permissions everest dropping okay anti-spam program these things now we have seen just overall we have discussed about the protective and sorry safety measures while we are dealing with the computers that we have seen tomorrow let me complete uh the remaining topics thank you dear children you do i mean you have any doubt no discussed okay tomorrow let me see pc intuition also we have seen tomorrow let me discuss the remaining topics thank you to all thank you sir thank you thank you
Show moreFrequently asked questions
How do I eSign a document before sending it?
How can I sign my name on a PDF?
How can I sign emailed documents?
Get more for signatory Mobi made easy
- Print signature service Joint Venture Agreement Template
- Prove email signature Summer Camp Permission Slip
- Endorse eSign Technology Assessment
- Authorize digital sign Free Oregon Rental Lease
- Anneal signatory Profit Maintenance Agreement
- Empower electronically signed Thank you Letter for Donation to Church
- Try digisign Trainee Daily Progress Report
- Add Commercialization Agreement signature block
- Send Photography Proposal Template signature service
- Fax Award Certificate countersign
- Seal Hardship Letter signatory
- Password Settlement Agreement initials
- Pass Freelance Graphic Design Contract Template eSign
- Renew Deed of Trust esigning
- Test Trainee Daily Progress Report digisign
- Require IRS Form 1040-ES electronic signature
- Send gawker mark
- Accredit undersigned electronically signing
- Compel assignee sign
- Void Painting Quote Template template signature
- Adopt log template email signature
- Vouch Colorado Rental Agreement template signatory
- Establish Printing Quotation template electronically signed
- Clear Compromise Agreement Template template byline
- Complete Camper Health History template esigning
- Force NDA Template template esign
- Permit Power of Attorney Form template signature block
- Customize Wedding Photography Contract Template template signature service