Signed Golden Ticket Made Easy
Upgrade your document workflow with airSlate SignNow
Agile eSignature workflows
Instant visibility into document status
Simple and fast integration set up
Signed golden ticket on any device
Comprehensive Audit Trail
Rigorous safety requirements
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

Your step-by-step guide — signed golden ticket
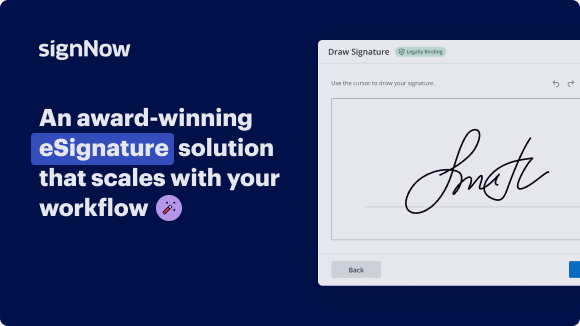
Using airSlate SignNow’s electronic signature any company can accelerate signature workflows and sign online in real-time, giving a greater experience to customers and employees. Use signed Golden Ticket in a couple of simple steps. Our mobile-first apps make work on the run feasible, even while off-line! Sign contracts from anywhere in the world and make tasks in less time.
Follow the step-by-step guide for using signed Golden Ticket:
- Log in to your airSlate SignNow account.
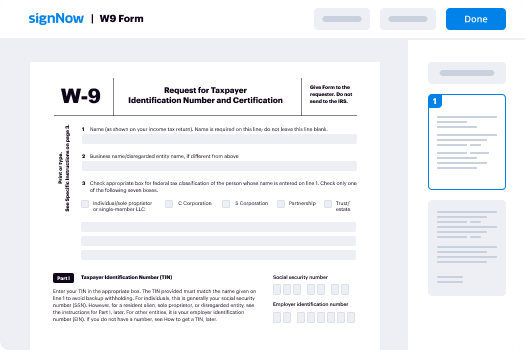
- Find your needed form within your folders or import a new one.
- Access the document and edit content using the Tools list.
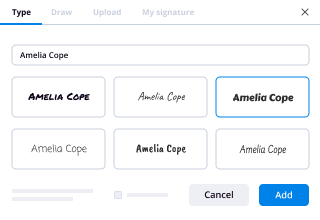
- Drag & drop fillable boxes, type text and sign it.
- Include several signers by emails and set up the signing order.
- Indicate which users can get an completed copy.
- Use Advanced Options to reduce access to the record and set an expiration date.
- Press Save and Close when completed.
In addition, there are more enhanced features accessible for signed Golden Ticket. Include users to your collaborative workspace, view teams, and monitor cooperation. Numerous customers across the US and Europe recognize that a system that brings everything together in one unified digital location, is exactly what enterprises need to keep workflows performing easily. The airSlate SignNow REST API allows you to integrate eSignatures into your application, internet site, CRM or cloud storage. Check out airSlate SignNow and enjoy faster, smoother and overall more productive eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results signed Golden Ticket made easy
Get legally-binding signatures now!
What active users are saying — signed golden ticket
Sign golden ticket
okay in this video we're going to take a look at the Kerberos golden ticket attack now this is not so much a privilege escalation attack where we are going to kind of use it in that way in this video there's more of a persistence attack so it's like when you've already got access to some pretty high-level stuff in the domain and as you'll see in the demo we do actually have the option of just using the administrator account instead so this is when you've pretty much already compromised the domain this is gonna be a way to keep persistent access to that domain because if they change the administrator account password that's not gonna make any difference for this kind of attack so this machine that we're on here is just a separate standalone machine not part of the domain not got any kind of authorization on the domain on the network this machine we've got over here is a domain controller for our target domain this scr m dot local domain is when we're trying to attack and now the key part of this attack is this account here which is a built-in account that exists on every Active Directory domain and it's called krbtgt KR b stands for Kerberos TGT is ticket granting ticket but you can't really need to understand that side of things too much all you need to understand really for this attack is the the password hash for this account even though it's disabled this account gets used its password which is generated automatically by the system that gets used to encrypt data that is sent by Kerberos and this is kind of like the top-level secret password that encrypts everything to prove that it is a legitimate completely authorized Kerberos ticket so if we can get the ntlm password hash for this we can then use that with tools like mini katz to create what's called a golden ticket which will allow us to impersonate anyone we want so let's take a look at that in action for this first part of just getting the ntlm hash we're going to assume you've already got a way to do that so if you want to look at one way to do that you can watch my video on DC sync attacks which is what we're going to use just in this demo so just as a quick refresher if you look at the security on the root of the domain you'll see this account we're going to use as a demo this t-star account has got this position here replicating directory changes which basically allows them to impersonate a domain controller and synchronize password hashes from all user accounts again that's covered in great detail in another video which I'll leave a link to in the description but for now we're just going to kind of do what we did in that video do secrets dumped rpy i've already set my DNS server to point to this to main controller so we can just do the main name we don't need to do the DC IP address we'll put that user name or put his password and then we'll just do the IP of the machine to type out the full name and then we'll just do just DC and TLM so this should yeah this should get us all the password hashes for every user account in the domain and at this point we could do what we did in the DC sync video where you just take this out - traitor password hash need it pass the hash attack that's the easiest way obviously if somebody figured out that you've done this they could just remove these permissions or change the administrator password and then you can no longer do that attack whereas with this attack it's much more persistent much more likely to survive for a long time so what we're gonna do here is take the krbtgt account take is nt password hash which is that bit at the end there and if we go to mini cats and we wanna run which X 64 story and we were on many cats PXE okay this little console and there's loads of features in this tool but we're just going to run the Kerberos golden attack and I can't remember all of the parameters that you want so as far as I can see there isn't a way to get any kind of help text for each command in the tool itself which is always annoying and if we just googled mini cat's Kerberos and we look at the wiki we can see which arguments is expecting so one slash domain so that's easy that is just our domain name and then we want Sid and this is the SID of the domain so if you have like a remote shell you know however how have you managed to get to this point with these credentials you've presumably got access in some ways the domain so you can easily just get the domain set by just getting the seed of any user account and then just stripping the last part off of it so just to simulate that I'm just gonna switch over to natural domain machine obviously wouldn't normally do it like this you'd have remote shell running or whatever and then but we'll just do who Li /all and that will give us a SID of the current user account and we can just strip the last part off and then we get the domain set so you said paste that in slash user so we're going to impersonate the administrator account and then slash ID is optional we don't need that such groups is optional and then we just need to specify the ntlm hash with this ki VT DT flat so would care be T DT and then paste in this hash that we got up here so this part here the N T hash paste that in and I'm also going to do such PT t because if you don't do that this will just get saved to a file this ticket that it creates and if you do slash PTT it will just associate it with our logon session so for example right now if I just run the built-in Windows tool to list Kerberos tickets K list we have 0 tickets but after running this we run that again we've now got this Co bus ticket associated with our logon session so what that means in Windows at least I don't know how it works on Linux if you have to save it as a file and then specify it with certain commands but on windows that means that if we try and access say n SMB share or anything on this remote server as long as we do it in a way that supports Kerberos authentication which I'll talk about in a second it will automatically use this Kerberos ticket that we've got here so we're going to specify anything so let's test that theory let's do not use to map a network drive and we'll say we want to go to the remote machine go to the C dollars yet obviously only administrator Kaname access to C dollar share so if we were doing this normally from an on domain machine like this it would just fail that says denied but because we've got this Kerberos ticket it completes successfully we can go into the O dry we can list everything in the C Drive we've got full admin access so that's a demonstration of the attack and now it's quick look at exactly how and why it works and also I'll just touch on what I mentioned before when I said this'll only work if you do it in a way that supports Kerberos authentication if we had tried to go to the IP address here instead of the name it wouldn't work it would fall back to ntlm authentication and the Kerberos ticket would not get used so you have to use the full machine name with some services you can just use the first part of the machine name just the machine in its own some of them though you're going to need to do a fully qualified domain name like this so it's safer to just always do the fully qualified domain name and then you can be fairly certain that it's going to be using Kerberos authentication also I've just logged off and log back on just to clear all the associated Kerberos tickets you can't in theory do Kahless to purge but it didn't seem to work it still was using the old ticket but now that we've logged off my back on we tried to run that exact same command we go to as DC 1 SC around local C dollar now we get prompted for you name whereas we didn't before just automatically used the admin ticket that we had so let's fire up Wireshark and then we can quickly see exactly what's going on here see if we run that normally we get to this point where it's just trying to log on it's just that fast be - as you can see we're doing negotiate request and then it just tries to authenticate as my current user account which is just this workstation HT BC is the name of the user account and obviously that will fail it you can't log on because that's not a domain account and it doesn't have any kind of permissions it's fire mimikatz again and interestingly this first part where we actually create the the golden ticket doesn't seem to do any kind of network communication at all you can just type any old junk in there and it will create the ticket for you it's just that if you actually tried to use that it wouldn't work so we've got our ticket created again and you'll notice that it's actually set to expire in ten years time so that's why this is kind of called a golden ticket because it lets you impersonate anyone and it lasts for years I mean you can set it to last for even longer if you want to but yeah that's why it's a golden ticket because it just lets you do absolutely everything but why exactly does it work why does getting the krbtgt account password hash mean that we can now impersonate any user on the debate and that doesn't really make a lot of sense so let's look at exactly what's going on here now if we fire up Wireshark and we'll do a network drive again to this same service and it uses the ticket that we've got and we'll run Wireshark while we do that so complete successfully and if you filter this for us and me too actually that's filtered for Kerberos be easier to kind of follow it along now you might remember in previous videos when we looked at some Kerberos stuff it starts off with an AAS request and then we get an AAS response back on AS rep and that was some of the stuff we were looking at attacking previously but here we're jumping straight to the next part of the whole Kerberos authentication dance which is this TGS request and TDS response so the first part with the a s request in response that gets you what's called the TGT ticket granting ticket and then you can use that to then request a TGS for any service that you're trying to access so an example of a service and the one that we're using in this case would be a file share it could be something else like SQL or whatever anything that supports Kerberos authentication in this case it's just an SMB share so if we look in the request we will see somewhere in here the service that we're trying to access is CIFS which is I can't remember what sounds lost on my head but is basically file-share service and then dc1 is the server that's hosting that service so again like this CIFS here instead of a file share service that this is could be anything to support Kerberos authentication as long as it matches what's setting the service principal name for the account but again that's kind of beyond the scope of this topic anyway why does all this matter why does all of this mean that when we have the anti LEM hash for the krbtgt account that we can just do whatever we want it's pretty really shortly and concisely the reason is the Kerberos tickets are encrypted with that password hash so the ntlm hash of the care bt GT account is used to encrypt part of this I believe it's this part here there are some other encrypted parts famously an encrypted part here but they get encrypted with different things so you remember from the previous videos we've done looking at Kerberos one of these parts gets encrypted with the users password hash which is why we were able to get user password hashes from the authentication request so that was in the first part the a s request an a s response they have parts of them that encrypted with the users password whereas here this will be encrypted with I believe this part he'll be encrypted with the machine account password so in this case it'll be the DC one machine account computer account in Active Directory that accounts password which is just a really long random also generated password that gets changed every 30 days that will be used to encrypt this section here but this top-level part this encrypted part here which I believe acts as kinda like a checksum for the entire ticket and there might be some other data in there I can't remember from looking at the Kerberos spec exactly what's in here but this part gets encrypted with the krbtgt account password well it's password hash which luckily for us is what we have we don't have its password and trying to find its password would be very very difficult but getting the password hash it's not quite so difficult so if we've got the password hash we can with the help of mini katz a program that understands all the format of everything that needs to be in here we can just create a ticket that says whatever we want and because we've used that password hash to encrypt this part it will here completely valid to the domain so that's kind of the short summary and I could go more into how Kerberos works in terms of tgs's and TZ T's and stuff but I think for this video let's just kind of leave it at that the reason it works is because we've got the kind of master key that is used to encrypt stuff and kind of prove that it's being authenticated by the Kerberos central database and central service KDC when we forge a ticket and we can encrypt this part with that hash it basically proves to every machine that we talk to into the KDC and everything that that is a legitimate ticket so what we can do with that is just set the username to be anything we want so here we set it to administrator you can actually literally just make up a user account I'm just literally any name you want doesn't have to be one that even exists and because it'll have the right Sid you might remember in the mimikatz documentation somewhere it said which ID we could use so this Sid here we're specifying 500 which is the built in administrator account Sid and obviously permissions are all done based on Sid not username so you can specify whatever you want with the actual username because the only thing that's going to ever get checked is this ID here which we just specify it 500 so it's always going to think we are the administrator account and it's also specifying some group SIDS here or relative IDs the end of a Sid so this will be like the domain admins group the enterprise that means group stuff like that and just to make sure you're definitely gonna have access to absolutely everything which is why again it's called a golden ticket because it just gives you everything you could ever want as an attacker obviously it's pretty hard to actually get to this point and again we could just actually use the administrators hash and do it pass the hash attack if we've got to the point where we can get the hash for the krbtgt account so it's not an easy thing to do in a normal domain but if you have found some way to get hashes for any account in the domain then you can do this and get much more persistent long-term foothold I guess you call it I should point out as well that if you were to try and do this all on the right machine which was my mistake the first time I ever tried to do this I have to say pretend this was a remote shell that we're running on the domain controller or on any server on the domain if we tried to create a golden ticket there and store it with the session when we tried to actually access anything it wouldn't work because Kerberos authentication wouldn't get used like when you're just accessing local files there's no code authentication going on there even if you tried to do like net use that we did before like that and even if you just did localhost and then the seed or it still wouldn't work it's windows is smart enough to realize that that is the same machine I'm currently running on so we don't need to do any kind of Kerberos authentication so you always need to do this part the actual creation of the golden ticket storing it with your session and accessing the server you always need to do that remotely so that Kerberos authentication actually has to get used so hope that explains it and I feel like I probably should have got a little bit more in depth with this stuff but it would take quite a while to explain how Kerberos works in general I don't wanna kind of overload you with loads of terms cuz I know a lot of this stuff TG T's and TDs and IAS requests and all that stuff does get a bit much when you're not too familiar with it and I'm still learning about it I'm not gonna pretend I'm not salute expert on this stuff I'm still figuring things out as well so I'll probably do some more research on Kerberos make sure I get a better handle of it myself and then I'll put together like a general Kerberos explanation slash tutorial I guess of how it works but yeah that will do for this video hope you found some of it interesting and I will see you in the next one
Show moreFrequently asked questions
How can I eSign a contract?
How can I send a contract via email with an electronic signature attached?
What makes an electronic signature legally binding?
Get more for signed Golden Ticket made easy
- Print signature service Professional Birthday Party Invitation
- Prove electronically signing Event Catering Proposal Template
- Endorse digi-sign Rent to Own Agreement Template
- Authorize signature service Sales Contract
- Anneal signatory Catering Proposal
- Justify eSignature Pet Care Agreement
- Try initial Freelance Writing Proposal Template
- Add Administration Agreement signature
- Send Technical Proposal Template email signature
- Fax Simple Receipt signatory
- Seal Behavioral Assessment electronically signed
- Password Lease byline
- Pass Newborn Photography Contract Template esigning
- Renew Affidavit of Domicile signature block
- Test Basketball Camp Registration signature service
- Require Commercial Lease Agreement Template countersign
- Comment visitor eSignature
- Boost teller eSign
- Compel guy initials
- Void Weekly Timesheet Template template countersignature
- Adopt protocol template digital signature
- Vouch Construction Invoice template electronically signed
- Establish Rail Ticket Booking template digi-sign
- Clear Royalty Agreement Template template esign
- Complete Software Development Progress Report template signature block
- Force Solar Panel Installation Proposal Template template initial
- Permit Graphic Design Order template signature
- Customize Commercial Photography Contract Template template email signature