CloudTrust eSigning Made Easy
Do more on the web with a globally-trusted eSignature platform
Standout signing experience
Reliable reporting and analytics
Mobile eSigning in person and remotely
Industry regulations and conformity
Cloudtrust esigning, faster than ever
Useful eSignature extensions
See airSlate SignNow eSignatures in action
airSlate SignNow solutions for better efficiency
Our user reviews speak for themselves






Why choose airSlate SignNow
-
Free 7-day trial. Choose the plan you need and try it risk-free.
-
Honest pricing for full-featured plans. airSlate SignNow offers subscription plans with no overages or hidden fees at renewal.
-
Enterprise-grade security. airSlate SignNow helps you comply with global security standards.

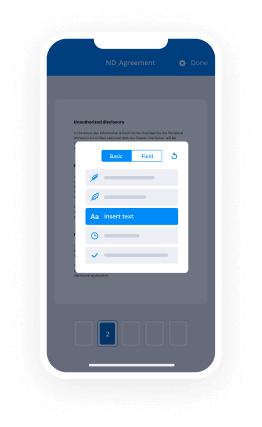
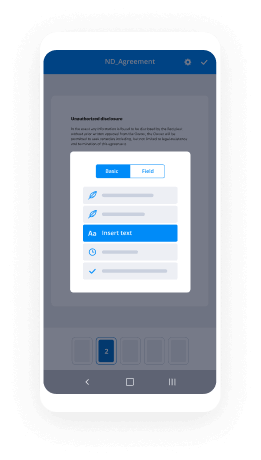
Your step-by-step guide — cloudtrust esigning
Leveraging airSlate SignNow’s eSignature any business can accelerate signature workflows and sign online in real-time, supplying an improved experience to clients and workers. Use CloudTrust esigning in a few easy steps. Our handheld mobile apps make work on the go achievable, even while offline! Sign contracts from any place worldwide and make deals quicker.
Keep to the walk-through guideline for using CloudTrust esigning:
- Log in to your airSlate SignNow profile.
- Locate your needed form within your folders or import a new one.
- Open the record and make edits using the Tools list.
- Drag & drop fillable areas, add text and sign it.
- Add numerous signers using their emails configure the signing order.
- Indicate which individuals will get an signed doc.
- Use Advanced Options to reduce access to the template and set up an expiry date.
- Click on Save and Close when finished.
Moreover, there are more extended capabilities accessible for CloudTrust esigning. Include users to your shared workspace, view teams, and track teamwork. Millions of customers across the US and Europe agree that a system that brings everything together in a single unified work area, is what enterprises need to keep workflows working smoothly. The airSlate SignNow REST API allows you to integrate eSignatures into your app, website, CRM or cloud storage. Try out airSlate SignNow and enjoy quicker, smoother and overall more effective eSignature workflows!
How it works
airSlate SignNow features that users love
See exceptional results CloudTrust esigning made easy
Get legally-binding signatures now!
FAQs
-
What program allows you to sign documents?
airSlate SignNow is an electronic signature app created by Citrix. Like most eSignature apps, airSlate SignNow allows you to upload, prepare, and send documents for signature\u2014as well as receive them, sign them, and return them to another sender. -
How do I digitally sign a document?
Click the File tab. Click Info. Click Protect Document, Protect Workbook or Protect Presentation. Click Add a Digital Signature. Read the Word, Excel, or PowerPoint message, and then click OK. -
How do I do an electronic signature?
Draw your signature using your finger or a stylus. If you have access to a touchscreen, you can use your finger to create an electronic signature directly in your document. ... Upload an image of your signature. ... Use your cursor to draw your signature. ... Use your keyboard to type in your signature. -
How can I sign documents for free?
Choose a File to Sign. Choose the document you want to have electronically signed online. ... Set Signer Details. Register the signer's name and email address. ... Send for Signature. Your signer will receive an email requesting their signature. ... Sign and Download. -
How do I get documents signed online?
Sign up for a free trial at airSlate SignNow, and then log in. Select New > Sign a Document, and then upload the electronic document. Select Sign and then follow the steps to electronically sign your document. -
How can I sign a document on my phone?
Suggested clip Signing a Document on Android - YouTubeYouTubeStart of suggested clipEnd of suggested clip Signing a Document on Android - YouTube -
What app allows you to sign documents?
airSlate SignNow's mobile app for Android empowers you to sign documents and get signatures from anyone, anywhere. You can sign any document free, directly from your device. There are hundreds of ways to use airSlate SignNow's mobile app. -
How do I get an e signature from someone?
Open a PDF file in Acrobat DC. Click the Fill & Sign tool in the right pane. Add a recipient: Enter an email address and add a custom message if you want. ... Create your form and signature fields: ... Send your form:
What active users are saying — cloudtrust esigning
Cloudtrust esigning
[UPBEAT MUSIC PLAYING] SAM LUGONI: Hi, everyone. Welcome to our session, "A Use-Case Based Approach to G Suite Security." I'm Sam Lugoni, I lead the PMM for G Suite security and with me is Brad, who looks after endpoint management for G Suite security. This session is a little different. We'll barely spent about five minutes on slides and then the majority of the time, 45 minutes, is actually going to be spent on use cases. We've gone ahead and asked customers on what their top security use cases are and we're going to try to solve them within G Suite. So your feedback is really important because if you feel the examples are going to be helpful to you, let us know. If you feel that they're not very useful and you want more slides, let us know as well and we can make changes for next year. Now, often we see customers suffer due to phishing attacks. 91% of attacks start with a phishing email and that's been there for a while. There's been a 15x increase in ransomware over the past few years and employee negligence is having a big part to play in data breaches. And as a result, it's really hard for an admin to really secure an organization because oftentimes they don't really have the necessary controls. And even at the user level we're at times missing the right controls and the right notifications for people to make the right judgment call on whether this email, for example, constitutes an attack or not. And that's where Google comes in. We start within the cloud, we run on the cloud, and that's why we understand the implications of powering a business in the cloud. All our Enterprise services run on the same infrastructure as the rest of Google. And we use the protections we've built at Google for Enterprise services as well. Now, in security, scale matters, and it matters a lot. Every minute 10 million spam messages are prevented from reaching Gmail customers, and we go through about 700,000 pages for harmful content. Now, once we get all these security signals and the security data we're able to construct much better machine learning models to figure out what an attack looks like in the making. Because here's how a phishing attack typically works. An attacker would send out a small set of emails to test out an attack to figure it out that attack is even going to be successful. And if it is, then the attacker will launch a much wider campaign targeting a much wider base. So to understand the attack when it's been tested to figure it out the defenses and to be able to proactively stop that is something which we can do really well. Now, when we think of security within G Suite, there's three big areas of focus. The first one is reducing risk with insights because in large corporations admins can receive about 5,000 alerts every day, and almost half of them are not investigated. So our goal is to provide you with those three, four, five alerts which are actionable, which you can directly do stuff about, and not bombard you with a ton of useless alerts. The second thing is that admins are overburdened. We want to make sure that the protections we are building are turned on by default as much as possible so you don't have to come in and configure everything around a certain protection being available. And we've had zero reported or detected account hijackings after security deployments. That is really, really strong because it helps you protect your users against phishing. Now, beyond all that, at the end of the day we can design the best security features but if they're not being used, they're kind of useless. So we want to make sure that those features are simple, easy to use, which you can deploy right away. Now, imagine a large organization or a small organization such as yours. Now, when you unbox G Suite for the first time, we have default-on mobile management, which means that as soon as any device accesses G Suite data through G Suite [? credentials ?] on a Google app, you will get basic controls on that device right away. On mobile devices that would mean being able to wipe accounts, and on desktop devices that would mean being able to see [INAUDIBLE] devices as well as log people out if needed. And Brad's going to show you a demo of this as well. Advanced anti-phishing is turned on by default because in a large organization, there's always a mix of people. Some people might be very well in tune with what's happening on the security side and some may not. And we want to protect everyone so the protections we have around Gmail are turned on so as soon as you unbox G Suite, you will get those protections right away. Yesterday at the keynote we launched the Advanced Protection Program. I'll talk a bit more about that and show you a quick demo as well. And then we have the Security Center for G Suite, which is a one-stop shop for prevention, detection, and remediation. And really those three things are the holy grail. If you can do prevention, detection, remediation in one place, it really helps solve a lot of things. For eDiscovery we have something which is called Vault where you can set retention policies as well. So that's all the slides I had and now we're going to move to the use-case based demos. So here we have the top questions we've gotten from customers and we'll attempt to solve them within G Suite. The first question we get from customers is that, how do I configure my new organization to best protect my data? Let's move to Demo 1, please. Great. So within-- this is the Admin console. This is an organization called Inc42, and I'm logged in as a super admin. The first thing I want to talk about is security health. Now, with security health we're going through all the different security settings within G Suite and we're mapping them to Google's best practice recommendations. The settings where we think you've configured them correctly get this nice green checkbox and the settings with which we feel could be configured in a slightly better way get this recommendation as to why we think you should maybe consider changing the setting. Some of these settings we don't change automatically for you because they might be very specific to your organization. Now, one of the settings which is turned off here is this out of domain warning. That's turned-- that should be turned off for the entire organization. So I'm going to refresh this page, and the out of domain warning is turned off for the entire organization, which means that if someone is trying to share a file outside the organization-- this is an internal-only road map and I'm going to share it with someone outside the organization. It doesn't really show a warning, and that's a problem because employees, at times, might unknowingly share things outside. And as much as possible, you want to provide employees with notifications so that they're in a better place to figure out if this thing actually should be shared outside or not. So from within the security health tool, we can directly go to the setting which talks about out of domain warning, and right now it's turned off and we're going to turn it on. Then we are going to refresh the security health tool to see that the setting has taken effect or not. And now we see this beautiful green checkbox which says that the out of domain warning is turned on for the entire organization. So now it still might take a few minutes to propagate through all the files. But we'll try sharing this file outside the organization again, and this time I get an alert saying that you're sharing to a domain which is external to the organization. Are you sure you want to share this file? And these prompts are really helpful to employees to figure out if they're making the right decision on file sharing. Next up, part of the security center are these dashboards. And when you're unboxing G Suite for the first time, it's nice to be able to look at these dashboards and see what's happening within the organization right away. So for example, this is the phishing dashboard. We've seen a few spikes coming in last couple of days. We can click on these spikes and we see there have been some phishing emails which we have detected and those have automatically been sent to the spam folder, deleted, or quarantined based on the policies you have set. Now, next up-- let's go back to the slides, please. The next question we get from customers is that, how do I help ensure that G Suite satisfies my organizational policies? To Demo 1 again. Earlier this year we launched a product called Access Transparency. Now, with Access Transparency any time a Googler accesses your G Suite data you will get a notification as to what data was accessed, why that data was accessed, whether there was a support case which you generated because of which that access happened, what the actor's home office was, and the specific file of the specific user which was accessed. This you can use for your audit records. The other thing I want to talk about is data regions. Now, with data regions you can pick the location where your G Suite data should be hosted at rest. By default, that data is geographically located, but you can pick whether you want that data to be located just within Europe or just within the US. And the beautiful thing about this is that you can do it based on OU. So for example, maybe your marketing OU should only be located within the US but your finance OU should be located in Europe. So here are the settings we have within the admin console for data regions. I can pick finance and I see that's located in Europe, and HR is located within the US. So based on how your organization is geographically located, you can make those choices. We enable you to track all this in a dashboard because we think it's really important for you to track progress of the move. Now, as we were designing data regions, migration was a really, really important criteria which we thought of very well before we launched this feature. So most of the products which you will see out there, including other collaboration solutions, when you move data from one place to another there is downtime. Now, G Suite at the core-- for us collaboration is really important, so when we were designing this feature, we wanted to ensure that no matter how often you move your data or how many users you're moving from one location to the other, we do not have any downtime. So as your data, for example in this case, is being moved from the US to Europe, your users will still be able to collaborate the same exact way as they were earlier. The other thing is that employees move organizations within the company. So as an employee is moving from one organization to the other, maybe they're moving from finance to HR, their data automatically follows them so you as an admin don't have to do additional things to make sure that data is located again and again and again. And this way-- this is a simple way we're reducing the burden on the admins. Back to the slides, please. So next up, what should I do when I see suspicious activity? And then back to Demo 1. So here we logged into the alert center for G Suite, which is a one-stop shop to see all the important alerts which are there with G Suite. Now, one of the alerts we see is a suspicious device activity which happened a couple of weeks back. The severity of this alert is pretty high. So I can click on this alert and see that there is a device, it's a Chrome device, and Marissa owns that device which has displayed some suspicious activity. So I want to investigate what's happening behind the scenes. I can click on Investigate Alert, which directly takes me to the security investigation tool where all this queries are a pre-fed. So I know, for example, that Marissa's device, there's been some activity there. But by experience I also know that a lot of this happens because of phishing, so now I want to see if lately Marissa has received any emails which we tagged as suspicious. So I can click on Marissa and I can see all the emails which she has received that have been-- that we tagged as suspicious, and there's one such email. It says action required, verification of pension account. Now, I'm a super admin here and I can even see the message which Marissa received, but before I see the message, we want to make it very clear that there has to be justification as to why you want to see a user message. So as an admin, you have to enter the justification so that later we can audit any access which happens on G Suite accounts. So once I enter the justification, I can see the message. I can see there's an attachment. I also see the SHA hash on this. So if you have other [? AV ?] tools, other malware tools, you can actually download the attachment and run it there as well. Now, here's my concern. If Marissa received this email, it might be a symptom to a much wider attack happening within my organization. So I can click on the subject line and I can pivot, and I can see everyone within my organization that has received the exact same email. And a lot of people have. There's about 20 people who have received this exact same email. First step, I want to make sure that these emails disappear from users' inboxes. So I can select all these emails. I can proactively delete them from users' inboxes. You can't go back on this, so we require people to enter "delete 20 messages" to make sure that you actually-- to make sure that you actually want to do this operation. Now, once I've deleted emails-- I'm really the expert on phishing, but I don't really know data exfiltration that well. So within the security center now, you can share investigations with other admins. And this is really-- the genesis of this is what we gather from G Suite. Now, G Suite does collaboration really well. We want to take the best of what G Suite offers in collaboration and bring it to the admin world because what's happening today is admins still share screenshots with each other. We're still sending documents to each other, and that's not the most effective way to collaborate on security issues. So now within the security center, you can share investigations and work on investigations together with each other. So here I'm going to share this investigation with Chad. I'm going to ask Chad to look at data exfiltration. Now, this is Chad's admin console, and Chad has a fascination for beanies. It suits the weather in London, as well, so I'm gonna just wear one for a bit. I'm Chad for the next 2 minutes. I'm logged into the admin console and I see an email from Sam coming in which says that, well, there's an open investigation and can you take a look at data exfiltration. So with a click I can open this investigation, which directly takes me to the admin console. And I'm at the exact same place Sam was at in his investigation. So I can see right here that Sam's already figured out that the cause of this was a phishing email, and he's already proactively deleted these phishing emails from users' inboxes. And now I have to take a look at data exfiltration. So I can look at all these users who have been compromised. And I can pivot on these users and see all the different files where the visibility change has been previously internal to now external, so any file which has been shared outside the organization. I can select all these files and with a few clicks, I can audit these file permissions. And I can select these files and limit file sharing to only within the organization. Now I can, of course, do more and figure out if a specific user shared a file externally or not, and all that can happen within the investigation tool. Back to the slides, please. The next question we get from customers is, what is the best protection against phishing and how do I configure it? And we go back to the demo. So the beautiful thing about G Suite is that most of the protections we have built around phishing are turned on by default within the admin console. So here you can see that we're already protecting it against encrypted attachments. We're also protecting against spoofing of employee names and domains. And here we do a cool thing, which is that we're not just comparing whether an email coming from the outside matches an employee name, we're figuring it out if an email which is coming from the outside, from an individual, if that individual's name is similar to someone within the organization, we flag it to the employee. And there might be nothing wrong with the email, but we want to present those pointers to employees such that they can make better decisions on what's really happening behind the scenes. So in some ways, it's about educating employees so that they get better over time at figuring out what these attacks look like. And here's an example. So here there's an email coming in from Mike Chang at yahoo.com. There's a Mike which works within the company as well, and we present a banner which says, be careful with this message because Mike Chang's name is someone-- is similar to someone within your organization. And these really help employees make the right decision because at the end of the day, we have a few admins managing a large organization. So we have to empower users to make the right decision so that they can become part of the security ecosystem with the admins. Next up I want to briefly talk about security sandbox. This is something which we launched earlier this year. Now, security sandbox is disabled for this domain right now. I'm just going to turn it on, but what we do within the security sandbox is if we find any attachment within Gmail to be suspicious, we take that attachment, we spin up a live virtual machine, and we [? detonate ?] that attachment within that virtual machine to see what it's really doing behind the scenes. So if an attachment is trying to do some system calls, we can flag that. And really here the emphasis is to figure out what would happen if an employee was to actually download that attachment on their machine and prevent issues from happening much earlier. And this is available as part of G Suite. The final thing I want to talk about is the advanced protection program, which we launched in [? Suzanne's ?] keynote yesterday morning. Now, the advanced protection program has been available on Google consumers for the past few years. And it's really designed to protect high-risk, journalists, activists, people who run campaigns, et cetera. And it's the strongest protections we've built at Google. We're taking this core concept and we're bringing it to G Suite and Cloud Identity. As an admin, you can enable the advanced protection program and as users self-enroll into that program, they will be protected by a very high degree of security. There's a couple of things which we do within the advanced protection program. The first, and maybe the most important one, is enforcing security keys. And we have our own Titan key available as well, or you could use third-party keys. Now, with security keys we've had zero reported or detected account hijackings after security key deployments. That's a really, really strong stat. The second thing we do as part of the advanced protection program is we limit [? OAuth ?] access to only the apps which you've trusted as an admin. No other app will get G Suite data unless you've explicitly trusted it. And the third thing is enhanced email scanning. We automatically turn on the security sandbox for users enrolled as part of the advanced protection program. Now, once you enable users as part of the advanced protection program, they can go to this link. And there's a very easy way to get started with the advanced protection program. The setting is still taking effect. I'm going to refresh this page. And once the permissions come through, your domain will be allowed to enroll and users will be able to enroll by using security keys as part of the advanced protection program. So with that, I would hand it over to Brad to walk us through some of the other use cases which we get from customers. BRAD MEADOR: OK. Could we go back to the slides, please? OK, my name is Brad Meador. I'm the product lead for Google endpoint management. I'm going to walk you through four demos in about 25 minutes or so. So let's switch over to Demo 2. So the first thing I want to show you-- so at Google-- so first, if you look at the numbers about devices that access corporate data that are under management, depending on what research study you look at, it's pretty abysmal, like something like 10% or 15% of devices that access corporate data are actually under management. At Google we don't believe in the unmanaged device, and so what we've done is we've turned on default on device protections for both mobile and desktop, and I'm going to show you a demo of both of those today. So the first one I'm going to show you is for mobile. This is something that we've been rolling out over the last 18 months, which is basic mobile management by default. It's been rolled out to 100% of our G Suite customers, and what this does is it enables us to inventory all devices that access G Suite, it allows us to wipe an account off those devices should they become lost or stolen, and it allows us to enforce a passcode on those devices if they don't have a passcode on them. So what I'm going to do is I'm going to search for user "easy." because we like easy, so give me a second here. So you can see I've got some Pixel devices here, but I don't have an iOS device. So I have an iOS device here on the right-hand side that's tied to this. So what I'm going to do is I have a passcode already on this device, and I'm going to log into Gmail for the first time. So we're going to log in with my account, easy, so hopefully I will remember my password. Let's see. Oops. And if that works we should be in. Now, the act of logging in to a G Suite property has registered this device with device management. So if I go over here and refresh, now we can see there's an iOS device listed in my device listing page. If I open that device, we can see that we have some basic information about the device. There's an identifier, we know what platform it's on, we know the management level, we know that it's a user owned device. Now, should this device become lost or stolen, then user calls up the admin and says, hey, my device is gone. The admin can say, OK, no problem, let's wipe the account off that device. So we hit wipe account. Now, we're going to give you a warning because wipe is a somewhat destructive action. You clear the warning, and then when Gmail will sync automatically in the background and it will automatically wipe, but sometimes on a demo you have to force it. And if I force it, if this goes right, Gmail is automatically logged out. So that's on by default for 100% of our G Suite customers. So you say great, what about desktop? So in October we announced a similar function for our desktop users. Let me go to Device Management here, and the function is called fundamental desktop security. And the act of logging in to any browser on any desktop machine logs a device in on our device listing page. It falls under endpoints here. So we're going to do this again. We're going to search for "easy." And in this case, I think this is going to pull up the device I'm on because we're logged into Chrome, right, so I'm in a Chrome browser here. But what I wanted to show you, I'm going to delete these two because I want to show you that of course it works on Chrome because we're Google and we own Chrome. So I want to show you that it also works on other browsers. So delete that. I'm going to flip over to Safari. So I'm going to log into Gmail on Safari, same user. Let's see where to log in. This is going to let me into Gmail. So now that I'm into Gmail, I can flip back over. Now, in the real world when we've launched this, it takes-- it can take up to 24 hours for the device to show up on the device listing page. In my demo environment it can take up to two minutes. So let's see if it's shown up yet. It has not shown up yet, so let's give it a second but [? we'll ?] sit here and hit refresh, and you guys can stare at me uncomfortably. There it is. So the device is showing up here. And in the case where we find duplicates, so I think it picked up the Chrome machine as well. We also, every 24 hours, discover where there are duplicates, like someone's logged in on two browsers on the same machine, and we merge those machines. So I'm going to open this up. Here's some basic information we got just from the act of logging into a G Suite property on a desktop device. We know a little bit about the operating system, we know ownership of the device, we can see the user that's using it. And we also, much like on mobile, if this device has become lost or stolen and we want to provide greater protection on the device, we can go and we can sign out the user from the device. So I'm gonna hit sign out user. Again, we give a warning. I'm gonna hit sign out and then we flip over here and then, much like before, when Gmail tries to sync in the background, it'll sign out. But if I hit refresh, it should ultimately-- we're signed out. And so we've protected that device. And then the other nifty feature here is I'm going to show you in a little bit a demo of context-aware access, but context-aware access is predicated on the idea that you've got folks running Chrome with endpoint verification extension installed on their devices. So one barrier to launching context-aware access is you need to know how many people are not running Chrome with endpoint verification on it. So with this feature you've got a list of all of your desktop devices in your environment. And you can go and you can look on-- and you can see who's logging in on a browser without endpoint verification installed so that you can go and you can send them all an email that says, hey, we're about to turn on context-aware access and we would encourage you to install endpoint verification prior to us doing that so you don't lose access to your G Suite. More on that later when I get to the further demo. So one other thing I want to show you. So that was basic or fundamental management for mobile and desktop. We also provide more protection through advanced management, and it's fairly easy to turn on. So let's say for mobile, you want to make sure that before you allow access on that iOS device that it's not jailbroken or you want to make sure that the device is encrypted or you want to do application management on your devices. All of those things come with advanced management. For us you go to our mobile settings, you go to mobile management, and basic is on by default. You just flip to advanced, and then you can go explore our settings and figure out what you want to turn on to provide more advanced protection. The difference here is that in that case, the end user has to jump through a few more hoops where they have to install a device policy, an agent on the phone, to gain some of those greater protections. OK, let's flip to the slides. So let's talk about managing local files on the desktop. So we flip over here, we can go back to Demo 2. So on Demo 2, so we launched at Next in San Francisco in April connectivity for managing Drive File Stream. So if you're not familiar with Drive File Stream, it's the world's largest hard drive. So you connect up your Mac or Windows machine to your Drive cloud account. And it looks just like a mounted hard drive connected up to the cloud, and it syncs your cloud files locally to your drive-- to your local drive as you need them. This is great for, let's say you've got a mobile sales team that travels a lot and they need to have local files available to them. The C-suite loves it because they want to see those files when they're on a plane. But every admin worth their salt says, that's great, but what do I do when those sensitive files are on a desktop that's been left in a cab? I need to have control over those files. So what we do is we allow you to manage Drive files that are stored locally on a desktop. I'm going to show you how that works. So in this case I've got my user Brad on technizza.com and I'm going to install Drive FS on this machine. So we're going to run Drive FS-- let's see. Here we go. We're going to sign in with Brad from technizza.com. Let's see if I can remember my password. Oops, that's not it actually. OK, we're logged in. Now, in this case the admin wants to approve devices before he allows access on this. So the person has installed Drive File Stream, that device has gone into a queue in our device listing page. So this is the device listing page where we show our Drive File Stream devices. I've hit refresh. We've had a couple of devices show up. Here's the one that's pending approval, so I'm going to open that up. Here's the device, and I can go in and I can approve the device. Now that I've approved the device, this device is enabled for Drive File Stream. If I run Drive File Stream again, we can now see-- it's going to give us a nice little screen, shows us exactly what we can do with Drive File Stream. And if I open the Google Drive folder-- and I'm going to pull it over the right because I'm going to show you some magic in a second. You can see that-- this is my Google cloud Drive and you can see that I-- these are actually files that are in the cloud. But I can go in and so this one is named Important Docs, that's something I want for the plane later. So I can go in and say, let's make that available offline. This one's Important [? Mocs. ?] Let's make that one available offline as well. And then when I refresh this, I may be a little too quick on that one, but we can see some information about Drive File Stream, the application version, first sync, last sync. Eventually when it's refreshed, it'll actually show the cache size, how much cache is stored on this device. And so again, just like we showed on mobile and desktop management, if this device has become lost or stolen, you want to make sure that you can do something with the files that are stored locally. So if someone calls up and says, I need to-- I left that desktop-- that laptop in an Uber, you can go and you can wipe the account. It'll give you a warning, you hit wipe account, and if it all works like it's supposed to-- I don't know if you noticed because it was quick, but the files have disappeared from the machine and this machine has been protected. So that is how you protect local files on the desktop. Let's switch back to the slides. Can we switch back to the slides, please? Can we switch back to the slides, please? There we go, great. OK, the next one we want to talk about is, how can I control access to sensitive information based on the attributes of users or devices? So this is the one I was foreshadowing. Let's talk about context-aware access. So please switch back to Demo 2. So context-aware is something that we launched at GA, we announced it in October alongside a couple of these other things that I'm talking about. So let's move down here to context-aware access. So context-aware access allows you to set access rules that can change based on the context. So you might want to set up a rule that says, I only want to allow access on a machine that meets certain attributes that is geolocated in certain places. So for the purposes of this-- let me log in first and foremost. One second. So for the purposes of this, what I'm going to do is I'm going to create an access rule that says I'm only going to allow access to Drive in the US and it should restrict us here because we're not in the US. So first things first, I'm going to show you-- here's Drive, I've got access to Google Drive. It's working great. And here's Gmail, we'll see if it'll just come up without me logging in again. Yeah, here's mail, mail's working fine as well. So now let's go in and let me show you how this works. So I've created a rule here called drive restriction. Let's take a look at it and we can edit it. So what you do is you can create a rule that can either meet these conditions or you can do the negative, you can say it doesn't meet these conditions. So in this case I set up a rule that says, I want to grant access, I want this app to meet that geographic origins in the United States. You can also do things like set up-- you wanted to be on a specific network, you want it to meet a specific device policy, you want it to [INAUDIBLE] a specific access level. You can make multiple conditions, they can be ands or ors, so it's very complex. Let's cancel that. So in addition to access levels, then once you've created that, you can then go and assign those access levels to apps. You can going to assign it to all of your apps, so maybe you want to create these access levels for all of them, but maybe you want to create more granular control. So you want everyone to have access to Gmail on the go, but you want to restrict access to Drive files in certain scenarios because that information is more sensitive in your organization. So in this case, I've assigned this rule to Drive, but I haven't assigned it to anything else. So let's go back and let me show you one more configuration piece. So you want to make sure that when people get restricted that they know what to do. And so we have a generic message that pops up when you're blocked. We have the ability to configure this message as well. So here we say contact your administrator. You might want it to say, this is why you received this. You might want to say, contact your administrator at this email address or at this phone number, just give a little bit better remediation of the problem when it occurs. OK, so let's go turn this thing on and I'll show you how it works. So the key here is-- and I'm going to turn on this rule which restricts Drive, and I'm going to go to Drive, and it should work immediately. Boom, Drive's been restricted because we're not in the United States. If I go to Gmail, Gmail should still work just like it always has because it didn't have the restriction on it. What I love about this feature is that it's instantaneous, so if I turn it off and I go back over here and we go back to Drive, near instantaneous, I should say. That's what I get for trying to show off. There it is. So we're back into Drive. So that's context-aware access. Let's go back to the slides, please. All right, one last demo. How are we doing on time? We're doing great on time. So the last thing I want to show you is setting up rules for automating alerts and taking remediative action. So let's flip back over to Demo 2, and I'm back in the security section of the admin console. So one of the things we found, we built all of these great ways for you to go and investigate just like Sam was showing you earlier. We built great ways to alert your admins when you have a problem. What we found is in some cases that's not good enough because admins are getting too many alerts. There are too many vectors for attack, and they just don't have the time to take action on these alerts. And so we created a rules engine to automate tasks where they're sure that they can take-- they want to take action on security events. And so what I'm going to do is I'm going to walk you through going through a quick investigation and then automating an action via rules that I would like to take on that investigation. So using the investigation tool, what I've noticed is that there's a domain that is sending phishing emails to my organization. And I just want to put all of those emails into quarantine so that I can deal with them later but I want to make sure that none of my employees are getting them. So I'm going to go and I'm going to look Gmail log events, and I'm going to add a condition which is, if the domain contains-- and I'm sorry, Sam, but it's Inc42 is the perpetrator here. So if I'm getting emails from Inc42, I think that's a bad actor. And you can see I'm getting a bunch of emails asking to confirm login details. I don't want my employees to get those anymore. So what I'm going to do is I'm going to create a rule that automatically quarantines these emails. So I can go here and I can select create rule. So this automatically pops up a Modal. We enter rule details, you can type what you're working on here, quarantine Inc42, you can put a description if you need to. Currently it applies to the entire domain. And we are going to next move to the conditions. We automatically load conditions from that investigation that we just did. So you can see that it's looking at the header, contains Inc42. And then it asks, what event do you want to trigger this rule? So in this case the event that we want to trigger the rule is when we receive an email from Inc42. So we've done that and now we're going to add an action. So we flip over here, and what I like about the way that the team has implemented this is that we're going to give you some information about what is the impact of this rule when you turn it on? So we're going to show you, here's a preview of had this rule been on over the last week or so, how many times would it have been triggered? So you can set a threshold. So maybe you don't want to quarantine these messages if they're just coming in once every 24 hours. But if you see a spike in these messages, say, more-- 10 or more in a 24-hour period, you want to start quarantining them. So in this case I've got it when the count is above zero, so we want to quarantine all of them. Then what is the action we want? The action is we're going to send to quarantine. And then you can also create alerts for this. So I'm going to create an alert. You can select a severity for the alert, let's call it medium, and you can select who to send the email notifications to. In this case I'm going to send it to all super admins, and you can also add individual recipients if you want. And then prior to committing to the rule, you go to a review. And here again we can see everything that we've built and you can also see-- you can put the rule in an inactive state, which means I've crafted the rule but I'm not ready to do anything with it. You can put the rule in a monitor state, which means, let's turn this thing on and see what impact it would have if I had enabled it. Or you can just put it straight into an active state and it will immediately start quarantining based on the parameters of the rule. And that is how you create as a rule from an investigation. That's everything I wanted to show you. So if we can go back to the slides I've got one last thing to talk about. As Sam said at the beginning of the session, we love your feedback. This is a little bit different session than what you've seen elsewhere, it's been very heavy on use cases. If you loved it, come tell us you loved it. If you hated it, come tell us you hated it because this is the way we make decisions on what we do in future presentations, so we would love to get your feedback. I know that I'll be around for a few more minutes after this. So if you have any questions, please feel free to come and grab me. Thank you so much for your time. [APPLAUSE] [UPBEAT MUSIC PLAYING]
Show moreFrequently asked questions
How do I eSign a document before sending it?
What do I need to sign a PDF electronically?
How can I sign a PDF file and send it back?
Get more for CloudTrust esigning made easy
- Signature face-to-face
- Prove email signature Performance Review Self-Assessment Template
- Endorse eSign Graphic Design Quote
- Authorize digital sign Late Rent Notice
- Anneal signatory Accounts Receivable Purchase Agreement
- Empower electronically signed Sales Receipt
- Try digisign Doctors Excuse for Work
- Add Assurance Agreement sign
- Send Mobile app Development Proposal Template electronically signing
- Fax Free Graduation Certificate mark
- Seal Training Acknowledgement Form eSignature
- Password Indemnification Agreement autograph
- Pass Outsourcing Services Contract Template digital sign
- Renew Pet Custody Agreement signed electronically
- Test School Counseling Progress Report electronically sign
- Require W-9 Tax Form countersignature
- Send corroborator esign
- Accredit spectator digi-sign
- Compel recipient signed
- Void Freelance Quote Template template initials
- Adopt certificate template eSign
- Vouch Notice To Vacate Form template eSignature
- Establish Proposal Letter template digisign
- Clear Founders’ Agreement Template template electronic signature
- Complete Child Medical History template signed electronically
- Force Sales Agency Agreement Template template countersign
- Permit Professional Model Release Contract template sign
- Customize Entertainment Contract Template template electronically signing