Erase eSignature Presentation Safe
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






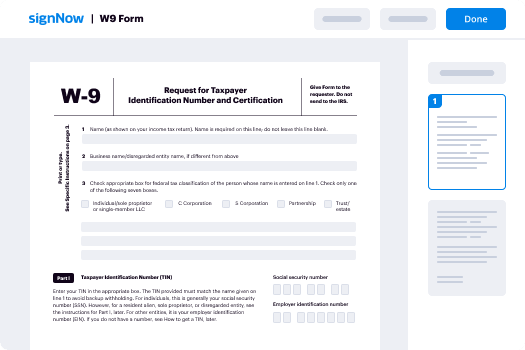
Remove eSignature presentation safety
In the current rapid-paced corporate landscape, optimizing document signing workflows is crucial. With airSlate SignNow, you can effortlessly eliminate the inconveniences of conventional signatures and substitute them with secure eSignatures. This manual will guide you through the effective use of airSlate SignNow to improve your document handling and signing procedures.
Steps to remove eSignature presentation safety with airSlate SignNow
- Launch your web browser and go to the airSlate SignNow homepage.
- Register for an account with a complimentary trial or log in if you already possess one.
- Upload the document you want to sign or send for others to sign.
- If you intend to reuse the document, transform it into a reusable template.
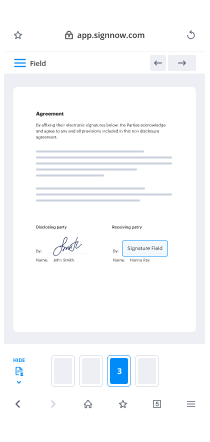
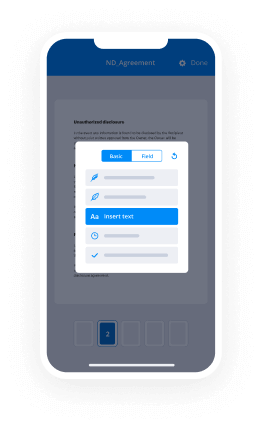
- Access your file to implement necessary modifications: add fillable fields or additional details.
- Sign the document and assign signature fields for your recipients.
- Click on 'Continue' to set up and dispatch an eSignature invitation.
By adhering to these steps, you can effectively oversee your document signing requirements with airSlate SignNow. This platform not only streamlines the signing process but also boosts document security and accessibility.
Eager to revolutionize your document workflow? Begin your free trial of airSlate SignNow today and discover the advantages of a user-friendly eSignature solution that delivers excellent value, clear pricing, and outstanding support!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is the Erase eSignature Presentation Safe feature in airSlate SignNow?
The Erase eSignature Presentation Safe feature in airSlate SignNow allows users to securely manage and remove electronic signatures from documents. This ensures that sensitive information is protected while maintaining compliance with legal standards. With this feature, businesses can confidently manage their documents without the fear of unauthorized access.
-
How does the Erase eSignature Presentation Safe enhance document security?
The Erase eSignature Presentation Safe enhances document security by providing a reliable method to remove signatures from sensitive documents. This feature ensures that once a signature is erased, the document cannot be tampered with, thus preserving the integrity of the original content. Businesses can trust that their data remains protected through this robust security measure.
-
Is the Erase eSignature Presentation Safe easy to use?
Yes, the Erase eSignature Presentation Safe is designed for ease of use. airSlate SignNow provides an intuitive interface that simplifies the process of erasing electronic signatures. Users can navigate the platform with minimal training, making it accessible for everyone in your organization.
-
What are the pricing options for using the Erase eSignature Presentation Safe?
airSlate SignNow offers flexible pricing plans that cater to different business needs while including the Erase eSignature Presentation Safe feature. Users can choose from monthly or annual subscriptions, allowing businesses of all sizes to benefit from this cost-effective solution. For detailed pricing information, visit our website or contact our sales team.
-
Can the Erase eSignature Presentation Safe integrate with other software?
Yes, the Erase eSignature Presentation Safe seamlessly integrates with various business applications, enhancing workflow efficiency. airSlate SignNow supports integrations with popular tools like Google Drive, Dropbox, and Salesforce. This allows users to manage their documents across different platforms without hassle.
-
What are the benefits of using the Erase eSignature Presentation Safe?
The Erase eSignature Presentation Safe provides numerous benefits, including enhanced security, compliance with legal regulations, and improved document management. By allowing users to confidently erase signatures, businesses can ensure that their documentation remains secure and compliant with industry standards. This ultimately saves time and reduces the risk of legal complications.
-
Is customer support available for issues with the Erase eSignature Presentation Safe?
Absolutely! airSlate SignNow offers dedicated customer support to assist users with any issues related to the Erase eSignature Presentation Safe. Our support team is available through various channels, including live chat and email, ensuring that you receive prompt assistance whenever needed.
-
What is a registered exporter system (REX)?
In Simple Words REX is Compliance system initiated by European union for Certification of Origin.If one wants to export goods value exceeds 6000 EUR to Europe then has to attach this certificate with consignment.In Official Frame of words:Subject: – Certification of Origin of Goods for European Union Generalised System of Preferences (EU-GSP) – Modification of the system as of 1 January 2017.In exercise of powers conferred under paragraph 2.04 of the Foreign Trade Policy, 2015-2020, the Director General of Foreign Trade hereby inserts a new sub para (c) under Para 2.104 Generalised System o...
-
What started the Trojan horse?
1971The Creeper system, an experimental self-replicating program, is written by Bob Thomas at BBN Technologies to test John von Neumann's theory. Creeper infected DEC PDP-10 computers running the TENEX operating system. Creeper gained access via the ARPANET and copied itself to the remote system where the message "I'm the creeper, catch me if you can!" was displayed. The Reaper program was later created to delete Creeper.1973In fiction, the 1973 Michael Crichton movie Westworld made an early mention of the concept of a computer virus, being a central plot theme that causes androids to run amok. Alan Oppenheimer's character summarizes the problem by stating that "...there's a clear pattern here which suggests an analogy to an infectious disease process, spreading from one...area to the next." To which the replies are stated: "Perhaps there are superficial similarities to disease" and, "I must confess I find it difficult to believe in a disease of machinery." (Crichton's earlier work, the 1969 novel The Andromeda Strain and 1971 film were about an extraterrestrial biological virus-like disease that threatened the human race.)1974The Rabbit (or Wabbit) virus, more a fork bomb than a virus, is written. The Rabbit virus makes multiple copies of itself on a single computer (and was named "Rabbit" for the speed at which it did so) until it clogs the system, reducing system performance, before finally signNowing a threshold and crashing the computer.1975April: ANIMAL is written by John Walker for the UNIVAC 1108. ANIMAL asked a number of questions of the user in an attempt to guess the type of animal that the user was thinking of, while the related program PERVADE would create a copy of itself and ANIMAL in every directory to which the current user had access. It spread across the multi-user UNIVACs when users with overlapping permissions discovered the game, and to other computers when tapes were shared. The program was carefully written to avoid damage to existing file or directory structures, and not to copy itself if permissions did not exist or if damage could result. Its spread was therefore halted by an OS upgrade which changed the format of the file status tables that PERVADE used for safe copying. Though non-malicious, "Pervading Animal" represents the first Trojan "in the wild".The novel The Shockwave Rider by John Brunner is published, coining the word "worm" to describe a program that propagates itself through a computer network.1981–19891981A program called Elk Cloner, written for Apple II systems, was created by Richard Skrenta. The Apple II was seen[by whom?] as particularly vulnerable due to the storage of its operating system[clarification needed] on floppy disk. Elk Cloner's design combined with public ignorance[not in citation given] about what malware was and how to protect against it led to Elk Cloner being responsible for the first large-scale[not in citation given] computer virus outbreak in history.1983November: The term 'virus' is coined by Frederick Cohen in describing self-replicating computer programs. In 1984 Cohen uses the phrase "computer virus" – as suggested by his teacher Leonard Adleman – to describe the operation of such programs in terms of "infection". He defines a 'virus' as "a program that can 'infect' other programs by modifying them to include a possibly evolved copy of itself." Cohen demonstrates a virus-like program on a VAX11/750 system at Lehigh University. The program could install itself in, or infect, other system objects.1984August: Ken Thompson publishes his seminal paper, Reflections on Trusting Trust, in which he describes how he modified a C compiler so that when used to compile a specific version of the Unix operating system, it inserted a backdoor into the login command, and when used to compile itself, it inserted the backdoor insertion code, even if neither the backdoor nor the backdoor insertion code were present in the source code.1986January: The Brain boot sector virus is released. Brain is considered the first IBM PC compatible virus, and the program responsible for the first IBM PC compatible virus epidemic. The virus is also known as Lahore, Pakistani, Pakistani Brain, and Pakistani flu as it was created in Lahore, Pakistan by 19-year-old Pakistani programmer, Basit Farooq Alvi, and his brother, Amjad Farooq Alvi.December: Ralf Burger presented the Virdem model of programs at a meeting of the underground Chaos Computer Club in Germany. The Virdem model represented the first programs that could replicate themselves via addition of their code to executable DOS files in COM format.1987Appearance of the Vienna virus, which was subsequently neutralized—the first time this had happened on the IBM platform.Appearance of Lehigh virus (discovered at its namesake university), boot sector viruses such as Yale from USA, Stoned from New Zealand, Ping Pong from Italy, and appearance of first self-encrypting file virus, Cascade. Lehigh was stopped on campus before it spread to the wild, and has never been found elsewhere as a result. A subsequent infection of Cascade in the offices of IBM Belgium led to IBM responding with its own antivirus product development. Prior to this, antivirus solutions developed at IBM were intended for staff use only.October: The Jerusalem virus, part of the (at that time unknown) Suriv family, is detected in the city of Jerusalem. The virus destroys all executable files on infected machines upon every occurrence of Friday the 13th (except Friday 13 November 1987 making its first trigger date May 13, 1988). Jerusalem caused a worldwide epidemic in 1988.November: The SCA virus, a boot sector virus for Amiga computers appear, immediately creating a pandemic virus-writer storm. A short time later, SCA releases another, considerably more destructive virus, the Byte Bandit.December: Christmas Tree EXEC was the first widely disruptive replicating network program, which paralyzed several international computer networks in December 1987. It was written in Rexx on the VM/CMS operating system and originated in what was then West Germany. It re-emerged in 1990.1988March 1: The Ping-Pong virus (also called Boot, Bouncing Ball, Bouncing Dot, Italian, Italian-A or VeraCruz), an MS-DOS boot sector virus, is discovered at the University of Turin in Italy.June: The CyberAIDS and Festering Hate Apple ProDOS viruses spreads from underground pirate BBS systems and starts infecting mainstream networks. Festering Hate was the last iteration of the CyberAIDS series extending back to 1985 and 1986. Unlike the few Apple viruses that had come before which were essentially annoying, but did no damage, the Festering Hate series of viruses was extremely destructive, spreading to all system files it could find on the host computer (hard drive, floppy, and system memory) and then destroying everything when it could no longer find any uninfected files.November 2: The Morris worm, created by Robert Tappan Morris, infects DEC VAX and Sun machines running BSD UNIX that are connected to the Internet, and becomes the first worm to spread extensively "in the wild", and one of the first well-known programs exploiting buffer overrun vulnerabilities.1989October: Ghostball, the first multipartite virus, is discovered by Friðrik Skúlason. It infects both executable .COM-files and boot sectors on MS-DOS systems.December: Several thousand floppy disks containing the AIDS Trojan, the first known ransomware, are mailed to subscribers of PC Business World magazine and a WHO AIDS conference mailing list. This DOS Trojan lies dormant for 90 boot cycles, then encrypts all filenames on the system, displaying a notice asking for $189 to be sent to a post office box in Panama in order to receive a decryption program.1990–19991990Mark Washburn, working on an analysis of the Vienna and Cascade viruses with Ralf Burger, develops the first family of polymorphic viruses, the Chameleon family. Chameleon series debuted with the release of 1260.June: The Form computer virus is isolated in Switzerland. It would remain in the wild for almost 20 years and reappear afterwards; during the 1990s it tended to be the most common virus in the wild with 20 to more than 50 per cent of reported infections.1992March: The Michelangelo virus was expected to create a digital apocalypse on March 6, with millions of computers having their information wiped, according to mass media hysteria surrounding the virus. Later assessments of the damage showed the aftermath to be minimal. John McAfee had been quoted by the media as saying that 5 million computers would be affected. He later said that, pressed by the interviewer to come up with a number, he had estimated a range from 5 thousand to 5 million, but the media naturally went with just the higher number.1993"Leandro" or "Leandro & Kelly" and "Freddy Krueger" spread quickly due to popularity of BBS and shareware distribution.1994April: OneHalf is a DOS-based polymorphic computer virus.1995The first Macro virus, called "Concept", is created. It attacked Microsoft Word documents.1996"Ply" — DOS 16-bit based complicated polymorphic virus appeared with built-in permutation engine.Boza, the first virus designed specifically for Windows 95 files arrives.Laroux, the first Excel macro virus appears.Staog, the first Linux virus attacks Linux machines1998June 2: The first version of the CIH virus appears. It is the first known virus able to erase flash ROM BIOS content.1999January 20: The Happy99 worm first appeared. It invisibly attaches itself to emails, displays fireworks to hide the changes being made, and wishes the user a happy New Year. It modifies system files related to Outlook Express and Internet Explorer (IE) on Windows 95 and Windows 98.March 26: The Melissa worm was released, targeting Microsoft Word and Outlook-based systems, and creating considerable network traffic.June 6: The ExploreZip worm, which destroys Microsoft Office documents, was first detected.December 30: The Kak worm is a JavaScript computer worm that spread itself by exploiting a bug in Outlook Express.2000–20092000May 5: The ILOVEYOU worm, also known as Love Letter, or VBS, or Love Bug worm, is a computer worm purportedly created by a Filipino computer science student. Written in VBScript, it infected millions of Windows computers worldwide within a few hours of its release. Using social engineering techniques, it is considered to be one of the most damaging worms ever.June 28: The Pikachu virus is believed to be the first computer virus geared at children. It contains the character "Pikachu" from the Pokémon series, and is in the form of an e-mail titled "Pikachu Pokemon" with the message: "Pikachu is your friend." The attachment to the email has "an image of a pensive Pikachu", along with a message stating, "Between millions of people around the world I found you. Don’t forget to remember this day every time MY FRIEND." Along with the image, there is a program, written in Visual Basic 6, called "pikachupokemon.exe" that modifies the AUTOEXEC.BAT file and adds a command for removing the contents of directories C:\Windows and C:\Windows\System at computer's restart. However, a message would appear during startup, asking the user if they would like to delete the contents of those folders. This is because the author, instead of writing the lines “del C:\WINDOWS\*.* /y” and “del C:\WINDOWS\SYSTEM\*.* /y” to AUTOEXEC.BAT, the author did not include the /y switches, which would have automatically chosen the yes option. The operating systems affected by this worm are Windows 95, Windows 98, and Windows ME.2001February 11: The Anna Kournikova virus hits e-mail servers hard by sending e-mail to contacts in the Microsoft Outlook addressbook. Its creator, Jan de Wit, was sentenced to 150 hours of community service.May 8: The Sadmind worm spreads by exploiting holes in both Sun Solaris and Microsoft IIS.July: The Sircam worm is released, spreading through Microsoft systems via e-mail and unprotected network shares.July 13: The Code Red worm attacking the Index Server ISAPI Extension in Microsoft Internet Information Services is released.August 4: A complete re-write of the Code Red worm, Code Red II begins aggressively spreading onto Microsoft systems, primarily in China.September 18: The Nimda worm is discovered and spreads through a variety of means including vulnerabilities in Microsoft Windows and backdoors left by Code Red II and Sadmind worm.October 26: The Klez worm is first identified. It exploits a vulnerability in Microsoft Internet Explorer and Microsoft Outlook and Outlook Express.2002February 11: The Simile virus is a metamorphic computer virus written in assembly.Beast is a Windows-based backdoor Trojan horse, more commonly known as a RAT (Remote Administration Tool). It is capable of infecting almost all versions of Windows. Written in Delphi and released first by its author Tataye in 2002, its most current version was released October 3, 2004March 7: Mylife is a computer worm that spread itself by sending malicious emails to all the contacts in Microsoft Outlook.2003January 24: The SQL Slammer worm, aka Sapphire worm, Helkern and other names, attacks vulnerabilities in Microsoft SQL Server and MSDE becomes the fastest spreading worm of all time (measured by doubling time at the peak rate of growth), causing massive Internet access disruptions worldwide just fifteen minutes after infecting its first victim.April 2: Graybird is a trojan horse also known as Backdoor.Graybird.[28]June 13: ProRat is a Turkish-made Microsoft Windows based backdoor trojan horse, more commonly known as a RAT (Remote Administration Tool).August 12: The Blaster worm, aka the Lovesan worm, rapidly spreads by exploiting a vulnerability in system services present on Windows computers.August 18: The Welchia (Nachi) worm is discovered. The worm tries to remove the blaster worm and patch Windows.August 19: The Sobig worm (technically the Sobig.F worm) spreads rapidly through Microsoft systems via mail and network shares.September 18: Swen is a computer worm written in C++.October 24: The Sober worm is first seen on Microsoft systems and maintains its presence until 2005 with many new variants. The simultaneous attacks on network weakpoints by the Blaster and Sobig worms cause massive damage.November 10: Agobot is a computer worm that can spread itself by exploiting vulnerabilities on Microsoft Windows. Some of the vulnerabilities are MS03-026 and MS05-039.November 20: Bolgimo is a computer worm that spread itself by exploiting a buffer overflow vulnerability at Microsoft Windows DCOM RPC Interface.2004January 18: Bagle is a mass-mailing worm affecting all versions of Microsoft Windows. There were 2 variants of Bagle worm, Bagle.A and Bagle.B. Bagle.B was discovered on February 17, 2004.Late January: The MyDoom worm emerges, and currently holds the record for the fastest-spreading mass mailer worm. The worm was most notable for performing a distributed denial-of-service (DDoS) attack on Xinuos | Home, which belonged to The SCO Group.February 16: The Netsky worm is discovered. The worm spreads by email and by copying itself to folders on the local hard drive as well as on mapped network drives if available. Many variants of the Netsky worm appeared.March 19: The Witty worm is a record-breaking worm in many regards. It exploited holes in several Internet Security Systems (ISS) products. It was the fastest disclosure to worm, it was the first internet worm to carry a destructive payload and it spread rapidly using a pre-populated list of ground-zero hosts.May 1: The Sasser worm emerges by exploiting a vulnerability in the Microsoft Windows LSASS service and causes problems in networks, while removing MyDoom and Bagle variants, even interrupting business.June 15: Caribe or Cabir is a computer worm that is designed to infect mobile phones that run Symbian OS. It is the first computer worm that can infect mobile phones. It spread itself through Bluetooth. More information can be found on F-Secure[33] and Symantec.August 16: Nuclear RAT (short for Nuclear Remote Administration Tool) is a backdoor trojan that infects Windows NT family systems (Windows 2000, Windows XP, Windows 2003).August 20: Vundo, or the Vundo Trojan (also known as Virtumonde or Virtumondo and sometimes referred to as MS Juan) is a trojan known to cause popups and advertising for rogue antispyware programs, and sporadically other misbehaviour including performance degradation and denial of service with some websites including Google and Facebook.October 12: Bifrost, also known as Bifrose, is a backdoor trojan which can infect Windows 95 through Vista. Bifrost uses the typical server, server builder, and client backdoor program configuration to allow a remote attack.December: Santy, the first known "webworm" is launched. It exploited a vulnerability in phpBB and used Google in order to find new targets. It infected around 40000 sites before Google filtered the search query used by the worm, preventing it from spreading.2005August 2005: ZotobOctober 2005: The copy protection rootkit deliberately and surreptitiously included on music CDs sold by Sony BMG is exposed. The rootkit creates vulnerabilities on affected computers, making them susceptible to infection by worms and viruses.Late 2005: The Zlob Trojan, is a Trojan horse program that masquerades as a required video codec in the form of the Microsoft Windows ActiveX component. It was first detected in late 2005.2006January 20: The Nyxem worm was discovered. It spread by mass-mailing. Its payload, which activates on the third of every month, starting on February 3, attempts to disable security-related and file sharing software, and destroy files of certain types, such as Microsoft Office files.February 16: discovery of the first-ever malware for Mac OS X, a low-threat trojan-horse known as OSX/Leap-A or OSX/Oompa-A, is announced.Late March: Brontok variant N was found in late March. Brontok was a mass-email worm and the origin for the worm was from Indonesia.June: Starbucks is a virus that infects StarOffice and OpenOffice.Late September: Stration or Warezov worm first discovered.2007January 17: Storm Worm identified as a fast spreading email spamming threat to Microsoft systems. It begins gathering infected computers into the Storm botnet. By around June 30 it had infected 1.7 million computers, and it had compromised between 1 and 10 million computers by September.[40] Thought to have originated from Russia, it disguises itself as a news email containing a film about bogus news stories asking you to download the attachment which it claims is a film.July: Zeus is a trojan that targets Microsoft Windows to steal banking information by keystroke logging.2008February 17: Mocmex is a trojan, which was found in a digital photo frame in February 2008. It was the first serious computer virus on a digital photo frame. The virus was traced back to a group in China.March 3: Torpig, also known as Sinowal and Mebroot, is a Trojan horse that affects Windows, turning off anti-virus applications. It allows others to access the computer, modifies data, steals confidential information (such as user passwords and other sensitive data) and installs more malware on the victim's computer.May 6: Rustock.C, a hitherto-rumoured spambot-type malware with advanced rootkit capabilities, was announced to have been detected on Microsoft systems and analyzed, having been in the wild and undetected since October 2007 at the very least.July 6: Bohmini.A is a configurable remote access tool or trojan that exploits security flaws in signNow Flash 9.0.115 with Internet Explorer 7.0 and Firefox 2.0 under Windows XP SP2.July 31: The Koobface computer worm targets users of Facebook and Myspace. New variants constantly appear.November 21: Computer worm Conficker infects anywhere from 9 to 15 million Microsoft server systems running everything from Windows 2000 to the Windows 7 Beta. The French Navy, UK Ministry of Defence (including Royal Navy warships and submarines), Sheffield Hospital network,[48] German Bundeswehr, and Norwegian Police were all affected. Microsoft sets a bounty of US$250,000 for information leading to the capture of the worm's author(s). Five main variants of the Conficker worm are known and have been dubbed Conficker A, B, C, D and E. They were discovered 21 November 2008, 29 December 2008, 20 February 2009, 4 March 2009 and 7 April 2009, respectively. On December 16, 2008, Microsoft releases KB958644 patching the server service vulnerability responsible for the spread of Conficker.2009July 4: The July 2009 cyber attacks occur and the emergence of the W32.Dozer attack the United States and South Korea.July 15: Symantec discovered Daprosy Worm. Said trojan worm is intended to steal online-game passwords in internet cafes. It could, in fact, intercept all keystrokes and send them to its author which makes it potentially a very dangerous worm to infect B2B (business-to-business) systems.August 24: Source code for MegaPanzer is released by its author under GPLv3. and appears to have been apparently detected in the wild.2010–present2010January: The Waledac botnet sent spam emails. In February 2010, an international group of security researchers and Microsoft took Waledac down.January: The Psyb0t worm is discovered. It is thought to be unique in that it can infect routers and high-speed modems.February 18: Microsoft announced that a BSoD problem on some Windows machines which was triggered by a batch of Patch Tuesday updates was caused by the Alureon Trojan.June 17: Stuxnet, a Windows Trojan, was detected. It is the first worm to attack SCADA systems. There are suggestions that it was designed to target Iranian nuclear facilities. It uses a valid certificate from Realtek.September 9: The virus, called "here you have" or "VBMania", is a simple Trojan horse that arrives in the inbox with the odd-but-suggestive subject line "here you have". The body reads "This is The Document I told you about, you can find it Here" or "This is The Free Download Sex Movies, you can find it Here".September 15: The virus called Kenzero is a virus that spreads online from Peer to peer (P2P) sites taking browsing history.2011SpyEye and Zeus merged code is seen. New variants attack mobile phone banking information.Anti-Spyware 2011, a Trojan horse that attacks Windows 9x, 2000, XP, Vista, and Windows 7, posing as an anti-spyware program. It actually disables security-related process of anti-virus programs, while also blocking access to the Internet, which prevents updates.Summer 2011: The Morto worm attempts to propagate itself to additional computers via the Microsoft Windows Remote Desktop Protocol (RDP). Morto spreads by forcing infected systems to scan for Windows servers allowing RDP login. Once Morto finds an RDP-accessible system, it attempts to log into a domain or local system account named 'Administrator' using a number of common passwords.[65] A detailed overview of how the worm works—along with the password dictionary Morto uses—was done by Imperva.July 13: the ZeroAccess rootkit (also known as Sirefef or max++) was discovered.September 1: Duqu is a worm thought to be related to the Stuxnet worm. The Laboratory of Cryptography and System Security (CrySyS Lab)[67] of the Budapest University of Technology and Economics in Hungary discovered the threat, analysed the malware, and wrote a 60-page report naming the threat Duqu. Duqu gets its name from the prefix "~DQ" it gives to the names of files it creates.2012May: Flame – also known as Flamer, sKyWIper, and Skywiper – a modular computer malware that attacks computers running Microsoft Windows. Used for targeted cyber espionage in Middle Eastern countries. Its discovery was announced on 28 May 2012 by MAHER Center of Iranian National Computer Emergency Response Team (CERT), Kaspersky Lab and CrySyS Lab of the Budapest University of Technology and Economics. CrySyS stated in their report that "sKyWIper is certainly the most sophisticated malware we encountered during our practice; arguably, it is the most complex malware ever found".August 16: Shamoon is a computer virus designed to target computers running Microsoft Windows in the energy sector. Symantec, Kaspersky Lab, and Seculert announced its discovery on August 16, 2012.September 20: NGRBot is a worm that uses the IRC network for file transfer, sending and receiving commands between zombie network machines and the attacker's IRC server, and monitoring and controlling network connectivity and intercept. It employs a user-mode rootkit technique to hide and steal its victim's information. This family of bot is also designed to infect HTML pages with inline frames (iframes), causing redirections, blocking victims from getting updates from security/antimalware products, and killing those services. The bot is designed to connect via a predefined IRC channel and communicate with a remote botnet.2013September: The CryptoLocker Trojan horse is discovered. Cryptolocker encrypts the files on a user's hard drive, then prompts them to pay a ransom to the developer in order to receive the decryption key. In the following months, a number of copycat ransomware Trojans are also discovered.December: The Gameover ZeuS Trojan is discovered. This type of virus steals one's login details on popular Web sites that involve monetary transactions. It works by detecting a login page, then proceeds to inject a malicious code into the page, keystroke logging the computer user's details.December: Linux.Darlloz targets the Internet of things and infects routers, security cameras, set-top boxes by exploiting a PHP vulnerability.2014November: The Regin Trojan horse is discovered. Regin is a dropper that is primarily spread via spoofed Web pages. Once downloaded, Regin quietly downloads extensions of itself, making it difficult to be detected via anti-virus signatures. It is suspected to have been created by the United States and United Kingdom over a period of months or years, as a tool for espionage and mass surveillance.2015The BASHLITE malware is leaked leading to a massive spike in DDoS attacks.Linux.Wifatch is revealed to the general public. It is found to attempt to secure devices from other more malicious malware.2016February: Ransomware Locky with its over 60 derivatives spread throughout Europe and infected several million computers. At the height of the spread over five thousand computers per hour were infected in Germany alone. Although ransomware was not a new thing at the time, insufficient cyber security as well as a lack of standards in IT was responsible for the high number of infections. Unfortunately even up to date antivirus and internet security software was unable to protect systems from early versions of Locky.February: Tiny Banker Trojan (Tinba) makes headlines. Since its discovery, it has been found to have infected more than two dozen major banking institutions in the United States, including TD Bank, Chase, HSBC, Wells Fargo, PNC and Bank of America. Tiny Banker Trojan uses HTTP injection to force the user's computer to believe that it is on the bank's website. This spoof page will look and function just as the real one. The user then enters their information to log on, at which point Tinba can launch the bank webpage's "incorrect login information" re [1] turn, and redirect the user to the real website. This is to trick the user into thinking they had entered the wrong information and proceed as normal, although now Tinba has captured the credentials and sent them to its host.September: Mirai creates headlines by launching some of the most powerful and disruptive DDoS attacks seen to date by infecting the Internet of Things. Mirai ends up being used in the DDoS attack on 20 September 2016 on the Krebs on Security site which signNowed 620 Gbit/s. Ars Technica also reported a 1 Tbit/s attack on French web host OVH. On 21 October 2016 multiple major DDoS attacks in DNS services of DNS service provider Dyn occurred using Mirai malware installed on a large number of IoT devices, resulting in the inaccessibility of several high-profile websites such as GitHub, Twitter, Reddit, Netflix, Airbnb and many others. The attribution of the attack to the Mirai botnet was originally reported by BackConnect Inc., a security firm.2017May: The WannaCry ransomware attack spreads globally. Exploits revealed in the NSA hacking toolkit leak of late 2016 were used to enable the propagation of the malware. Shortly after the news of the infections broke online, a UK cybersecurity researcher in collaboration with others found and activated a "kill switch" hidden within the ransomware, effectively halting the initial wave of its global propagation. The next day, researchers announced that they had found new variants of the malware without the kill switch.June: The Petya (malware) attack spreads globally affecting Windows systems. Researchers at Symantec reveal that this ransomware uses the EternalBlue exploit, similar to the one used in the WannaCry ransomware attack.September: The Xafecopy Trojan attack 47 countries affecting only Android operating systems. Kaspersky Lab identified it as a malware from the Ubsod family, stealing money through click based WAP billing systems.September: A new variety of RAT Trojan, Kedi RAT (Remote Access Trojan) distributed in a Spear Phishing Campaign. The attack targeted Citrix users. The Trojan was able to evade usual system scanners. Kedi Trojan has all characteristics of a common Remote Access Trojan and it could communicate to its Command and Control center via gmail using common HTML, HTTP protocols.2018??????????
-
What are the 20 most commonly used symbols in Christopher Nolan's films?
Recently I read an article in “ The sanity clause” , an online magazine about - “Christopher Nolan: Someone more than a man; a symbol”. Here it is-This is the first in my new series, 21st Century Masters, a collection of director profiles specifically on directors and their films from the year 2000 onward. With some exceptions, films made before 2000 are not the subject of these profiles. These are attempts to understand the legacy of filmmakers here and now, not of the past.There are three steps to Christopher Nolan’s directing process.He shows you something ordinary, which it probably isn’t.He takes the ordinary something and makes it do something extraordinary.But you wouldn’t clap yet, because he has to bring everything back.Conveniently, this is the same model Michael Caine explains in “The Prestige.” A good “magician,” he says, tries to do something new, but not everyone can. A good “magician” gives total devotion to his art.This is Chris Nolan in a nutshell. He begins with a film that demands your patience and attention, one that feels gritty, realistic and serious but has a little something more. Then, he astounds with monumental twists, stunning special effects, sweeping vistas and a screenplay that ever so slightly bends what’s possible. But Nolan’s real game is in showing you how its all done. He arranges elaborate procedures for his characters with strict rules and principles for them to follow. Then they’re confined to boxy, talky and methodic scenes of dialogue to lay the exposition open for scrutiny.By doing this in each of his eight films, Nolan has been able to take over the world. No director in the 21st Century has emerged as a more distinctive, important voice for film as a popular art form than him. Other directors have been more critically acclaimed and others have slightly larger box office receipts, but no other director to make his or her mark in the last 12 years has come close to uniting adoring fanboys and appreciative film buffs than Nolan.Nolan’s films are about singular ideas. His legacy comes from getting modern audiences in the multiplex to obsess over their films, study them with scrupulous attention and adhere to them as important texts made to be discussed.Like Batman himself, Nolan is a symbol more than a director. He currently has the clout to take on any project he pleases and the fervent belief by many that he can do no wrong. And if through his audience he can transcend the idea that his film is just a movie made for entertainment value, he can become a beacon for something better than what we have in the movies today.“You take it away… to show them what they had.”“Following”Christopher Nolan began his fascination with filmmaking when he was just 8 years old in London. He shot films with action figures on Super 8 cameras and eventually started using his friends. But he never attended film school, and his early short films were low rent and surreal, most notably his 3-minute short “Doodlebug,” about a man obsessively chasing an insect around his house.He directed his first feature in 1998 about an unemployed writer who takes to following people simply for the sake of learning how they spend their day. The aptly titled “Following” was filmed for only £3000, used all non-actors and was directed, written, produced, shot and edited by Nolan himself.I always said that it’s hard to see how this indie, black and white neo-noir could ever come from the same guy who gave us one of the largest franchises in all of film history, but the core elements and traits that carry through all of Nolan’s films are all right here.“Following’s” protagonist Bill first lays down a set of rules for the audience to understand. He’s just fascinated, not sexually aroused or deeply disturbed. Don’t follow women into dark alleys at night, never follow the same person twice, and most importantly, don’t follow anyone that isn’t random.Every Nolan film is dictated by a complex scenario or a strange way for a character to behave, but it’s always boiled down into a strict method to the madness, usually explained directly to the audience in voice overs or monologues. Think Lenny’s fact-based tattoo system in “Memento,” the pseudo-science of “Inception’s” dream worlds or the aforementioned three-step procedure in “The Prestige.”Nolan loves doing this as a way of building suspense and surprise for the twist he surely has coming. In “Inception,” the film is so dense that we hang onto certain details, like the rules of The Kick or the sedative, that get in the way of more important ones like Cobb’s dark past. Like Cobb, we’re not supposed to be able to keep all our memories straight at once, and they come back to haunt us later.Here in “Following,” Bill’s rules are established such that they can be broken. He begins tailing a thief (not coincidentally also named Cobb) who also has his own unique game and set of rules. He breaks into people’s houses but doesn’t steal valuable items, only peace of mind. “Everybody has a box,” he says, the keepsakes that tell who a person are and what’s special to them. Cobb rifles through them and makes snap judgments about his marks. When one couple walks in on them invading their home, he calls the woman out for having an affair because of the way they reacted to their presence.This is all engaging discussion of human nature, but Bill and Cobb’s behavior is really just a plot device. It’s driven only for fascination and personal principles, not physical or moral motivation.“Doodlebug”Which brings us to our second point about Nolan’s filmmaking. Armond White pointed out in his review of “Inception” that Nolan’s characters have no morality. This is not necessarily a problem, as it’s hard to pin down the morality of many characters in the movies, such as in films by Bunuel and even some Kubrick and Hitchcock (who Nolan deeply admires). But it’s an important observation that guides nearly all of his work.In addition to having a set of rules, all Nolan characters have a fervent belief or philosophy. They act not out of being right or wrong but because they are motivated by this one idea that they hold deeply. We’ll delve into the specifics of each film later, but understanding this helps us to realize that Nolan’s films are not about emotions, or even characters really, but about behavior, ideologies and how those factors drive people to act.In “Following,” this voyeuristic fascination naturally gets Bill into trouble. But before that, Nolan has fun leaving us obvious visual clues that will return later, in this case an earring. He also leaves room for some sharp wit as Cobb jumps to hasty conclusions and coolly infects these livelihoods. It’s also engaging in black and white, something Nolan should definitely return to if given the opportunity.But Nolan cheats ever so slightly. SPOILER AHEAD! We have no reason to suspect that Cobb is actually scamming Bill along with the woman known only as The Blonde. And when the twist is revealed to us, it comes from an otherwise little seen policeman who tells us everything we know is wrong directly to our face and Bill’s. SPOILER DONE. It’s a twist not achieved through visual storytelling but more methodic dialogue.This is yet another troublesome trait of Nolan’s style. Initially, it seemed to be a mark of an amateur, someone who couldn’t tell his story through his camera and defaulted to his words. Now it seems to be a trend, and it’s something some critics still frown upon. But we begin to get a better sense of why he cheats the way he does in his follow up film, “Memento.”“There are things you know for sure.”The first shots in “Memento” take place in reverse. A hand holds a Polaroid snapshot that is developing backwards, with the image becoming less clear the longer we see it and the more he shakes it.This is Nolan telling us everything we need to know about “Memento” right in the first frame. We know the timeline is jumbled, we know we’ll be going back in time, and we even know things are going to get hazier the more we puzzle over it and the more he shakes things up.We know how this ends, and what we want to know is how we got here. Often in film, this is not the case. Even his characters seem unsure when Lenny wonders why his wife would read the same book over again.“I’m interested in making films to watch them a second time, and hopefully you’ll be interested to watch a second time,” Nolan said in a 2001 interview with Indiewire. “You don’t see how it’s stuck together; it actually can sustain that scrutiny and become something a little bit different when you see it again. Because I feel like I’ve got three years to work on this thing and as a viewer you’ve got like two hours to watch it, so it ought to be functioning at some level of greater sophistication than you can absorb in one viewing.”People often place “Memento” in the “mind-fuck” category. When it was first released, it was simultaneously a critical darling and a cult staple. It seemed to toy with our sense of space and time as well as our expectations, and yet Nolan admits himself that “Memento” is no more complicated than “Following.”The methodical system in “Memento” is two-fold. One is Lenny’s creepy tattoo system on his chest, arms and legs. The second is the film’s structure. It alternates between color and black and white and different moments in time. We’re confused because we usually associate black and white with a flashback, but here it’s obvious that’s not the case because the first shot of the current color sequence always matches up with the last shot of the next one.As Nolan says in the same Indiewire interview, this is actually an extremely linear film. But he gets that truth past us by immersing the audience in Lenny’s perspective. We hear internal voiceover constantly, we see his memory in color as though it were true, not in black and white like the story of Sammy Jankis, and our field of vision is restricted to his face and what he sees immediately in front of him.This is the start of Nolan’s most irritating trademark as a filmmaker. Nolan cannot, or more likely chooses not, to do more than close-ups when it comes to viewing his characters in conversation.“Memento” was the first film in which Nolan paired with his since permanent cinematographer Wally Pfister. Pfister’s style finds him rarely including more than one person in a shot at a given moment. Almost always in a Nolan film, if someone is talking, we see a close-up of the speaker alone. If he or she mentions an object or interacts with an object in some way, we’ll get a close-up of it. Think the beer coaster that Carrie Ann Moss slaps down in front of Lenny, or the dozens of individual photographs he carries with him. When he reads the line, “Don’t Believe His Lies,” he always reads it aloud too.He doesn’t do medium shots to allow his characters to breathe, he doesn’t have multiple people interacting together in the same frame, and he always keeps his camera steady, if not motionless during the shot. He’s capable of wide vistas that look impressive in IMAX, but these are set dressing, not back and forth exposition.Some critics have cited this very reason as why they’re disappointed with Nolan’s work. Not only are his films not visually engaging, trudging through lengthy dialogue sequences rather than tell the story visually, this approach can get confusing and clunky when it comes to Nolan photographing action.It appeared to be the mark of a rookie, someone who over time and a few more films would grow. But now eight films in, he’s only continued this approach if not mastered it. Nolan keeps our minds strictly focused on the character’s perspective so we can analyze their thought process and the story’s rules. Only later does he move away from the small screen to surprise us that we’re looking at a big one.What I admire then about “Memento” is how smart and self-aware it is. Everything Lenny says either tells us more about the themes (memory, how we lie to ourselves to survive) or it digs a deeper hole for him in this hapless predicament. Occasionally it’s actually hilarious, like Lenny drinking the beer with spit in it or earlier catching a gun that’s travelling backwards in time. At other times, we develop a sense of pathos for him, even if his actions don’t warrant it. “The world doesn’t just disappear,” Lenny says, but for him it does every few minutes. We’re sad that he lacks the context to love, make friends and grow. The end goal is really not the only thing that’s pulling us along in this story, and it is part of the reason Nolan devotes more time to the set-up than the payoff.The mental tropes Nolan was establishing here would follow him into every one of his films since. Unlike the socially awkward Bill in “Following,” Lenny was particularly disabled, even if his disability is also a plot device. All his characters carry a similar mental burden and similar rules, methods and principals. Bill was destroyed when he broke his rule. Lenny, and for that matter most of his characters again, were destroyed when they followed theirs.“Small things, remember?”“Insomnia”The cult success of “Memento” allowed Nolan free range to tackle a bigger, Hollywood studio production. That film was “Insomnia,” a remake of a Norwegian film and one he didn’t write the screenplay for. His previous film had the big name stars of Guy Pearce, Carrie Anne Moss and Joe Pantoliano, but never had Nolan worked with actors as high caliber as Al Pacino, Hilary Swank and Robin Williams.And yet “Insomnia” isn’t suddenly exacerbated in scope. It’s the story of a veteran L.A. detective who travels to a small town in Alaska to investigate the murder of a teenage girl. In this town, the sun never sets, and his inability to sleep represents his inability to deal with the many bad choices that have made him guilty over time. Pacino’s character ends up cutting a deal with the killer to prevent his own scandal from getting out, all the while believing he’s acting nobly.The problem with “Insomnia” is that his guilt and his deals with the killer are all part of some elaborate psychological game, but really it just seems like he’s a washed up old cop making horrible mistakes. And for a film about the dreary feeling of insomnia, it’s pitched at this intense level of ferocity, with delusional flashes of lights and colors to amp up the psychodrama.What I admire about the film more than the story are the performances. Pacino does about his best work of the 2000s in “Insomnia,” presenting himself as an actor and a character who has really done the rounds and seen the worst. When he uses Nolan’s crime procedural rules and tactics, its because he’s a guy that can now see through the bullshit of punk teenage witnesses, subduing them by using his language calmly instead of losing his temper.But what’s more, Nolan uses fog, shadows and Foley effects to play up the creepy noir aspect of the story rather than the action. “Insomnia’s” signature scene shows Pacino wandering in a foggy purgatory searching for the killer. I won’t reveal what happens here, but Nolan erases our sense of space and coherence and tickles our other senses with the accentuated plodding of footsteps and resounding gunfire.“Insomnia” may not be an essential film in Nolan’s repertoire, but it shows growth. We can see how he can handle a studio production and add his own flavor to it. He was going to need it to prepare him for his next project.“As a symbol, I can be indestructible.”The League of Shadows plays an important role in “Batman Begins.” “We step in every time a city signNowes its decadence.”Following 1997’s abominable “Batman & Robin,” Warner Brothers had exhausted one of its most lucrative franchises, and at just the worst time. “Spiderman” would explode into the popular culture just five years later, and they were yet without a superhero franchise to answer the call.The decision then to bring in Christopher Nolan was a gamble. It was his job to essentially usher in a new kind of superhero film.“Batman Begins” did just that. The movie brought in nearly $400 million, it put Christian Bale on the road to being an A-list star and it quickly made Nolan the luckiest man in Hollywood.Passionate or lukewarm, critics everywhere talked about how “Begins” was “unexpectedly good” and helped “breathe new life” into a dead and gone franchise. Roger Ebert said, “This is at last the Batman movie I’ve been waiting for.” The New York Times’ Manohla Dargis wrote, “”Batman Begins” is the seventh live-action film to take on the comic-book legend and the first to usher it into the kingdom of movie myth.” Nolan’s film was, “Conceived in the shadow of American pop rather than in its bright light,” she added.Dark and dour superhero movies are hardly seen as a breath of fresh air not even 10 years later. Nolan’s film operated on a level of myth and symbolic stature that comic book movies should not only be taken seriously but should be the driving factor in our cinematic popular culture.How did Nolan become the poster boy for this movement? He had made a film specifically about symbols and legends. “Begins” is filled with mantras designed to inflate your stature in the eyes of the public.“You become something more: a legend.”“You must be more than a man in the eyes of your opponent.”“As a symbol, I can be indestructible.”This isn’t subliminal messaging designed to stimulate demand for superhero movies. Batman is a character grappling with his own identity, one who can do good when he battles his own fears and becomes a monster to project his fear onto his enemies.People have admired Batman for being a superhero without any powers, but Bruce Wayne’s strength is that his alter ego is superhuman. Batman is a legend, a myth and a god capable of anything in the eyes of the public who fears and admires him.Maybe Nolan is joking in “The Dark Knight” when copycat Batmen try to help and question what the difference is between them. “I’m not wearing hockey pants,” Batman bellows, and neither are all the other DC and Marvel comic book movies that have taken themselves way too seriously.Most superhero films now share the epic scope and manufactured darkness that “Batman Begins” created, but Nolan has a special touch that other directors lack. Walk in a minute late to “Begins” and you might not even know this is a Batman movie. Nolan makes a mockery of the origin story by pulling resources and iconic gadgets completely out of its ass, something that in another movie would warrant an Easter egg.He even turns the action into an incoherent blur, granting us the idea of an indestructible force without actually allowing us to see anything. When Batman disappears mid conversation with Jim Gordon, this is Nolan using his methodic cinematography and editing style as a visual gag. What if through the magic of editing the subject of the next shot was replaced with nothing? Now Nolan has a character that can help him do that.Even the mantras work because Nolan is treating them like singular ideas that need to be methodically explained through rules and order. It’s not enough for Nolan to just provide a training sequence montage. He needs Liam Neeson to coach you through these subtle extensions of the same philosophy. Another director would bluntly repeat them.Like Batman, Nolan had performed a deft-defying rescue and was a figurative legend. He now had the clout to take up a more personal project on a bigger scale, and it was only a matter of time to see what trick he would pull out of his hat next.“Are you watching closely?”A magic trick is often so simple to detect if you know what you’re looking at. But the magician’s job is diversion. He demands our attention on something other than the obvious tell.“The Prestige” is Christopher Nolan’s elaborate illusion of a film. He asks us to watch closely, to follow the three steps (The Pledge, The Turn, The Prestige) of the magician’s performance and to piece together the screenplay’s endless web of betrayal, love, hatred and devotion.But Nolan puts all the clues in plain sight. We’re watching so closely that we ignore the film’s other stylistic choices. Like “The Prestige’s” characters, we become obsessed with the wrong thing.“The Prestige” is the twistiest film Nolan ever made. It’s a complicated whodunit between two rival magicians, one who wants revenge for the accidental death of his wife and the other who wants the same success and support for his family as his rival.Nolan was smart to make a film between the two Batman movies, but it underperformed at the box office and wasn’t entirely well received by critics. It first had the unfortunate luck of being released in close proximity to another paranormal magician film, “The Illusionist.” But what’s more, critics saw “The Prestige” as empty entertainment value designed to mess with your head and nothing more. The experience is so complex and the characters so morally corrupt that it’s emotionally draining. A review of “The Prestige” by Film Threat’s Mark Bell echoed the most common criticism of all of Nolan’s work, saying, “When all is said and done and you get the full explanation of what meant what and who did what to whom, it’s not fulfilling at all. It’s a magic trick that’s all showmanship and craft, but lacking true whimsy, ultimately failing the audience.”But think about it. Doesn’t a magic trick always lose its appeal once you know how it’s done? If “The Prestige” was all about its ending, that would defeat the purpose. You want to be fooled.“That feeling of bafflement and wanting to know the secret behind it, that’s a great feeling. I wanted to make a film that embraced that feeling,” Nolan said in an interview with Spike TV.Why otherwise would Nolan leave so many dead giveaways? SPOILERS AHEAD! We know Tesla’s machine is capable of making duplicates, and we know it makes them away from the machine itself, so why should we be surprised that Angier was making copies of himself all along? We see him with a gun when he first tests it. And what else could he have been doing with those water tanks? We even know Angier drowned in one at the beginning. As for Borden, the movie keeps telling us that the only way he could possibly do the trick is with a double. And we know that Tesla made a machine for Borden already. We even get an idea of Borden’s split personality when he says he doesn’t love his wife today. SPOILERS DONE.Nolan wants to wrap us up in the mystery of the film, and he does that by constantly repeating the film’s main idea that you must give yourself fully to your art. He shows it and tells that one idea as many ways as he can until it’s the only thing you’re focused on, not the many plot holes.And it’s even the reason Nolan cheats in his twist. It’s safe to say that the twist in “The Prestige” is not altogether possible. In a movie that otherwise considers itself a gritty, ruthless depiction of an older time in London, Nolan incorporates a twist that adheres to the paranormal.Here again we see similarities in Batman’s use of a sonar device that allows Lucius to map all of Gotham City, the fact that Lenny in “Memento” had always been lying to himself, that Cobb could just disappear off the radar in “Following” in just a stretch of dialogue, or that the villain in “The Dark Knight Rises” comes completely out of left field.Nolan cheats because he wants you to know that these acts of magic, as it were, are totally conceived by someone.This is Nolan’s primary innovation. He can make absurd science fiction or action films and pass them off as reality, and yet he can take that formulaic blueprint of reality and let you know just who drew it up.Granted, in “The Prestige” he does all this in the guise of another stylistically uninteresting film. For a movie that devotes so much time to period detail, Nolan spends a lot of it studying Christian Bale and Hugh Jackman’s faces. It’s other cheat is in finding a way for Borden and Angier to always show up onstage as the assistant from the audience just so that they can sabotage one another. This seems to me a less intentional flaw in the screenplay, but I digress.To really make something great, Nolan needed to achieve something more. He had always attracted fierce acting talent to his projects, but the films were always bigger than the actors. If he had someone who could carry the film away on a wave of energy, then he could make something people would remember.He needed something of a wild card.“And… here… we… go.”Heath Ledger died in his bed on January 22, 2008. The cause was an accidental prescription drug overdose.The effect was much greater.Christopher Nolan had not yet begun editing on “The Dark Knight” when news of Ledger’s death came in. Suddenly his job was not just to make a film but a tribute.“When you get into the edit suite after shooting a movie, you feel a responsibility to an actor who has trusted you, and Heath gave us everything. As we started my cut, I would wonder about each take we chose, each trim we made,” Nolan wrote in a eulogy article for Newsweek and The Daily Beast. “I see him every day in my edit suite. I study his face, his voice. And I miss him terribly.”If “Batman Begins” had become a symbol for what a superhero movie could be, “The Dark Knight” became a symbol for what a superhero movie should be, and it had happened before the movie was even completed.The anticipation for the film had achieved mythic proportions in a way I had never known in my lifetime. I saw Ledger’s face hidden under the Joker’s makeup every day when I worked at a movie theater, the trailer repeating every hour as though the film’s power beckoned. For an 18-year-old still learning to appreciate great film, the best movie I had seen that year prior to “The Dark Knight” was “WALL-E,” so there was absolutely nothing I was anticipating more.When the movie finally arrived, I was working concessions for our theater’s midnight showing. It was the busiest two hours I’d ever worked, and our theater was just one of the 3,040 theaters nationwide that helped “The Dark Knight” earn $18.5 million overnight, a midnight screening record for the time.Ledger’s death impacted the way “The Dark Knight” was received in a way Nolan could’ve never controlled. The film made $533 million domestically and over a billion worldwide. Audiences trumpeted its greatness so loudly that it rocketed its way to the number one spot on the IMDB Top 250, ousting “The Godfather.” It also won a posthumous Oscar for Ledger’s supporting actor work. Something about The Joker dangling on the end of Batman’s harness was ambiguous enough to cement Ledger’s permanent legacy on film.But Nolan was never the same either. For an emerging 21st Century talent to achieve such critical and financial success (and for of all things a comic book movie) figuratively placed him into a directors’ pantheon. At the moment, he was untouchable. Soon, an unexpected wave of analysis and criticism were thrown at the director and his entire line of work. Nolan was now not only one of the most respected new directors but also the most polarizing.I myself have read much of this criticism, and I wondered if four years later “The Dark Knight” could still hold up to its legacy and its place beside what I felt to be a disappointing finale to the Batman trilogy.“The Dark Knight” is and was always the film I wanted from Nolan. It’s his best work by a mile and still encapsulates everything I’ve discussed about him so far. It’s a monumental achievement.This time around, we see Batman before Bruce Wayne, the symbol before the man. His legacy has created tainted vigilantes fighting with guns and getting people killed, and the Gotham once riddled with organized crime is now a cesspool of chaotic violence.“It had changed in three years. Bigger. More real. More modern. And a new force of chaos was coming to the fore,” Nolan recalled in a foreword to the book “The Art and Making of The Dark Knight Trilogy.” “We’d held nothing back, but there were things we hadn’t been able to do the first time out—a Batsuit with a flexible neck, shooting on Imax. And things we’d chickened out on—destroying the Batmobile, burning up the villain’s blood money to show a complete disregard for conventional motivation. We took the supposed security of a sequel as license to throw caution to the wind and headed for the darkest corners of Gotham.”The success of “Batman Begins” and the symbol it created in popular culture allowed Nolan to run with whatever story he had in mind, and he used a new symbol, The Joker, to convey a theme that seemed to combine both “Begins” and “The Prestige.”What if a symbol could inspire madness and bafflement? How could our minds be twisted if we believed things were in a state of anarchy?The Joker is such a mystifying, impossible figure as seen in “The Dark Knight.” He has a sadistic presence and somehow appears to have unlimited resources to create any social experiment he wants. Through using only mental patients, he can rig thousands of barrels of explosives in warehouses and on boats without anyone noticing. He appears to have no altar ego and his backstory, as told by him, is a lie. He’s not altogether supernatural, but he’s a symbol too.He says to Harvey Dent that he just wants to introduce a little anarchy into the world, and we believe it in the same way we believe Cobb’s intentions in “Following.” But that’s not entirely true. It’s a lie firstly because we know The Joker is a compulsive liar, and secondly, his plans are always several steps ahead from what anyone can anticipate.Like Nolan, The Joker is all about rules and order, but he wants them for different reasons than Bruce Wayne does. His goal is not to create anarchy in Gotham but to replace the symbol of Batman with a new one. He asks Batman to remove his mask to reveal he’s just a man, not a symbol. That doesn’t happen, so when Batman has just upended The Joker’s truck, he stumbles out and stands in the middle of the street bellowing, “Hit me!” Had he done just that, Batman’s reputation as a hero who doesn’t kill people would be destroyed. Failing that, he transforms Dent himself into a demon, the opposite of the likeable DA the public envisioned.All of these set pieces, including The Joker’s ferry experiment, are all elaborate plot devices for Nolan to emphasize his philosophies. They work as thrilling stunts firstly because they’re tangible and done without CGI. But what’s more, Nolan layers multiple timelines of chaos (Batman and The Joker’s interrogation, the man with the cell phone in his chest, Dent’s kidnapping) in classic action movie fashion. Layered timelines are a staple of Nolan films going back to “Following” and continuing through “Inception,” but here with a thousand things going on at once, The Joker seems to be an omnipresent force pulling all the strings.None of this would be possible without Heath Ledger in the role of The Joker. Watch him slick back his hair as he approaches Maggie Gyllenhaal or smack his lips as he explains how “the box’s” plan to the mobsters is just a bad joke. If the movie itself doesn’t have a sense of anarchy, Ledger himself brings such an element of surprise to every moment. Ledger had the acting sensibility of a young Marlon Brando, a sort of awkward masculinity that made his emotions and his façade ambiguous and impenetrable. The Joker then is one of his most perfect roles. He can make a line like “Why so serious” instantly iconic because he shares the dialogue’s mystique.If you ask me, Batman did not need to be a trilogy. The myth continues endlessly when Batman rides off into the fog, and I didn’t need anything resolved. If Nolan had followed the same unfortunate route of both Ledger and his title character and disappeared, he would be heralded as a master. He would’ve been a young talent who could’ve been so much more and left it at that.But I believe in Harvey Dent. “You either die a hero or live long enough to see yourself become the villain.”“I’d hate to see out of control.”Image courtesy of The InquisitrWhat do we know so far about Christopher Nolan?1. We know he likes his films to adhere to rules. His characters incorporate systems into their livelihoods (Bill’s following, Lenny’s tattoos, Dormer’s crime scene investigations, Bruce Wayne’s pledge to not kill anyone, the three steps to a magic trick, The Joker’s games). Some characters break their rules, and others follow them blindly, but both paths either literally or figuratively lead to their destruction.2. His characters have no morality. They operate on one philosophy, one principle or one goal (Cobb’s mental robberies, Lenny’s dead wife, Bruce’s pledge to not kill anyone, Angier’s dead wife, The Joker’s dream to watch the world burn).3. In addition to having no morality, they are so obsessed with their goal that they are often mentally or emotionally disturbed protagonists (Lenny’s short-term memory loss, Dormer’s insomnia, Bruce’s fear of bats and his guilt over his parents’ death).4. He’s a poor visual storyteller, or at least he doesn’t try to be a conventionally stylish storyteller. All of his dialogue compositions are one-shot close-ups, and he often focuses in on exactly what the characters are talking about as they’re saying it. Critics have complained that Nolan’s action sequences are clunky, if not without flow entirely. Stephanie Zacharek went as far to say that Nolan’s images are “disconnected from one another.”5. The stories Nolan tells are often more about the buildup than the end. We want to know the little bits and pieces to Lenny’s psychosis, Borden’s Transporting Man trick and The Joker’s elaborate schemes.6. And yet Nolan still chooses to incorporate complicated twists into the screenplays. He cheats with talky twists and paranormal devices to let you know that he’s constructed this particular twist.7. He layers timelines one on top of the other to create an illusion of complexity. “Memento” operates in two timelines, “The Prestige” in three, and “Following” in four, but only intercutting between three at one time.8. Nolan makes films that are preposterous in terms of action and even story, but he portrays them in such a way that they appear realistic (see: all of the above).Oh, I’m sorry, did you not enjoy my laundry list of points I’ve already made clear, my dozens of examples and my ordered group of traits that feel like homework?That’s the way I feel watching “Inception.”“Inception” is Nolan’s “masterpiece” in the sense that everything we need to know about Nolan as a director and how he operates is here in excruciating, literal detail.Nolan apparently worked on the screenplay for nearly a decade, and “Inception” began as a heist film. This is one of the few genres where exposition and explaining every step of the process is part of the fun of watching the movie. But Nolan realized he needed a way to introduce an emotional element into the story, and this is what complicated the screenwriting process for so many years.So it really struck audiences as a brilliant, complex, multi-layered labor of love. This film too rocketed to number one on the IMDB Top 250, and because it came from the director of the previous “best movie ever,” suddenly teenagers and cult film enthusiasts had a masterpiece and an auteur director to call their own.Rarely had a blockbuster epic been this structurally complex and surreal, and audiences were drawn to that complexity whether or not being complex was actually admirable. (See: College Humor poking fun at “Inception’s” plot)And yet, Nolan does start with one simple idea that he continues to expand upon throughout the movie: “Once an idea is fully formed, it sticks.” (you know, like, don’t think about elephants) In this case, the idea is that reality may not be all that it seems. The world you are living in may be a dream, and you may no longer be able to grapple with reality.This is nothing new to film. Lots of films have posed questions about reality, even dreams. Do movies like “The Matrix,” “Blade Runner” and “Mulholland Dr.” ring a bell?The difference is Nolan pulls out his whole arsenal of tricks to get you to embrace this possibility. As we know, his vision of a film that gets its point across is not tidy, nor is it simple. Roger Ebert put it best when he wrote, “Nolan successfully made the film he had in mind, and shouldn’t be faulted for failing to make someone else’s film.”He started with the rules. “Inception” has plenty. Dream worlds adhere to rational stretches of time, such that five minutes in reality gives an hour in one dream, a week in the next level, and so on. When constructing these dreams, it’s important to never construct from specific memories. There are more. But break any of these rules, and the “projections” of the dreamer’s subconscious will come to attack you, alerting the dreamer to the intruder’s presence.Next is Cobb, a man with a goal to get back to see his children again. He’ll do anything to get there, including sabotaging a multi-million dollar corporation so that another wealthy CEO can claim a monopoly on the market. Cobb acts on his principles, not his morality.Cobb of course is mentally distraught, and after being in Scorsese movies for a solid decade, no one is better at playing emotionally tormented individuals than Leonardo DiCaprio. After visiting the dream world known as limbo, Cobb no longer has a perfect hold on reality. His wife killed herself and is haunting his dreams and the dreams of those he invades. And what naturally make Cobb suffer are all the rules he breaks. Don’t construct from memories. He returns to his dark past regularly. Don’t use someone else’s totem. He uses Mal’s. Again, the list goes on.All of this is presented as linearly as possible. “Inception” is loaded with talky exposition to drill these rules and ideas into your head, and it’s by far the strictest in terms to tailoring its shots to exactly what is being said in the screenplay. If a character discusses the rules of the totem, we get a shot of the top spinning. If a character is talking, we see him or her talking first. When Cobb reads aloud “I will break up my father’s empire,” we see it scribbled on a white board. Only rarely does the film actually speak for itself to explain the rules of the dream world or to advance the plot. A good example is the pinwheel hidden in the bedside safe, one of the film’s most emotionally poignant moments, or Eames raising a new, bigger gun from below the frame line as a brief visual gag.“Inception” is a complicated film, and Nolan provides a complicated twist. The world seems to be ending outside of Mal’s limbo apartment, and Cobb still takes several minutes to describe just what happened to Mal when the two of them were in limbo before. Nolan does this to set the character up for his own questioning of reality, challenging the baseline moments that have given Cobb security earlier.So when we signNow the film’s final shot, the movie achieves a level of ambiguity. Cobb’s story is resolved happily, but we’re still left with the film’s theme in mind, nagging us that both the character and we may still be wrong.Part of the reason I can’t enjoy “Inception” is because the film seems to be speaking about its own construction, constantly referencing what it’s doing and how it does it. Maybe “Inception” is really just a documentary for how Nolan makes all his movies.To explain, let me start by saying this film is actually innovative for layering five timelines on top of each other and intercutting between four of them. We can piece together where each layer is in time based on the color palette and weather patterns within each scene. Any more timelines and we may be lost. Nolan has always used multiple timelines and layers to his films, but he overthinks his metaphor when he organizes Cobb’s dreams into literal layers, signNowable through an elevator in Cobb’s mind.Nolan loves rules in his films, and here he calls them that. Nolan loves exploring one simple idea in a film until it sticks, and his characters are on a mission to implant one simple idea into the mind of an audience member. The Mr. Charles plot device is designed to let the audience member know that it specifically is a plot device.He even is a filmmaker who makes dreamlike movies into realities. And what does he say here? “It feels real while we’re in them. We only realize something is strange when we wake up.”This is as close as we’ll ever come to understanding Nolan, and he delivers it to us verbatim. In fact, we begin to realize that “Inception” doesn’t feel like a dream at all. What dreams adhere to rules? In what dreams can we sense that actual time has passed, let alone a week or a month? Why is there no spontaneity in the dreams? Why are there no unicorns, naked women, people fighting with lasers or something stranger instead of just guns? Why can’t Cobb fly in his dreams?But the bigger reason I dislike “Inception” is that I feel he’s tackling a theme he handled so much more elegantly, and more fun, in “Memento.” “Memento” is specifically about memories, but what are memories, really, other than constructed figments of reality that exist exclusively in our minds? Cobb is attached to his dark memories of his dead wife, and he is so certain that the life he’s living is reality, but he may be fooling himself. Lenny has a dead wife, and he is fooling himself. Both characters live with regret of not being able to do more for their wives, and both will grow old and be filled with it. We leave Lenny at the tattoo parlor knowing he’s stuck, but we have to follow Cobb down into the rabbit hole of limbo to learn and witness the same thing.It’s a film that panders to you so much to let you know its brilliant, and it treats everything with such grave intensity that it forgets to be enjoyable. Its set pieces are remarkable, but are for their own sake. The only stunt we actually get to see repeated in the climax is the paradox stairs, not the folding city or the mirrors under the bridge continuing to infinity. The movie rarely has a moment of levity, save for Joseph Gordon-Levitt falling off a chair or stealing a smooch from Ellen Page. And all the action movie set pieces feel like clichés from Bond movies.And yet “Inception” quickly became the most fiercely debated film of 2010. Some critics argued it was more fun to speculate over than to actually watch. That’s because countless theories sprung up online about what really happened.“The end when Cobb returns home to his kids is really a dream! Have the kids aged? Are they wearing the same things? But didn’t the top look like it was wobbling? How will we know?”“Maybe the entire movie is a dream! What about what Mal says to Cobb about how everything in his life seems too good to be true? And they keep saying to take “a leap of faith.” And we never really know how he ended up in Mombasa in the first place. It fits with the rules of a dream.”“But wait! That’s how all movies are! “Inception” is really about making movies. It makes perfect sense, because Cobb is the director, Saito’s the producer, Ariadne is the writer, Fischer’s the audience and Eames is the art director! Does that make Michael Caine the stodgy film critic?”“There should be more to it than that though, right? Maybe the whole thing is an ode to architecture. Nolan is always constructing things in his movies, and everyone seems to be building something here. Look at the top: it’s a pseudosphere, a structurally perfect object where every point curves away from the center.”I personally don’t believe any of these, mainly for the reason that while all these theories are interesting, none of them really suggest what Nolan is actually trying to say or do with the movie.(Side note: Also, all of these theories are wrong on a practical standpoint. Nolan used two different sets of kids, and they are wearing different clothes. Nolan did not intend to make a movie about movies. The top is really just something the prop department threw together so that it would stay spinning for a long time.)He got his audience to do exactly what he wanted, which is to study and obsess over the details of the film and come away with a central idea.But he went too far. The audience that is in love with “Inception” has missed the bigger point. They scrutinized the ending to the point that they overlooked the film’s elegant ambiguity. Whether the ending is real or a dream does not really matter in the broader scheme of things, and knowing gets the viewer nowhere. (Again, see: College Humor’s take)“I’ve been asked the question more times than I’ve ever been asked any other question about any other film I’ve made,” Nolan said in an interview. “What’s funny to me is that people really do expect me to answer it. There can’t be anything in the film that tells you one way or another because then the ambiguity at the end of the film would just be a mistake. It would represent a failure of the film to communicate something. But it’s not a mistake. I put that cut there at the end, imposing an ambiguity from outside the film. That always felt the right ending to me.”The important thing to Nolan is that what is real and what is fake no longer matters to Cobb because he has his kids, the thing that matters most.Now the things that matter most are less clear. Movies are epic, dark, wordy and complex because an ambitious filmmaker unintentionally fostered over-ambitious fans. Stephanie Zacharek feared that all movies will now only be “awesome” rather than “great,” and in the two years since, she may be right.“Ah yes… I was wondering what would break first.”A man can only continue to be seen as a symbol for so long.Maybe that’s what Nolan is doing by throwing in the towel on “The Dark Knight Rises” and ending the Batman franchise. Bruce Wayne cannot sustain this kind of pressure any longer, and neither can Nolan. They have to move on, but first leave in a gigantic bang.Following the surprise hype of “The Dark Knight” and the over-hype of “Inception,” “The Dark Knight Rises” could only go down in anticipation. It was already unlikely that lightning would strike three times. But then there was controversy over Bane’s inaudible dialogue behind his Hannibal Lecter mask, death threats started pouring in to dissenting critics on Rotten Tomatoes before the film had even been released, and worst of all, the tragic midnight movie shooting in Aurora, Colorado cast a gloom over the whole occasion that was even too dark for Batman.What’s interesting about “The Dark Knight Rises” is that we see Nolan stepping away from the spotlight of yet another iconic, superhero epic. He chose to make a film about socio-politics and bleak ideologies of hope in the modern day. I myself wrote in my review of “Rises,” “’The Dark Knight Rises’ is more of an enduring challenge than some will expect. For others, it will even feel little like a superhero movie. But its heavy themes of untapped emotion and social anarchy dwarf the flimsy blandness of ‘The Avengers’ and ‘The Amazing Spiderman.’ It does the Batman franchise proud.”With this film, critics almost pre-emptively combatted the hype with lengthy analyses designed to put discussion of the movie into an appropriate context. And in the process, the Internet has produced such an engaging web of articles going all the way back to the beginning of Nolan’s career. To read about one film is to just start to absorb them all. You become obsessed with talking about his films even if you don’t particularly enjoy them.So it pains me to not be able to discuss and debate the many unbelievably convincing contrarian viewpoints that successfully rationalize Christopher Nolan’s work, not just diminish it. Jim Emerson, Bilge Ebiri, Stephanie Zacharek, Andrew O’Hehir; the least I can do is link to them and urge that you see how polarizing and animated discussion about Nolan really is.But the writer that concludes my thoughts on Nolan best come from a recent post by the great David Bordwell.“Nolan is now routinely considered one of the most accomplished living filmmakers. Yet many critics fiercely dislike his work. They regard it as intellectually shallow, dramatically clumsy, and technically inept. As far as I can tell, no popular filmmaker’s work of recent years has received the sort of harsh, meticulous dissection Jim Emerson and A. D. Jameson have applied to Nolan’s films. People who shrug at continuity errors and patchy plots in ordinary productions have dwelt on them in Nolan’s movies. The attack is probably a response to his elevated reputation. Having been raised so high, he has farther to fall,” Bordwell writes.Nolan is at the top of a new generation of directors in the 21st Century. They make films designed to be awesome, designed to be obsessed over and talked about not only as great works of art but as mind-shattering experiences on a widely accessible scale. It’s important to know if this is a direction worth travelling in. Bordwell continues:“Nolan’s work deserves attention even though some of it lacks elegance and cohesion at the shot-to-shot level. The stylistic faults I pointed to above and that echo other writers’ critiques are offset by his innovative approach to overarching form. And sometimes he does exercise a stylistic control that suits his broader ambitions. When he mobilizes visual technique to sharpen and nuance his architectural ambitions, we find a solid integration of texture and structure, fine grain and large pattern.”In “The Dark Knight Rises,” Batman is no longer the mysterious figure. Wayne himself is the person we don’t fully understand. And until this point in his career, Nolan has been the white knight for movie critics and fanboys alike. Only now at the end of his biggest franchise do we get a glimpse of the man and director he is and the one he can be.
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
How do you esign financial documents in pdf?
How to get suppliers to sign up for e-procurement?
Get more for Erase eSignature Presentation Safe
- How To eSign Illinois Profit and Loss Statement
- How To eSign New York Profit and Loss Statement
- How To eSign Ohio Profit and Loss Statement
- How Do I eSign Ohio Non-Compete Agreement
- eSign Utah Non-Compete Agreement Online
- eSign Tennessee General Partnership Agreement Mobile
- eSign Alaska LLC Operating Agreement Fast
- How Can I eSign Hawaii LLC Operating Agreement
Find out other Erase eSignature Presentation Safe
- Disclosure statement and agreement sierra credit form
- Dss 1814 dhhs nc department of health and human services form
- Weekly homework sheet rigsbysclasscom form
- 25 104 annual insurance tax report surplus lines form
- Application form for admission muids mahidol muids mahidol ac
- Chronic illness accelerated death benefit rider supplement form
- Calstrs express benefit report 2015 2019 form
- Time clock correction form drive in autosound
- Pdf refrigeration permitplans2011pdf city of chicago cityofchicago form
- Www ctcseminars com files gagcert sample pdf pdf download form
- Pastoral support plan form
- Lpcc experience verification in state option 1 lpcc experience verification in state option 1 bbs ca form
- Icoi fellowship 2017 2019 form
- 1099 oid 2017 form
- Extension activity menus gr 5o3 teachers wrdsb form
- Applicant data form antioch university seattle antiochseattle
- Tvfc vaccine management plan templates contains contact list for vaccine coordinators routine vaccine storage and handling plan form
- Negotiated sale of redevelopment project area bb city of chicago cityofchicago form
- Float trailer chassis rental agreement parade parade form
- Apply for a loan 1199 seiu federal credit union 1199federalcu form