Share Electronic signature PDF Android
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






Advantages of Utilizing Electronic PDF Forms with airSlate SignNow
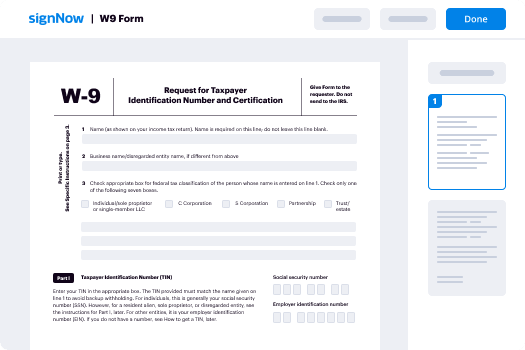
In the current digital landscape, effective document management is vital for enterprises. Employing an electronic PDF form via airSlate SignNow enables users to optimize their document signing workflows, guaranteeing a quicker and more productive process. This guide will lead you through the steps to fully utilize the advantages of airSlate SignNow for your electronic PDF documents.
How to Utilize Electronic PDF Forms with airSlate SignNow
- Launch your web browser and go to the airSlate SignNow main page.
- Sign up for a complimentary trial or log in if you already possess an account.
- Choose the document you intend to sign or distribute for signatures and upload it.
- If you plan to reuse this document later, convert it into a template.
- Access your document to perform necessary modifications: add fillable fields or input required details.
- Insert your signature and allocate signature fields for additional recipients.
- Click 'Continue' to set up and dispatch the eSignature request.
By utilizing airSlate SignNow, businesses can benefit from a variety of advantages that improve their document management operations. With a comprehensive feature set that offers a remarkable return on investment, users can effortlessly navigate and adapt the platform to suit their requirements.
If you're prepared to revolutionize your document management process, embark on your journey with airSlate SignNow today. Discover transparent pricing with no concealed charges and exceptional support available at all hours. Sign up now and witness how simple it is to integrate an electronic PDF form into your workflow!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is an electronic PDF form and how does it work with airSlate SignNow?
An electronic PDF form is a digital document that can be filled out and signed online. With airSlate SignNow, you can easily create, send, and eSign electronic PDF forms, allowing for a streamlined workflow that eliminates the need for paper. This solution enhances document management by ensuring that all signatures and data are securely stored and easily accessible.
-
How can I create an electronic PDF form using airSlate SignNow?
Creating an electronic PDF form with airSlate SignNow is simple and intuitive. You can upload your existing PDF document, add fillable fields, and customize it with your branding. Once your electronic PDF form is ready, you can send it to recipients for eSigning in just a few clicks.
-
Is there a cost associated with using airSlate SignNow for electronic PDF forms?
Yes, airSlate SignNow offers various pricing plans to cater to different business needs. Each plan includes features for managing electronic PDF forms, eSigning, and document tracking. You can choose a plan that best fits your requirements and budget, ensuring a cost-effective solution for your document management.
-
What features does airSlate SignNow offer for electronic PDF forms?
airSlate SignNow provides a range of features for electronic PDF forms, including customizable templates, drag-and-drop field creation, and real-time tracking of document status. Additionally, you can integrate with other applications, making it a comprehensive solution for managing your documents efficiently.
-
Can I integrate airSlate SignNow with other software for electronic PDF forms?
Absolutely! airSlate SignNow seamlessly integrates with popular software like Google Drive, Salesforce, and Microsoft Office. This integration allows for easy access and management of your electronic PDF forms, enhancing your overall workflow and productivity.
-
What are the benefits of using electronic PDF forms over traditional paper forms?
Using electronic PDF forms offers numerous advantages, including faster processing times, reduced printing costs, and improved accuracy. With airSlate SignNow, you can easily track changes and updates, ensuring that your documents are always up to date without the clutter of physical paperwork.
-
Is airSlate SignNow secure for managing electronic PDF forms?
Yes, airSlate SignNow prioritizes security for all electronic PDF forms. The platform uses bank-level encryption and secure data storage to protect your documents and sensitive information. You can confidently manage your electronic PDF forms knowing that your data is safe from unauthorized access.
-
What does PDF stand for a computer?
Portable Document FormatThe .pdf files can only be open with pdf reader softwares like the most popular signNow and Foxit Reader. These applications are also available for Android and iOS.Well, we mostly create pdf files for electronic signatures and to make it more safer.As we know, most of the companies uses their unique font style in their documents and if the company send a letter to any of their associates by an email in a Ms Word format. Their associates might find the document in different font style because they are not using the same font style. So pdf documents are not editable which makes them more portable to share. Pdf files maintain the same font style and style in which it was created.You can check by yourself by making documents in a ms word format and pdf format.If u wanna know how to create pdf documents u must google it.
-
What are some must have Android apps?
Edit: I wrote this answer for “must have Android apps” but these are same apps which have changed the way I used to live my life. Each and every App has helped me in one or the other way. I hope you will also find them helpful and a bit life changing. So here is the list: 10. Psiphon For those who use WiFi with proxy settings. So Psiphon bypasses and tunnel the websites or app through a different IP Address. 9. Mirror It's a simple app to record your mobile screen. Based on the concept of CamStudio in PC where you can record your screen, Mirror offers recording of your Mobile screen. 8. NTES- National Train Enquiry System If you are from India and you want to know the running status, cancelled train (partial or fully), Live Station and other features, this App is a must have. 7. VOLT Simple but effective for those who want to learn new vocabulary. That's too obvious, then why not others? Coz here you get the “memory key” which helps you relate the words and easier to remember them. 6. Parchi It a note making app. But here’s a catch. You can view, review, edit and add right from your lockscreen without need to open the app. Isn't that amazing! I personally find this app very useful. 5. edX If you are student or a learner who wants learn something new everyday, and cannot afford to go in the prestigious institutions like MIT, Harvard University, Cambridge, IITM, etc ten it is a must have app. Enroll yourself in any course and Bazinga!! You are ready to learn from the most amazing professors. Similar to edX, we have Coursera. 4. Walnut Manage your expenses on your finger tips. Its easier then that. It shows you your monthly expenditure, ATM locations, bill remainders and many more features. Its a must have app. 3. CamScanner Everyone doesn’t own a scanner but most of us have camera. So click the pic, upload to CamScanner and voila you are done. You have the scanned copy of your documents, notes, Marksheet and upload them on your DigiLocker. 2. inshorts Till now you all must be knowing this app. The tagline is also simple “News in 60 words” and trust me it is worth having. In this “I don't have time” world, you need news to be fast and accurate so here it is. 1. DigiLocker If you have this app then you don’t need to carry your personal documents like driving license, Adhar card, voter ID card, or even your Marksheets. Keep them safe in actual locker and leave the rest to your DigiLocker. And the best part is that it is acceptable as the original ones at every governmental or non governmental institution because it is developed under Digital India initiative. That's it for the day. Thank you and Enjoy !!! Update 1: Today I came across two new apps which I found useful. Hope it would help you all. 1.Forest : Stay focused Features • A self-motivated and interesting way to help you beat phone addiction • Stay focused and get more things done • Share your forest and compete with friends • Track your history in a simple and pleasant way • Earn reward and unlock more tree species • Customize your whitelist : Leaving Forest and using apps in whitelist won’t kill your tree. 2. Swachh Bharat Toilet Locator Swachh Bharat Toilet Locator is specifically useful for Indians who're committed for Swachh Bharat. Update 2: So I am back with yet another interesting app for you all. And trust me it is worth hanving. You are bored just go through it and kaboooom !!! You are into a black hole. Enjoy the ride. 3. Curiosity It is the latest app I installed but got addicted to it. It’s exactly works like its name, generates a curiosity which inturn increases your knowledge. It covers a large field of scope from Humanity to science to faith and many more. This app deserves more snapshots but why to increase the length of my answer. Comment below if you think the list should be updated? Thank you.
-
How would I contact Mycelium Client Benefits?
Mycelium Customer service number 1–800–298–9018 Mycelium Customer support number project by Megion Research & Development GmbH makes a number of products including the Mycelium Bitcoin Wallet, Entropy, Bitcoincard, Mycelium Gear (a payment gateway), ATMs, Local Trader, and Tabtrader. It is located in Vienna, Austria.The Mycelium Bitcoin Wallet is available for Android and for iOS. The source is available for review on GitHub. It has been awarded the prestigious "Best Mobile App" award by Bitcoin Block Explorer - Blockchain in 2014.[1]It is available in 12 languages, translated by volunteersBitcoin Wallet Features100% control over your private keys, they never leave your device unless you export themNo block chain download, install and run in secondsUltra fast connection to the Bitcoin network through our super nodes located in different data centersWatch-only addresses & private key import for secure cold-storage integrationEncrypted PDF backup and restore of single key accountsSend and receive by specifying an amount in Fiat and switch between fiat and BTC while entering the amountAddress book for commonly used addressesTransaction history with full transaction detailsImport private keys using SIPA, mini private key format (Casascius private keys) or xPriv from QR-codes or clipboardExport private keys as QR-codes, on clipboard, or as encrypted PDFsSecure your wallet with a PINCompatible with other bitcoin services through bitcoin: uri handlingCompatible with Orbot (socks setting) so you may connect via Tor even without rootingSupport for BIP38 KeysView your balance in 164 fiat currenciesIntegrated QR-code scannerFind other people to trade Bitcoins with the integrated Local TraderDirectly spend from paper wallets (single key, xPriv or master seed)Trezor enabled - directly spend from trezor-secured accounts.Mycelium Entropy compatible Shamir-Secret-Shared 2-out-of-3 keys spendingCompatible with other bitcoin services through bitcoin: uri handlingShare your bitcoin address using NFC, Twitter, Facebook, email and more.BIP70 payment request compatibleIntegration with service Cashila to send money via SEPA[3]Support for BitID AuthenticationDeterministic signatures for Bitcoin transactions (RFC6979)Local TraderMycelium Local Trader is a decentralized in-person exchange that is built right into the Mycelium bitcoin wallet. Because the coins are stored locally in your wallet, the Local Trader exchange never needs to hold any of your bitcoins or fiat. Local Trader servers only help arrange the trade between buyers and sellers, manage the transaction, and calculate reputation ratings based on the trades.BitcoincardBitcoincard is a stand-alone device that acts as an electronic wallet. It can be used to secure the wallet in a safe place (outside the computer, making it inaccessible to hackers). The goal is to create an infrastructure-independent, self-powered, ad-hoc network that could dynamically form wherever a sufficient number of nodes came together to support it. A prototype was presented in Q1 2015.[4]Mycelium EntropyMycelium Entropy is a small USB device that uses hardware based entropy to generate directly printable Bitcoin paper wallets, without the need for a PC. The project was successfully funded on Indiegogo[5].Mycelium GearMycelium Gear is designed to allow you to receive BTC from customers directly into your wallet controlled by you only. Mycelium Gear eliminates the notion of payouts - you get your BTC instantly. It's easy to integrate with your online store or website, with no special skills required. Optionally you can convert your BTC to fiat using the Cashila service.
-
What is the future of IBM filenet eforms?
I am not sure about future of IBM filenet eForm, but I guess they and some of the other market leader had failed to create a complete solution for eForm that’s why you can see it’s not yet popular into the market yet and paper forms and pdf forms are still in use.We still use papers even in the digital age. We still use paper in various processes like form filling, documents, and approval. Paper and printing cost is much higher and companies still doing this due to less explored possibility of paperless technologies or limitations of existing solutions.There is a small firm in India called “Swayam Tech Lab” who has started figuring out the answer for this question of how to eliminate papers completely in early 2017. And the answer they have give is Trexa. Trexa solving some of the biggest, nastiest problems our industries were facing due to lack of complete solution.We firmly believe that technology has potential to replace paper and save nature, while making processes more efficient then paperwork. Using the technology we see the future where the paper is obsoleted and we are helping in shaping that technology - says CEO of the companyTrexa is an enterprise solution that helps you convert paper forms, pdf forms and document processes paperless, efficient, and automated by making them digital. Deploy to internal teams or customers on the web or mobile and efficiently collect and analyze your data on an interactive dashboard.What makes it different from others market-leading solutions that it provides a complete solution to the bigger problems of adopting the digital solution for replacing the papers. While many of the eForm solutions on the market are disruptive and don’t account for different business needs, We have designed the complete platform for all the businesses from small scale to large scale.They have made the overall process very smooth from creating forms, distributing among teams and gathering data. Our powerful designer will enable the user to upload their existing paper form or pdf form, make it digital form using drag-and-drop interface and distribute it to teams. Empower mobile user to capture form data digitally from anywhere whether they are online or offline. We have fascinating mobile app for iOS and Android to easy the create, edit and submit documents from anywhere. All the data will be stored in the cloud and the intuitive dashboard will allow you to turn data into visual charts.There are many benefits to using Trexa electronic forms instead of paper-based forms or pdf forms. These benefits include the following:• Reduce errors, increase the accuracy of information and improve data quality through validations. • Reduce form filling time and provide ease of form filling• Avoid lost data• Speed up the internal work processes• Eliminate data entry re-typing• Reduce the costs associated with form printing and handling• Make documentation and information easier to share• Stored data can be used for further analysis• Integration with other systems• Save space on filing• Helps the environment by eliminating paper• Keep information more secure• Easy accessibility via web and mobile• Allows document sharing for editing or signature• Offline editing on mobile application• Advanced searched capabilities over the form data and Analytics• Document approval processMore and more businesses are streamlining their workflows by converting paper documents to digital documents. But when it comes to your company’s forms, not just any electronic forms solution will do. You need a solution that will retain the exact look and feel of your paper or pdf forms and contracts while enabling users to fill them from web or mobile and save to cloud, access them in anytime, and approve them. With Trexa eForms solution you can easily move paper-based processes to the Web and accelerate form filling process. Now your organization can expedite forms submission and cut the costs associated with managing paper at the same time.For more information please visit our website: TrexaView introduction YouTube
-
What is a good, free document management solution?
When it comes down to choosing a good solution to manage your documents, whether you’re an individual, or part of a company, there are a few things to consider, and it basically boils down to what you need the software to accomplish, how much automation you want, how easy do you want it to be.A good all around option I’d suggest checking out it Kdan Document 365. It has some nice features to help you manage your PDFs (editing, signing, etc.,) and other kinds of documents you might be working with. If you’re part of a company, it’s easy to share and collaborate on projects/documents/presen...
-
Can I use my CBSE 10th class mark sheet for an identity card issued by a recognized educational institution for a PAN card?
Digital Documents Now Valid. Here's All You Need To Know About DigiLockerDigiLocker is a platform for issuance and verification of documents and certificates in a digital format, thereby eliminating the use of physical documents. Indian citizens who sign up for a DigiLocker account get a dedicated cloud storage space that is linked to their Aadhaar or UIDAI number.DigiLocker is a cloud-based digital locker to save documents online. They are now be officially acceptedNew Delhi:The government, on Thursday, issued an advisory to all states to accept documents in electronic form. With the idea of paperless governance, and an aim to make life simpler for citizens, the government announced that documents such as driving license, car registration, voter ID, PAN card, school and college certificates, and many other documents issued by the government will now be accepted, when presented in digital form. These documents can even be used for photo ID purposes at airports and railway stations.DigiLocker, as the name suggests, is a 'digital locker' for citizens to securely save copies of all their documents.DigiLocker is a platform for issuance and verification of documents and certificates in a digital format, thereby eliminating the use of physical documents. Indian citizens who sign up for a DigiLocker account get a dedicated cloud storage space that is linked to their Aadhaar or UIDAI number.Government departments and organisations which are registered with DigiLocker can push electronic copies of documents and certificates issued by them, directly into the citizens lockers. Citizens can also upload scanned copies of their documents in their accounts. These documents can be electronically signed as well, using the eSign facility.Here is all you need to know about DigiLocker, and how to use it:Q) What is DigiLocker, and how does it work?A) DigiLocker is a digital locker facility provided by the government. It allows all Indian citizens to store scanned or digital formats of their documents. The technology used by DigiLocker is Cloud computing, where all citizens are given 1 GB (gigabyte) of storage space on a secure and private cloud account. DigiLocker is part of the government's Digital India initiative.The project was launched by PM Modi in 2015, when it had a beta version. It is now completely ready, with the government telling all states to start officially recognising it. It is aimed at reducing the need to carry physical documents, while also aiding in paperless governance.How the DigiLocker system worksQ) What are the benefits of DigiLocker?A) Some of the benefits offered by DigiLocker include:Citizens can access their digital documents anytime, anywhere and share it online for their ease and convenience. This helps in saving time, paperwork, and helps people get their work done on the move.It reduces the administrative overhead of government departments by minimising the use of paper, thereby making it a hassle-free and more environment-friendly way of getting things done.DigiLocker makes it easier to validate the authenticity of documents as they are issued directly by the registered issuers. Since documents are verified by the concerned departments, it helps a user get many other tasks done, for eg: documents required for various banking purposes, or at airports and railway stations, where IDs are needed.Self-uploaded documents can be digitally signed using the eSign facility (which is similar to the process of self-attestation of documents). Documents can thereby be shared as and when required, without it having to be manually delivered or collected.All physical documents can then be kept in the safety of ones home, minimising the chance of ever losing them, or damaging them.Here is a video showing how DigiLocker helps in our daily lives:Q) How can I open a DigiLocker account? What do I need?A) The DigiLocker facility is available only for Indian citizens. To open a DigiLocker account, you must have an Aadhaar card (Aadhaar number). To activate the account, it is mandatory to link your DigiLocker account to your Aadhaar (UIDAI) number.Q) Is my data (certificates and documents) safe in DigiLocker?A) The government assures that DigiLocker is completely safe, with some of the best security features available on date. DigiLocker allows only the user to access their data and documents. The user gets a secure and private cloud account, which is password-protected. Security measures also include a 256 Bit SSL encryption and mobile authentication based sign up process (with OTP facility). DigiLocker also comes with a 'timed logout', which means it logs the user out if the individual leaves it open and idle.DigiLocker follows the best industry practices, and keeps data 100 per cent private, allowing only the user to share details and documents with others. DigiLocker is ISO certified, and has an ISO-27001 certified data centre.Some of the main security features include:Standard Practices: DigiLocker follows standard software development practices of uniform coding standards, guidelines and reviews. Every release is reviewed and tested internally for security and penetration vulnerabilities before getting deployed on our servers.256 Bit SSL Encryption: DigiLocker uses 256 bit secure socket layer (SSL) Encryption for information transmitted during any activity.Mobile Authentication based Sign Up: DigiLocker uses mobile authentication based signup via OTP (one time password) for authenticating users and allowing access to the platform.Aadhaar Authentication based Issued Document Access: To receive issued documents from registered issuers, citizens need to authenticate themselves using Aadhaar's Biometric or Mobile OTP authentication service.ISO 27001 certified Data Centre: The application is hosted in a ISO 27001 security certified data centre.Data Redundancy: Data is backed up in secure environment with proper redundancy.Timed Log Out: To protect citizen's account from unauthorized access, our system is designed to terminate session automatically if extended inactivity is detected.Security Audit: The DigiLocker application has been security audited by a recognized audit agency and the application security audit certificate has been obtained.User Consent Based System: The data from DigiLocker is shared only with the citizen's explicit consent. All sharing and access activities are logged and conveyed to the citizen. Organizations that need access to citizens' certificates need to register on DigiLocker and seek explicit consent from the citizen.To know full details about the technical specifications of DigiLocker, please click here.Q) Who are the key stakeholders in the DigiLocker system?A) DigiLocker has three stakeholders. They are:Issuer: Entity issuing e-documents to individuals in a standard format and making them electronically available eg: CBSE, Registrar Office, Income Tax department, RTO (transport office), etc.Requester: Entity requesting secure access to a particular e-document stored within a repository (eg: University, Passport Office, Regional Transport Office, etc.)Resident: An individual who uses the Digital Locker service based on their Aadhaar number.Q) What are the main technology components of the DigiLocker system?A) The main technology components of the DigiLocker system include:Repository: Collection of e-documents that is exposed via standard APIs for secure, real-time access.Access Gateway: Secure online mechanism for requesters to access e-documents from various repositories in real-time using URI (Uniform Resource Indicator).DigiLocker Portal: Dedicated cloud based personal storage space, linked to each resident's Aadhaar for storing e-documents, or URIs of e-documents.To know full details about the technical specifications of DigiLocker, please click here.Q) What is the sign-up and sign-in procedure for DigiLocker? Can I link my Google or Facebook to DigiLocker?A) While signing up for a DigiLocker account, it is mandatory for a user to have an Aadhaar (UIDAI) number. A one-time password or OTP is sent to the users Aadhaar-linked mobile number, which they need to sign-up.For log-ins thereafter, a user can set a password of their choice, or link the account to their Facebook or Google logins. The choice of linking DigiLocker with Google or Facebook is given to every user, and is left to their discretion. It is not necessary to link them.Here is video explaining the sign-in and sign-up processes:Q) Can an NRI (Non Resident Indian) sign up using a foreign mobile number?A) No, it is not possible. You can register in DigiLocker using an Indian mobile number only.Q) Once I sign-up for DigiLocker, How can I get my eAadhaar linked with my account?A) Here are the steps to get eAadhaar in DigiLocker:Login to DigiLocker with your credentials.After logging into DigiLocker, you will see a dialog box with a message to get your eAadhaar.Click on "Click here" link.An OTP box will appear in the dialog.You will receive an OTP on your mobile number linked to Aadhaar.Enter this OTP in the OTP box and click "Verify OTP" button.On successful validation of the OTP you will be redirected to "Issued Document" page where URI for eAadhaar will be listed.Click on "Save" icon next to Aadhaar Card on "Issued Document" page. Your eAadhaar will be saved to "Uploaded Document" section.Q) Is DigiLocker only accessible through a web browser? Does DigiLocker have a Mobile App? What platforms is it available on?A) DigiLocker is available both for the web, as well as mobile. This means, a user can access their DigiLocker account both, from a web or mobile browser, as well as the DigiLocker Mobile App.The DigiLocker Mobile App (mobile application) is available on Google Play Store and iOS App Store. Click on the links in this answer, while on your mobile phone, to download the DigiLocker App.Q) What are the rules and amendments to use DigiLocker?A) To know all about the rules and amendments of DigiLocker, please click here. The first 8 pages are in Hindi. For English, please go straight to page 9.Q) How do I upload and e-sign documents on DigiLocker?A) Here is a video explaining the entire process of uploading and e-signing documents on DigiLocker:Q) How do I get documents issued on DigiLocker?A) Here is a video explaining the entire process of getting documents issued on DigiLocker:Q) What is DigiLocker integration with Ministry of Road Transport and Highways (MoRTH). What are the benefits of this integration for citizens?A) DigiLocker has partnered with the Ministry of Road Transport and Highways for making available digital driving license and vehicle registration certificates to Indian citizens. Under this partnership, DigiLocker is now directly integrated with the National Register, which is the national database of driving license and vehicle registration data across the country. Henceforth, DigiLocker users will be able to access their digital RC and DL both on desktop computers and on mobile devices.Here are the benefits of this integration:Paperless Services: Digital driving license and vehicle registration will minimize the use of physical documents.Authentic Records: Citizens can share the authentic digital certificates directly from the data source with other departments as identity and address proof resulting in reduction of administrative overhead.Spot Verification: The digital RC and DL in a DigiLocker account can be spot verified for authenticity either by validating the Digital Signature of MoRTH on the PDF copy of the document or by scanning the QR code on digital documents by using the QR scan facility on DigiLocker mobile app.Q) What is the process of getting my digital DL (driving license) and RC (registration certificate) in DigiLocker?A) For getting the digital RC and DL, users should ensure their Aadhaar number is linked with their DigiLocker account. Once this is done, they can go to the "Pull Partner Documents" section, select the issuer and document type and enter the document details asked for. This will allow them to fetch their document from the transport ministry database. Once the document is fetched, users can save a permanent link (URI) to this digital document in their "Issued Documents" section for later reuse.While fetching the transport ministry digital records in DigiLocker, your name in your Aadhaar card should match your name in the RC and DL database of the National Register. This ensures that only the rightful owner of the documents is able to fetch the digital DL and RC.Please click here to get a step by step demo for the process of getting the digital RC and DL.Citizens can get their Digital RC and DL on both desktop and on mobile devices (Android only at present, iOS coming soon.)Q) How can I be sure that the Digital RC and DL in DigiLocker is indeed coming from the transport ministry database? Are these digital records authentic and legally valid under Indian laws?A) The digital RC and DL in DigiLocker is digitally signed by Ministry of Road Transport and Highways. It is fetched in real-time directly from the National Register database and has a timestamp for record keeping purposes. This digital document is a legally valid document under the Indian IT Act 2000.Q) How can a CBSE Class XII student get access to their digital mark sheet on DigiLocker?A) DigiLocker has partnered with CBSE for issuing digital mark sheets to 2016 Class XII students. Students who have registered their mobile number with CBSE would receive their DigiLocker account credentials through SMS, while those who don't have their mobiles registered with CBSE would need to create a DigiLocker account with their mobile number, sync with their Aadhaar number and then pull their mark sheet from the CBSE databases.For step by step instructions on how to do this, please click here.Q) What are issued documents and what are uploaded documents?A) Issued documents are e-documents issued by various government agencies in electronic format directly from the original data source and the URI (link) of these documents is available in the issued documents section of DigiLocker. Whereas uploaded documents are those e-documents uploaded directly by the DigiLocker user.Q) What is the maximum allowed file size that can be uploaded?A) Maximum allowed file size is 10MB.Q) What type of files can be uploaded?A) File types that can be uploaded - pdf, jpeg & png.Q) What is the meaning of URI?A) A URI is a Uniform Resource Identifier generated by the issuer department, which is mandatory for every e-document of the DigiLocker system. This unique URI can be resolved to a full URL (Uniform Resource Locator) to access the actual document in its appropriate repository.Q) What departments under the government have linked themselves to DigiLocker so far? What advisory has the government given to the states to officially recognise soft copies (on DigiLocker)?A) Here is the letter or advisory that the government has issued to all the states to officially recognise documents of citizens uploaded or fetched on DigiLocker. The letter also lists all the government departments that have linked themselves to DigiLocker.
-
What types of websites are most likely to contain viruses or malware?
What types of websites are most likely to contain viruses or malware? Websites that sell ads from real-time ad broker networks. By far, by far, the most common way for viruses and malware to be spread from Web sites is through poisoned ads.What is the most dangerous website?So be careful when you visit these sites, since your computer may not come out in good health, after your visit.#1 Ucoz. com. Description: Site hosting. Global rank in malware hosting: 14.#2 sapo .pt.#3 Amazonaws .com.#4 Blogspot .de.#5 4shared .com.#6 sendspace .com.#7 comcast .net.Can certain websites cause viruses?Yes, it's entirely possible to get infected by simply visiting a website. Most commonly via what we call "Exploit Kits". Right now, EK are used to deliver a lot of dangerous malware (such as banking trojans and Cryptoware) to computers worldwide. So using a standard Antivirus and Antimalware won't cut it.Can you get a phone virus from a website?How phones get viruses. The most common way for a smartphone to get a virus is by downloading a third-party app. However, this isn't the only way. You can also get them by downloading Office documents, PDFs, by opening infected links in emails, or by visiting a malicious website.Threat 1 >> Malicious Flash files that can infect your PCThe Place: Websites that use FlashsignNow's Flash graphics software has become a big malware target in recent years, forcing the company to push out frequent security patches. But another danger you might not know about is associated with Flash cookies. Flash cookies are small bits of data that their creators can use to save Flash-related settings, among other things. But like regular cookies, Flash cookies can track the sites you visit, too. Worse still, when you delete your browser's cookies, Flash cookies get left behind.If You Have to Go There: To help protect against Flash-based attacks, make sure you keep your Flash browser plug-ins up-to-date. And you can configure the Flash plug-in to ask you before it downloads any Flash cookies.Threat 2 >> Shortened links that lead you to potentially harmful placesThe Place: TwitterScammers love Twitter since it relies so much on URL shorteners, services that take long Internet addresses and replace them with something briefer.And it's very simple to hide malware or scams behind shortened URLs. A shortened link that supposedly points to the latest Internet trend-du-jour may be a Trojan horse in disguise.If You Have to Go There: Simply don't click links. Of course, that takes some of the fun out of Twitter. The other option is to use a Twitter client app. TweetDeck and Tweetie for Mac have preview features that let you see the full URL before you go to the site in question.Some link-shortening services, such as Bit.ly, attempt to filter out malicious links, but it seems to be a manual process, not an automatic one. TinyURL has a preview service you can turn on.Threat 3 >> E-mail scams or attachments that get you to install malware or give up personal infoThe Place: Your e-mail inboxAlthough phishing and infected e-mail attachments are nothing new, the lures that cybercrooks use are constantly evolving, and in some cases they're becoming more difficult to distinguish from legitimate messages. My junk mailbox has a phishing e-mail that looks like a legitimate order confirmation from Amazon. The only hint that something's amiss is the sender's e-mail address.If You Have to Go There: Don't trust anything in your inbox. Instead of clicking on links in a retailer's e-mail, go directly to the retailer's site.Threat 4 >> Malware hiding in video, music, or software downloadsThe Place: Torrent sitesTorrent sites (such as BitTorrent) are often used for sharing pirated music, videos, or software, and are a trove of malware. No one vets the download files--they may be malware in disguise.Ben Edelman, privacy researcher and assistant professor at Harvard Business School, thinks torrent sites are the most dangerous places to visit, since they don't have a business model or reputation to defend (by comparison, many porn sites rely on being deemed trustworthy). "The [torrent] customers, they really don't want to pay," he says.If You Have to Go There: It's probably best to avoid torrent sites entirely, given their untrustworthy content, but if you must visit, use a secondary PC to protect your main system. Use antivirus software, and keep it updated. Scan downloaded files and wait a couple of days before opening them. Brand-new malware can be tricky to catch, but the delay in opening may allow your antivirus software to get the necessary signatures.Threat 5 >> Malware in photos or videos of scantily clad womenThe Place: ‘Legitimate' porn sitesPorn sites have a reputation of being less secure than mainstream sites, but that assumption doesn't tell the whole story. "There is no doubt that visiting Websites of ill-repute is deadly dangerous. If you make a habit of it, it's a given that you'll be attacked at some point," says Roger Thompson, chief research officer with security firm AVG. "Unfortunately, staying away from those sites won't keep you safe by itself, because innocent sites get hacked all the time, and are used as lures to draw victims to the attack servers."And as mentioned earlier, many porn sites operate as actual, legitimate businesses that want to attract and retain customers. That said, it may be hard to tell the "legit" porn sites from malware-hosting sites that use porn as a lure.If You Have to Go There: Be suspicious of video downloads, or sites that require you to install video codecs to view videos (see the next threat, below). Using tools like AVG's LinkScanner and McAfee's SiteAdvisor (or SiteAdvisor for Firefox) can help you weed out the malicious sites.And, again, consider visiting such sites on a secondary machine. You don't want your browser history on the family PC.Threat 6 >> Trojan horses disguised as video codecs, infecting your PC with malwareThe Place: Video download sites, peer-to-peer networksIf you watch or download video online, you've likely been told to download a video codec--a small piece of software that provides support for a type of video file--at least once. Usually, these bits of software are perfectly legitimate (for example, the popular DivX codec), but some less-than-reputable download services or video sites may direct you to download a piece of malware disguised as a codec. Security software company Trend Micro provides a good example of what these attacks look like.If You Have to Go There: Your safest option is to stick with well-known video sites such as YouTube and Vimeo. And for catching up on the latest episodes of your favorite TV shows, sites and services like Hulu, http://TV.com, ABC Home Page - ABC.com, and iTunes are safer than peer-to-peer networks.Threat 7 >> Geolocation--your smartphone and perhaps other parties know where you areThe Place: Your smartphoneThe smartphone market is still in its infancy, really, and so are the threats. One possible concern is the use--or abuse--of geolocation. Although plenty of legitimate uses for location data exist, the potential for inappropriate uses also exists. In one case, a game listed on the Android Market was in reality a client for a spy app. In a less invidious example, a site called Please Rob Me showed that--for a time--a stream of FourSquare check-ins indicated that a person was away from their home (the site's goal, mind you, wasn't to condone theft, but to raise awareness of the issue).Apple recently updated its privacy policy to reflect changes in how it handles location data in iOS 4. The policy now states that "to provide location-based services on Apple products, Apple and our partners and licensees may collect, use and share precise location data." You can read more on Apple's new privacy terms and what they mean for you.If You Have to Go There: Be particular about the location-based sites, apps, and services that you use. As shown in the screenshot at right services such as Yelp provide good examples of useful location-aware apps. On the other hand, weigh the privacy implications of services like FourSquare or the new Facebook Places feature, and consider how much you feel comfortable divulging. (Read more on how to retain privacy on FourSquare and Facebook Places.)Threat 8 >> 'Poisoned' search engine results that go to malware-carrying WebsitesThe Place: Search enginesSearch engine poisoning is the practice of building tainted sites or pages that are designed to rank high in a search on a given topic. For example, according to a recent study by the security firm McAfee, 19 percent of search results for "Cameron Diaz and screensavers" had some sort of malicious payload. Breaking news topics and Facebook are also common search targets for attackers.If You Have to Go There: Pick and choose which sites to go to. Don't just blindly click search results; check each URL first to make sure that it really leads to the site you want.Threat 9 >> Malicious PDFs that try to fool you into installing malwareThe Place: Hacked Websites, plus your inboxAs Microsoft has become more serious about Windows security over the past few years, would-be attackers have had to find new ways to infect PCs. Attacking flaws in signNow is one of these newer methods. So-called poisoned PDFs are PDF files that have been crafted in such a manner that they trigger bugs in signNow and signNow; posted on a hijacked Website, they may let an attacker commandeer your PC and access your files and personal info.A newer variant takes an otherwise innocent-looking PDF document and inserts malware into it. signNow may pop up an alert asking if you want to run the malware, but hackers can edit those messages to trick you into opening the file.How serious is this problem? In 2009, attacks using malicious PDFs made up 49 percent of Web-based attacks, according to security firm Symantec.If You Have to Go There: First, always make sure that you're running the latest version of signNow.Threat 10 >> Malicious video files using flaws in player software to hijack PCsThe Place: Video download sitesAttackers have been known to exploit flaws in video players such as QuickTime Player and use them to attack PCs. The threats are often "malformed" video files that, like malicious PDFs, trigger bugs in the player software that let the attackers in to spy on you, plant other malware, and more.If You Have to Go There: Keep your player software up-to-date. Apple and Microsoft periodically release patches for QuickTime and Windows Media Player, respectively. Avoid downloading videos at random. Stick to well-known video sites such as YouTube, or to download services like iTunes.Threat 11 >> Drive-by downloads that install malware when you visit a siteThe Place: Hacked legitimate sitesA drive-by download occurs when a file downloads and/or installs to your PC without you realizing it. Such downloads can happen just about anywhere. Some sites are built to lure people into a drive-by download; but in a common attack method, criminals will hack a Web page, often on an otherwise legitimate site, and insert code that will download malware to your computer.If You Have to Go There: The first thing to do is to keep your security software up-to-date, and to run regular malware scans. Many security suites can flag suspicious downloads.Threat 12 >> Fake antivirus software that extorts money--and your credit card informationThe Place: Your inbox, hacked legitimate sitesFake antivirus programs look and act like the real thing, complete with alert messages. It isn't until you realize that these alerts are often riddled with typos that you know you're in trouble.Most fake antivirus software is best described as extortionware: The trial version will nag you until you purchase the fake antivirus software-which usually does nothing to protect your PC. Once you send the criminals your credit card information, they can reuse it for other purposes, such as buying a high-priced item under your name.Threat 13 >> Fraudulent ads on sites that lead you to scams or malwareThe Place: Just about any ad-supported WebsiteHey--ads aren't all bad! They help sites pay the bills. But cybercriminals have taken out ads on popular sites to lure in victims. Last year, the New York Times site ran an ad from scammers, and earlier this year some less-than-scrupulous companies were gaming Google's Sponsored Links ad program and placing ads that looked like links to major companies' Websites."The bad guys have become very clever at exploiting online advertising networks, tricking them into distributing ads that effectively load malicious content--especially nasty, scaremongering pop-ups for rogue antispyware," says Eric Howes, director of research services for security firm GFI Software.If You Have to Go There: Most large sites, such as PCWorld - News, tips and reviews from the experts on PCs, Windows, and more, have ad sales departments that work frequently with a core group of large advertisers, so it's probably safe to click a Microsoft ad on the New York Times site. But as the Google Sponsored Links incident shows, nothing is entirely fail-safe.Threat 14 >> Questionable Facebook appsThe Place: FacebookFacebook apps have long been an issue for security experts. You don't always know who's developing the apps, what they're doing with the data they may be collecting, or the developers' data security practices. Even though you have to approve apps before they can appear on your profile and access your personal information, from there the security of your data is in the developer's hands.If You Have to Go There: Be selective about the apps you add to your profile--don't take every quiz, for example. Check your privacy settings for Facebook apps, as well: Click the Account drop-down menu in the upper-right corner of Facebook's site, select Privacy Settings, and then click Edit your settings under ‘Applications and Websites'. There, you can control which apps have access to your data, and which of your friends can see what information from apps (such as quiz results); you can also turn off Facebook apps altogether.Threat 15 >> Sites that lure you in, get you to sign up, then sell your e-mail address for spamThe Place: 'Free electronics' sitesYou've no doubt seen sites around the Web blaring, Get a free iPad! Get a free notebook! A free iPod! It's easy! These sites aren't typically dangerous in the classical sense--you probably won't get infected with malware--but your personal information could be sold to other businesses, who can then use it to sell more stuff to you.If You Have to Go There: Read the privacy policies. And then read them again. Also, beware of privacy policy loopholes--even though a site says that it won't sell your private data to third parties, depending on the language of the policy, they may still be able to give your information to "affiliates."Threat 16 >> Phishing 2.0 on social networks that tricks you into downloading malware or giving your Facebook login information to a criminalThe Place: Social networksQuestionable Facebook apps and malicious shortened links aren't the only dangers lurking on social networks. Sites like Facebook have given rise to new forms of phishing. Scammers might hijack one person's Facebook account, then use it to lure that person's friend into clicking a malicious link, going to spam sites, or giving up their Facebook login information--thereby giving scammers one more Facebook account to hijack."One of the bigger dangers currently facing users is malware, adware, and spyware spread through social networks like Facebook and Twitter," says Eric Howes, director of malware research with Sunbelt Software. "Users may receive spam via these networks offering them free deals, links to interesting videos, or even widgets to enhance their Facebook profiles. In many cases what's really being pushed on users is adware, spyware, or even malicious software that can exploit users' PCs."If You Have to Go There: Don't trust every link posted to Facebook, even if one of your friends posted it. Be especially suspicious if the post is out of the ordinary for that person. Check the person's wall or Twitter @-replies to see if anyone is concerned that the person's account has been compromised.And if you suspect that your account has been hijacked, change your password immediately. Both Facebook and Twitter have resources to help you keep up-to-date on the latest threats on both sites. Facebook users should visit its security page; if you're on Twitter, be sure to follow @spam and @safety for Twitter security best practices.Threat 17 >> Oversharing--exposing too much personal information on your social network profilesThe Place: Social networksHow many times have you seen friends on Facebook or Twitter publicly divulge a bit more information than is necessary? Oversharing isn't just a matter of getting a little too personal--it can leave your private information viewable to the general public. But it's avoidable."There is a subtle danger that few people understand with the social networking sites, and that is the idea of information leakage," says AVG's Roger Thompson. "People, particularly teens, put all sorts of information online, without realizing that many more people than just their friends can see that data."Oversharing could very well lead to more serious privacy issues further down the road, Thompson adds. "As today's young teens signNow an age to apply for a credit card, I fully expect an onslaught of fraudulent card applications on their behalf, because they unwittingly divulged so much information. Harvesting is going on now, and we have no idea who is doing the harvesting."If You Have to Go There: This particular threat is relatively easy to avoid, in that a little common sense can go a long way: Just be mindful of what you post. Do you really need to publish your home address and phone number to your Facebook profile?Finally, be certain to check your privacy settings to make sure that you're not divulging your deepest, darkest secrets to all 500 million Facebook users.
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
How to sign a pdf in paint?
How does esign work banks?
Get more for Share Electronic signature PDF Android
- eSignature Tennessee Residential lease agreement Easy
- Can I eSignature Washington Residential lease agreement
- How To eSignature Vermont Residential lease agreement form
- How To eSignature Rhode Island Standard residential lease agreement
- eSignature Mississippi Commercial real estate contract Fast
- eSignature Arizona Contract of employment Online
- eSignature Texas Contract of employment Online
- eSignature Florida Email Contracts Free
Find out other Share Electronic signature PDF Android
- Older adult full service partnership department of form
- Office use onlyclient no date receivedapplicat form
- Self assessment guide for residence in new zealand 1003 form
- Asia pacific economic cooperation business travel card form
- Form 456 australia short stay business visa bapplicationb form bb
- Form1419 hebhebrewapplication for avisitor visa
- Asthma action plan for school children year 20 form
- Nc dhhs contactnc dhhs contactnc dhhs contactnc dhhs public health form
- Basic patient information
- North carolina only form
- Consent and acknowledgement for cdl nc department of health ncdhhs form
- Professional endorsement form cce global
- Dma 5097 ia form
- Afo measurement form 403148906
- Dma 5202c ia pdf designation of authorized representative appendix c form
- Elect state continuation coverage form
- Adult client information form keira oseroff psychotherapy
- Request for search of putative father registry form 3961 revised 02
- Grady health system marcus stroke and neuroscience form
- Marta mobility application fill online printable fillable form