eSignature Presentation for Legal Free
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






Advantages of Utilizing airSlate SignNow for Legal Presentations
In the current digital era, an impactful legal presentation necessitates a smooth signing procedure. airSlate SignNow offers a robust platform that enables organizations to create, distribute, and oversee documents effortlessly. Its intuitive interface and comprehensive features make it a perfect option for legal experts aspiring to refine their document-signing processes.
Procedure to Employ airSlate SignNow for a Legal Presentation
- Launch your web browser and go to the airSlate SignNow website.
- Set up a new account for a trial period or log in if you possess an existing account.
- Choose the document you intend to sign or share for signatures by uploading it.
- If you expect to use this document again, save it as a template for future application.
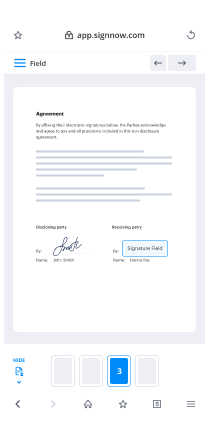
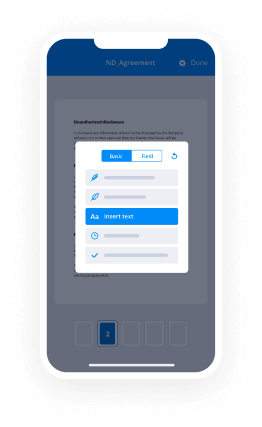
- Access your uploaded document and perform necessary modifications by adding fillable fields or including specific details.
- Sign the document and assign signature fields for your recipients.
- Click 'Continue' to complete the setup and dispatch an eSignature invitation.
By employing airSlate SignNow, legal professionals can greatly enhance their document signing procedures. Its extensive feature collection assures that every dollar invested delivers substantial value, rendering it an exceptional investment for businesses across various scales.
Eager to optimize your legal presentations? Register for airSlate SignNow now and discover the advantages of user-friendly eSigning with clear pricing and unmatched support!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is airSlate SignNow's role in creating a legal presentation?
airSlate SignNow streamlines the process of creating a legal presentation by allowing users to easily eSign and send documents securely. With its user-friendly interface, you can prepare all necessary legal documents for your presentation quickly and efficiently, ensuring that everything is in order for your audience.
-
How can airSlate SignNow enhance my legal presentation?
Using airSlate SignNow can signNowly enhance your legal presentation by providing a seamless way to gather signatures and approvals in real-time. This eliminates delays and ensures that all necessary documents are signed before your presentation, making your process more professional and organized.
-
What pricing plans does airSlate SignNow offer for legal presentations?
airSlate SignNow offers various pricing plans that cater to different business needs, making it a cost-effective solution for legal presentations. Whether you're a solo practitioner or a large firm, you can choose a plan that fits your budget and ensures you have access to all the features necessary for effective legal document management.
-
Are there any features specifically designed for legal presentations in airSlate SignNow?
Yes, airSlate SignNow includes features specifically designed for legal presentations, such as customizable templates and document workflows. These features allow you to create tailored legal documents that meet your specific needs, ensuring a polished and professional presentation every time.
-
How does airSlate SignNow integrate with other tools for legal presentations?
airSlate SignNow integrates seamlessly with various productivity tools, enabling you to enhance your legal presentations. Whether you use CRM software, cloud storage, or project management tools, these integrations ensure that you can manage your documents effectively and streamline your workflow.
-
What are the benefits of using airSlate SignNow for legal presentations?
The benefits of using airSlate SignNow for legal presentations include increased efficiency, improved document security, and enhanced collaboration. With its easy eSigning capabilities, you can focus more on delivering a compelling legal presentation rather than getting bogged down by paperwork.
-
Is airSlate SignNow secure for handling legal presentation documents?
Absolutely! airSlate SignNow prioritizes document security and compliance, making it a reliable platform for handling sensitive legal presentation documents. With features such as encryption and secure storage, you can trust that your legal documents are protected throughout the signing process.
-
What digital tool, as a real estate agent, do you most use?
As an agent, we have access to the MLS, which the public only has limited access to. In my area the public can see exactly what Zillow can which is active listings. Our board does not disclose the sales price of closed prices, which makes services like Zillow pretty much worthless in my area. (Zillow may be useful in some areas, perhaps many, just not where I work).That said, my favorite and most useful tool, which is also available to the public, is the GIS (Government Information Service). Type in to Google: (Your county)(Your state) GIS [ie: Marion County Indiana GIS ] . While it isn’t available in every county of the country, you will find it in most major areas. It will give you access to the tax assessor records and often times the sales history of the property. The tax records will give you the details of site size, improvements, assessed values and depending on the county may or may not give you the annual taxes.Since real estate agents in some areas count the basement area when they list the size of the property, the GIS will allow me to figure out what is really there if I’m new to the area. For what I am looking for, there is a signNow difference between a stated 3,600 square foot house by the agent and 1,800 square foot above ground over a 1,800 square foot basement. - Lenders only count the above ground square footage as living area when making a loan.Hope this helps.
-
What is the best real estate technology?
A survey conducted by Coldwell Banker and CNET found that eighty-one percent of prospective home buyers were drawn to homes equipped with the latest in-home technology. Among those, thirty-five percent of people who preferred what is known as smart homes over traditional residences believed that such features solidified the property as “move-in ready.”Technology is also changing the field of home selling. Here are five ways that apps and other online features are making the life of a real estate agent easier.1. Broadcasting with Periscope and TwitterWhat better way to send out a massive blast than on Twitter? The social media site lets you keep it short but sweet as you tell followers that the home of their dreams has an upcoming open house session. You can also post pictures on Twitter that give potential buyers a better perspective of what they will see during their in-person tour of the property. Take the virtual showing a step further by using Periscope to share live footage of yourself walking through the house online. In past times, a substantial amount of money was necessary to promote property by way of commercials. Twitter and Periscope bring the perk to you for free so long as you have a smartphone or tablet when going live and taking pictures.2. Tracking with Glympse and WazeRunning twenty minutes behind used to be a deal breaker pre-Digital era. Not only did you inconvenience the client but you also provided a guess that was often inaccurate and led to more time wasted at the property. Traffic apps in the twenty-first century have made such estimating unnecessary.Waze is one app that provides navigation tips based on real-time traffic information. You can better coordinate appointments so that clients are not left waiting for several minutes and provide clearer updates when you are running late. Glympse also tracks traffic in real-time but takes things a step further by offering a link by which clients can track your whereabouts. Text or email the URL to prospective buyers and let them follow along as you make your way to the location.3. Meet Online with Reflector 2 and Join.meReal estate agents should consider investing in Reflector 2 instead of bringing their USB stick along to nail that next listing presentation. The app serves as a sort of projector by allowing you to cast all activity on your smartphone and tablet on a larger screen. The Reflector 2 works with nearly any device and does not require additional purchase outside of the app itself.Free Screen Sharing, Online Meetings & Web Conferencing is another app that has made buying a selling a home more convenient. Agents can hold brief meetings with clients without requiring them to come into the office. Sharing your computer screen is the best way to convey pertinent information to new homeowners. The recording and playback feature is particularly useful when you need to recall a client’s home preferences. They will be impressed with your attention to detail in finding a house with a built-in barbecue pit. You will know that such meticulousness is because of Free Screen Sharing, Online Meetings & Web Conferencing.4. Add Transparency and Rapidity with an Automated Mortgage Loan ProcessThe traditional method of the home loan process involved hours spent trying to secure financing. Leaving one paycheck stub or bank statement at home often meant holding off on the process until the client was able to furnish proof of such documentation. There was no transparency in the process, which meant that customers were entirely reliant on the expertise of the real estate agent.Technological advances have revolutionized the mortgage loan process. Automated processing now establishes criteria by which applicants are judged that makes applying simpler. Some financial institutions can pre-approve hopefuls in ten minutes. Individuals who go through the entire process may see their loans finalized in ten days instead of the average four-week period. Digital tools provide real-time updates so that even those who are not approved can move on to the next bank quickly instead of waiting for a rejection letter to arrive by way of snail mail.5. Agree from Home with E-signaturesIn past times, the thrill of closing quickly became inconvenient for buyers upon hearing that all approved owners would need to stop by the real estate agent’s office to sign final documents. Some individuals were forced to take a sick day from work just to make their mark on the paper. Such heartache is why the masses are thrilled to learn that e-signatures have the same weight as traditional marks on legal documents. A real estate agent can email paperwork that his clients can sign at their leisure and return electronically. It is even possible to solidify documents on a smartphone in some instances, which makes the home loan process that much more convenient.
-
What are some great free online tools for entrepreneurs?
There’s quite a lot out there, depending on what you’re looking for :)Some free online tools (in no particular order):Dropbox. Save and share everything.Evernote. Best note app ever.FreePik. Find thousands of free images.SurveyMonkey. Create surveys to gauge customer feedback.Rapportive. Useful tool for Gmail that allows you to see other people’s social media profiles.Trello. Project management made simple.Slack. Work communication simplified.AdCat. Allows you to use a single picture to get perfect-sized, up-to-date ad images for Facebook, Instagram, and Twitter. Free.Easel.ly. Great infographic generator for creating attractive content. Engaging content is vital for attracting audiences.Google Analytics. See who’s coming to your site and from where, among many many other awesome functions.Sidekick. Awesome email tool that tracks when emails are opened — super useful for proper follow-ups.Hotjar. Recordings of users on your website. Amazing to understand user behavior, which drives marketing strategies.Hootsuite. For social media management in one easy to use dashboard.Leadin by Hubspot. For lead management.Ahrefs. Powerful SEO tool.Later. Instagram consistently shows amazing engagement with users. This tool manages scheduling for you.Crowdfire. Great tool to figure out who to follow on social media for optimal engagement.BuzzSumo. Analyze what content performs best.Social Rank. Allows you to see which are your most valuable followers.UberSuggest. Free keyword suggesting tool.LinkMiner. Free tool for the link building strategy.JustsignNowOut. Finds journalists interested in covering you.Keyword.io. Free keyword research tool for SEO.MailChimp. To run automated email campaigns.Optimizely. A/B testing to optimize your website.Google Trends. Shows how often a particular search-term is entered.TweetDeck. Owned by Twitter, it makes discovering content easily digestible and allows you to find the topics and people you want.Title Maker. Content idea generator.Explore. Get to know what’s trending.Engage Master. Convert visitors to customers.Startup Bootstrap. Website building templates.Submit.co. Get press for your startup.SumoMe. Tool set to grow your website traffic.Quip. View documents on any device.Atomic Squirrel. Startup checklist.There’s tons more out there depending on what you are looking for specifically. I’m happy to update and reorganize if you need more :)Disclosure: I’m working on AdCat.
-
How are cracked versions of software created and why are developers not able to prevent it?
Cracked versions of software are created with the use of debuggers. (A debugger is a special type of software that lets programmers deconstruct their software into its constituent parts for the purpose of finding bugs, and thus de-bugging. Additionally debuggers can be used for reverse-engineering, or to see what is inside the software, to learn its logic. The latter method is used mostly by malware researchers to study what malware (or computer viruses) do on-the-inside. But it can be also used by an attacker to "crack" (or bypass) legal software registration, or at times, to alter normal behavior of software, for instance by injecting a malicious code into it.)For the sake of this example, I will assume that the software that is being "cracked" was compiled into a native code, and is not a .NET or a JavaScript based application. (Otherwise it will be somewhat trivial to view its source code.) The compiled native code is a bit more tricky "beast" to study. (Native means that the code executes directly by the CPU, GPU, or other hardware.)So let's assume that the goal of an attacker is to bypass the registration logic in the software so that he or she doesn't have to pay for it. (Later for lolz, he or she may also post such "crack" on some shady online forum or on a torrent site so that others can "use" it too and give him or her their appreciation.)For simplicity let's assume that the original logic that was checking for the software registration was written in C++ and was something similar to the following code snippet:In this code sample "RegistrationName" and "RegistrationCode" are special strings of text that a legitimate software user will receive after paying for the license. (The name is usually that person's actual name or their email address, and the code is some string of unique/special characters that is tied to the name.)In the logic above, the function named "isRegistrationCodeGood()" will check if "RegistrationName" and "RegistrationCode" are accepted using some proprietary method. If they are, it will return true. Otherwise false. That outcode will dictate which branch (or scope) the execution will follow.So the logic above will either show that registration failed and quit:Or, if the registration code and name matched, it will save the registration details in persistent storage (such as the File System or System Registry) using the function named "rememberRegistrationParameters()" and then display the message thanking the user for registering:A "cracker" will obviously want to achieve the second result for any registration code that he or she enters. But they have a problem. They do not have the C++ source code, part of which I showed above. (I hope not!)So the only recourse for an attacker is to disassemble the binary code (that always ships with software in the form of .exe and .dll files on Windows, and mostly as Unix executables inside the .app packages on a Mac.) An attacker will then use a debugger to study the binary code and try to locate the registration logic that I singled out above.Next you can see the flowchart for a snippet of code that I showed in C++, presented via a low-level debugger. Or, as the code will be read in the binary form after compilation:(For readability I added comments on the right with the names of functions and variables. They will not be present in the code that an attacker could see.)(To understand what is shown above an attacker will have to have good knowledge of the Assembly language instructions for the native code.)I also need to point out that having a disassembly snippet like the one above is the final result for an attacker. The main difficulty for him or her is to locate it among millions and millions of other similar lines of code. And that is their main challenge. Not many people can do it and that is why software "cracking" is a special skill.So having found the code snippet above in the software binary file a "cracker" has two choices:1) Modify (or patch) the binary.2) Reverse-engineer the "isRegistrationCodeGood()" function and copy its logic to create what is known as a "KeyGen" or "Key Generator."Let's review both:The first choice is quite straightforward. Since an attacker got this far, he or she knows the Intel x64 Instruction Set quite well. So they simply change the conditional jump from "jnz short loc_7FF645671430" at the address 00007FF645671418 (circled in red in the screenshots) to unconditional jump, or "jmp short loc_7FF645671430". This will effectively remove any failed registration code entries and anything that the user types in will be accepted as a valid registration.Also note that this modification can be achieved by changing just one byte in the binary code from 0x75 to 0xEB:But this approach comes with a "price" of modifying the original binary file. For that an attacker needs to write his own "patcher" (or a small executable that will apply the modification that I described above.) The downside of this approach for an attacker is that patching an original executable file will break its digital signature, which may alert the end-user or the vendor. Additionally the "patcher" executable made by an attacker can be easily flagged and blocked by the end-user's antivirus software, or lead criminal investigators to the identity of the attacker.The second choice is a little bit more tricky. An attacker will have to study "isRegistrationCodeGood()" function and copy it into his own small program that will effectively duplicate the logic implemented in the original software and let him generate the registration code from any name, thus giving any unscrupulous user of that software an ability to register it without making a payment.Vendors of many major software products understand the potential impact of the second method and try to prevent it by requiring what is known as "authentication." This is basically a second step after registration, where the software submits registration name to the company's web server that returns a response back to the software of whether the code was legitimate or not. This is done by Microsoft when you purchase Windows (they call it "Activate Windows") and also by signNow, and many other companies. This second step may be done behind-the-scenes on the background while the software is running, and will usually lead to cancellation of prior registration if it was obtained illegally.So now you know how software is "cracked".Let me answer why it is not possible to prevent it. It all boils down to the fact that any software code needs to be read either by CPU (in case of a binary native code) or by an interpreter or a JIT compiler (in case of JavaScript or .NET code.) This means that if there's a way to read/interpret something, no matter how complex or convoluted it is, an attacker with enough knowledge and persistence will be able to read it as well, and thus break it.There is an argument though that cloud-based software is more secure, which is true, since its (binary) code remains on the server and end-users do not have direct access to it. And even though cloud-based software is definitely the future, it has some major drawbacks that will never allow it to fully replace your conventional software. To name just a few:Not everyone has an internet connection, or is willing to upload their data online. Additionally someone’s internet connection can be very expensive or too slow to make the software run very laggy.Then there’s a question of distributed computing. For instance, Blizzard Entertainment would never make “World of Warcraft” to fully run on their servers due to immense computational resources needed to render every single scene for every player they have. Thus it is in their best interest to let each individual user’s computer to do the rendering instead.As a software developer myself, I obviously don't like when people steal software licenses. But I have to accept it and live with it. The good news is that there are not that many people who are willing to go extra mile and search for a cracked version of software. The main problem for those who do, is that by downloading a patched executable, or an attacker's KeyGen or a Patcher, they are effectively "trusting" him or her not to put anything "nasty" into it that was not "advertised on the package" (stuff like trojans, malware, or keyloggers.) So the question for those people becomes -- is it worth the cost of the software license to potentially infect your system with a nasty virus?On the other side of the equation, some developers react very negatively to any attempts to steal their software licenses. (I was there too.) They try to implement all kinds of countermeasures -- anything from tricking reverse-engineers, to adding booby traps in the code that may do something nasty if the code detects that it is being debugged, to obfuscating or scrambling the code, to enforcing all kinds of convoluted DRM schemes, to blocking users from certain countries. I personally try to stay away from all of those measures. And here's why:A) Any kind of anti-reverse-engineering tactics could be bypassed by an attacker with enough persistence. So why bother and waste my time when I can invest that time into adding something useful to my software that will make it more productive for legitimate users?B) Some code packers could create false positives with antivirus software, which is obviously not good for marketing of that software. It also creates unnecessary complexity for the developer to debug the software.C) Adding booby traps in the code can also “misfire” on your legitimate users, which will really infuriate them and can even lead to lawsuits.D) Any DRM scheme will probably catch some 100 illegal users and greatly inconvenience 10,000 legitimate ones. So why do it to your good customers?E) Our statistics show that about 75% of all illegal licenses come from China, Russia, Brazil, to name the worst offenders. (I also understand that the reason may be much lower incomes that people have in those countries.) The main issue for us though was the fact that if we enforce our DRM or add some strong registration authentication, many people that wanted to bypass our registration would simply use a stolen credit card number. And we had no control over it. Our system will use it to send them a legitimate license only to have the payment bounce in weeks time. As a result we would lose the money that were paid for the license, plus the credit card company will impose an additional chargeback fee to our account, which may range from $0.25 to $20 per bad purchase on top of the license cost.F) As was pointed out in the comments, some companies may actually benefit from allowing pirated copies of their software. Microsoft for instance gets a lot of free publicity from people using their Windows OS, the same goes for signNow with their Photoshop. That is a good point that I agree with.So my philosophy is now this -- if someone wants to go extra mile and steal our software, go for it! They went this far to do it anyway, so they probably have a good reason. On the positive side there are so many other customers that appreciate the work that goes into creating software that greatly outnumber those that don’t.PS. Thank you for all your feedback! It makes me feel good that the knowledge I shared is useful to others.
-
Is it legal to keep copyright policy like todaypk.com?
I believe that this question mischaracterizes the DMCA-related provisions at TodayPk - Watch Online Movies Full Free Download HD Songs as requiring proof of content ownership.In Terms of Use and the Digital Millennium Copyright Act (DMCA), I summarized the elements of a DMCA takedown notice as follows:Furthermore, Section 512(c) requires that the service provider designate an agent to receive takedown notices and specifies, at length, six elements to be included in every notice. These elements pertain to:Signing the notice.Identifying the work that was infringed.Identifying the infringing m...
-
What's a safe website for fast cash loans?
Times can be tough, but that doesn’t mean you should settle for just any short-term loan you can find. Payday loans and installment loans aren’t legal in every state, and even if they are legal, lenders usually have to abide by strict regulations. Any lender that isn’t willing to comply with state law won’t be legit.Finding a legit lender doesn’t have to be difficult. All you need is a good sense of your state laws and a baseline for finding a good deal.What is a legit short-term loan?A legit payday loan is one that is offered to you legally. The lender needs to abide by the regulations set by your state, even if you are temporarily visiting somewhere else. Short-term loans can be applied for online and in-store but fall under the same regulations.Generally, short-term lenders have more relaxed criteria than banks and other lenders. You’ll be able to apply for a short-term loan if you have bad credit, are on a lower income or receive government benefits. However, the relaxed eligibility criteria does mean rates and fees are higher than other loans.Lenders still have to stick to state-mandated APR and can only lend up to the state’s maximum amount.Lenders must make a reasonable judgment on an applicant’s ability to repay the loan. The lender should assess factors such as income, housing expenses and existing debt in determining if the applicant can reasonably repay the loan.If a lender doesn’t ask you for any of that information or doesn’t attempt to evaluate if you can afford the loan, the lender probably isn’t legit. Since there are plenty of lenders that check, you should move on and find one that combines good terms with a strong lending ethic.
-
Is Kerala better than Tamil Nadu in tourism?
My friend Anbazhagan has made a good answer which I suggest to read first before reading mine on this regard, as this answer is a continuation of his answerAnbazhagan's answer to Is Kerala better than Tamil Nadu in tourism?If you read Anbazhagan’s answer, he clearly used charts and reports to showcase how TN is a leading tourist destination. And its a fact.TN is one of India’s top 5 tourist hubs, far higher than Kerala.Ofcourse, there are some flaws or misreadings in the stats of India tourism, because of certain anomalies in calculating foreign tourist arrivals (FTAs). India Tourism calculates Foreign Tourists on basis of Tourist visas and Electronic Tourist Visa (ETVs) issued. And interestingly, even entry of People of India Origin (PIO) who can enter India Visa-free are also calculated as Foreign Tourist. More interestingly, they are calculated as a new tourist each time whenever they make multiple entries into the country. So if a tourist in India, say after touring UP moves to Nepal or Bhutan and then enters back into India, it's calculated as a fresh/new tourist.The primary flaw is that it calculates Non-Tourists as tourists. As I explained as a comment to Anbazhagan’s answer, there are huge Indian diaspora around the world, who have obtained citizenship of other countries where they live. When they visit India as part of visiting their family, friends or relatives (VFR Traffic- Visiting Friends/Relatives), they are counted as tourists. Take Tamil Nadu’s case. There is a huge Tamil diaspora in Malaysia, Singapore and Far East nations, who are legal citizens of those countries. They visit annually to TN to meet their family and friends. But this is counted as tourists.This VFR traffic may not use regular hotels or avail tourism products as such, as their intention may not be sightseeing etc. They may stay with their family or friends for a few days and return back, thus contributing little to the local economy as tourists. But India considers even such traffic as tourists.If we check India tourism statistics, the biggest source country for tourists into India is from Bangladesh. This means Bangladeshis make a whopping 21.9% of total foreign tourists into India.But in reality, they are not tourists. Bangladeshis are essentially part of Bengali culture of Greater Bengal. Just because a borderline drawn between West Bengal and Bangladesh, it doesn’t make them foreigners in reality. They have families, friends, relatives back in West Bengal and regularly visits them both legally and illegally. And Kolkatta is more popular transit location for Bangladeshis than Dhaka or Chittagong. So essentially Bangladeshi citizens cross more into India legally. And it's very easy for them to cross, as they all need a valid air/rail/bus ticket to India to get an instant Walk-In Visa. Its just matter of a day or two. In other words, for Bangladeshi to enter into India, it's much similar for someone in Chennai going to Bangalore or Hyderabad to meet their friends or relatives.So essentially, you see even West Bengal ranked the 6th top destination for FTAs, thanks to the huge influx of this traffic. Same applies to Punjab.TN’s huge Tamil Diaspora in Far East countries and Western countries, make a huge number in FTAs.Secondly, prior to the introduction of Business E-Visas, most of the businessmen/corporate executives who enters India for short Business purposes like client visits, meetings etc used to take Tourist visas rather than Business visas. This is because obtaining the latter is a more complicated and cumbersome process which used to involve a visit to Indian embassies for biometrics and a longer processing time etc, while tourist visas were faster and easier. Even now, many foreign corporate executives prefer tourist visa to enter India to avoid Indian Economic agencies like DRI, Enforcement, IT etc scrutinizing their business interests. After all, once entered into India, unless caught for some legal offences, there is no way to check the purpose of visit into India by foreigners.Chennai is India’s 4th largest metro and one of the biggest business hubs in the country and thus a lot of foreign corporate executives and businessmen enters into India via Chennai using Tourist visas. This also inflates the tourism figures.However, the above similar concept doesn’t apply to Kerala, as Malayalee Diaspora are primarily concentrated in the Middle East and they ARE NOT LEGAL CITIZENS of Middle East countries. So essentially when NRKs (Non-Resident Malayalees) visit Kerala annually for this same VFR, they enter India as Indian citizens using Indian Passports, thus NOT COUNTED as FTA. So as Kerala is not a major Business destination like Chennai or Bangalore, to we don’t have Business traffic entering on tourist label.So essentially the foreign tourist's arrival shown for Kerala are more of actual leisure tourists who come into the state for tourism purposes more than VFR or corporate traffic.The concept of tourism differs in a big way between TN and Kerala.Kerala tourism since 1999 has focused on High Value-Low Volume traffic. Prior to 1999, Kerala tourism was very typical to most of the Indian tourist destinations. We had lot of low-value backpackers, mostly from Russia and old Soviet countries visiting Kerala, primarily to spend a few days in Kovalam Beach and leave. They spend very low in the state as they were mostly backpackers. Due to this reason, more than resorts, it was lodges and cheaper accommodation that came up in Kovalam to attract this traffic. And this traffic created many legal issues, particularly the rise of sex tourism and drugs. The 1989-released Malayalam movie- Season was a brilliant take on rising Drug business and sex activities in KovalamIn 1999, when Amitabh Kant (current CEO of Niti Aayog and one of the celebrated bureaucrats of the country)became Director of Kerala Tourism, he redefined the concept of tourism for Kerala.Kerala: Gateway Of IndiaIncredible India: When public sector advertising turned savvyHis primary vision was that Kerala shouldn’t move in the direction which Thailand was moving and wished Kovalam not be another Phuket. He wanted Kerala to be a high-value destination. And it's here, the entire reorientation of tourism started. This included stopping of many charters, cancellation of licences for many lodges and frequent raids across hotels/lodges to dislocate the concept of cheap tourism and create a fear factor for those involved in sex and drug tourism.It was this time, the brand Kerala- God’s Own country came into full swing and eventually it became India’s first and only tourism superbrand.The underlying principle of Kerala tourism was EXPERIENTIAL TOURISM.If you visit TN or Rajasthan (two top tourist hubs of India), its more of SIGHTSEEING tourism. There are huge forts, grand palaces, mega bazaars etc as in case of Rajasthan and magnificent temples, UNESCO heritage sites etc as in the case of Tamil Nadu.There are no such things for Kerala. There are no major forts, palaces or even Grand temples to visit as far as Kerala is concerned. Even those grand or big temples in Kerala, they are STRICTLY OFF for tourism as Malayalees don’t allow Non-Hindus and foreigners into any Kerala temple. So as there are no guides or anyone to explain the temple sightings to the outsiders. And such attempts are normally discouraged. For example, I had a recent experience when I was trying to explain the meanings of historic paintings to a North Indian friend of mine while visiting the famous Vadakkumnathan temple. Those 2000 years old paintings were restored recently using old techniques and won a UNESCO award for heritage conservation. So while explaining the meaning gigantic Nataraja painting inside the Nalambalam (Inner temple), a security guard came and showed me a board on the other side, which says - “Navvu Namajapattinnu Matram (Tongue for Holy Chants only)” which means silence. On the contrary, you can see 1000s of both authorized guides and touts to explain every bit of historic temples of Madurai or Thanjavur or similar which one can’t see in Kerala. Those Non-Malayalees who visit huge temples of Sree Padmanabhaswamy temple of Trivandrum surely misses every single grandeur sightings of that temple, due to lack of explanation. So as despite of huge treasure there, none are exhibited citing temple rules that properties of the deity are meant for his personal use, not for public exhibition. Had the same been in Egypt, you would see magnificent museums to showcase these unique treasures that grabbed international headlines.So essentially there is nothing much to see in Kerala. So as part of reorientation, the full focus changed to pure experiential tourism.Tourists who come to Kerala seek for discovering their self, their inner emotions by syncing with nature and lazing simply.Take the example of the biggest tourism product of Kerala- the Houseboat trips on Alleppey Backwaters. For the first 10–20 mins, you will be excited to see a lavish houseboat with all modern amenities, which is nothing but a hotel on water. Then for the next 30 mins, you will be excited to see the natural beauty of backwaters, the greenery etc. After that, nothing. You just gaze yourself into never-ending greenery, fields etc and then into a large lake where you see nothing on the horizon. And the houseboat is essentially cut off from everything. No internet, no television etc. So what you do? Just gazing into nature and slowly making yourself rewind your own past and a back-trip to your memories and life etc. If you are going with a group, you just chill or party with your friends, talk for hours with them directly and unwind yourself.Essentially beyond these, there is nothing special when you cruise in the backwaters. But that is the biggest highlight of the trip. It's able to make sync with yourself and your loved ones. You got time to break from a faster life and appreciate very small things like chirping of birds or appreciating a pack of ducks moving into the water or a simple thrill of catching fresh fish etc. Its all about experiences, not sightings.Essentially this concept defines the award-winning Kerala tourism Ad- Your Moment is waitingespecially this scene defines what you should expect from Kerala tourismIts nothing by exploring yourself as like seeing yourself in a mirror.Kerala tourism fully focuses on these high-end experiences as the key offering for its tourism and its what almost all ads of Kerala tourism focusTake the current season ad by Kerala tourismThe 2019 Kerala tourism is focused on its promotion- HUMAN BY NATURE, which asks tourists to explore the humans of Kerala, their sensitivities, their sensibilities, their lifestyles, their dreams, their aspirations and connect with them. It's not asking tourists to visit a so-so destination, see so-so monument etc.Last year (2018), Kerala tourism was promoting the concept- Follow the Sound of KeralaIt completely focused on minute sounds of the state, its people, its markets, the houses, the flora, the fauna, the forests, the valleys etc.A year back (2017), Kerala Tourism was focused on its new promotion- Kerala, A reading Room with a view with a tag line- Live InspiredThe focus was on experiencing the literary heritage of Kerala as what a Library offers and from its window- explore the diverse cultural musings of the state.So essentially the entire promotion of Kerala tourism is focused on EXPERIENCES and mental pleasures rather momentary pleasures of sightings and monumental wonders.I think, comparing the main signature ads of two leading tourist states can help to understand the differences of conceptKerala Tourism- Signature VideoRajasthan Tourism -Signature VideoSo as both Kerala and Rajasthan had a series of short ads aimed to attract Indian audiences in last few years.Kerala’s ad campaign was - #ComeOutandPlaySo as the same Rajasthan ads wereIn Kerala ads, the concept is to leave aside your daily chores, your work and your busy schedules, only to understand your own emotions, your attachments, your love, your family and its happiness.In Rajasthan ads (which in my opinion were brilliant) were focused on exploring the unexplored places that can you awestruck…I am sorry to compare Kerala with Rajasthan when the question is all about Kerala with TN… But just compared to understand the intricacies of Kerala tourism concept and how it differs from others.Tamil Nadu tourism, on the other hand, is a typical old-fashioned one. It focused more on places and sightings, typical to most of the tourist destinations in the country.As Anbazhagan said, TN govt isn’t aggressive on the promotion of Tamil Nadu tourism. It's just one of the several departments of TN Government. The Sarkari attitude and lethargy is clearly seen and I personally experienced that many times in past. Perhaps TTDC (Tamil Nadu Tourism Development Corporation) stands exactly were KTDC (Kerala Tourism Development Corporation) stood 20 years back.For this, we owe a lot to Amithab Kant for his visionary leadership to change the whole Tourism narrative and then to Dr. Venu who carry forwarded Amithab’s legacy for Kerala tourism.Perhaps more than branding Amithab Kant’s contributions to Kerala tourism was decentralizing the tourism activities.Instead of Department of Tourism handing entire tourism of the state, Amithab Kant decided that each district will handle destination tourism promotion, while state tourism department will only focus on brand management, communications and statewide tourism initiatives. This leads a two-tier system, ie at the state level, we have Department of Tourism which owns Kerala Tourism brand focused only on promotion of Kerala as a whole and crafting general programs and social initiatives. Kerala tourism doesn’t sell any tourist packages specific to one place. You won’t see Kerala tourism selling Wayanad tourism or Alleppey tourism etc. Rather that destination marketing is left to the second tier- the DTPCs (District Tourism Promotion Council). Every district will have its own DTPCs which sells the local places. This has promoted better competitivity and efficiency. DPTCs are mostly controlled by local tourist operators, hotel companies and tourism leaders of the districts who have direct stake-hold in tourism activities in that district. So they aggressively promote their place.The best example is that of DTPC Alapuzha which aggressively pushed Alleppey to international popularity, with houseboats and backwater tourism. Perhaps you won’t see that spirit in some other DTPC like that of Kasargod or Kannur. So the destiny of tourism marketing of a destination is with the locals, not with few bureaucrats sitting in the capital. While Tamil Nadu tourism is still a capital-centric model like many other tourist boards across the country. Few bureaucrats in one city cannot design and push destinations located across a large state especially that of TN.As Kerala tourism (Department of Tourism) doesn’t do destination marketing, they have ample time and resources to push for many other important things. For example, the priority of Kerala tourism these days is RESPONSIBLE TOURISM initiatives, aiming to train stakeholders to improve their skills for responsible tourism.For example, Kerala tourism launched a scheme of Better Together, where they train locals for becoming responsible guides, cooks, community workers, model farmers, etcThe above ads weren’t meant for tourists. Its meant for Malayalee community, how to train themselves for becoming a better guide, better run a community kitchen or push farm tourism etc.Kerala tourism regularly conducts programs for such community training. The first of its series started with Kumarakom in Kottayam and by now, Kerala is a leader in RT activities as defined by UNWTO.Detailed presentation of Kerala Tourism- Responsible Tourism Initiatives that changed community life in those places where it was implemented. This is a presentation made by Tourism Director Dr. VenuThe aim is simple. Make tourism, a driver of the local economy and create sustainable economic activities within the state that can create more than 5 Lakh employment by 2021.All You Need to Know About Kerala Tourism's Responsible Tourismhttp://www.uniindia.com/kerala-s...Kerala's 'Responsible Tourism' initiative a role model, says UNWTOSo Kerala tourism, instead of being a tourism operator, ended up a training organization for effective organic farming or sustainable community monetary programs or small scale tourism employment programs etc.Such larger scale social activities are missing with other tourism boards like TN etc because its primary job is only to promote and push sightseeing activities in the stateEssentially Kerala tourism is definitely miles ahead than TN Tourism if one takes value and quality wise. Whereas in terms of quantity and volume, TN Tourism is definitely miles ahead than Kerala.
-
What is the best e-signature app?
What is Digital Signature? And Benefits of Digital Signature CertificatesA digital signature is basically a way to ensure that an electronic document (e-mail, spreadsheet, text file, etc.) is authentic. Authentic means that you know who created the document and you know that it has not been altered in any way since that person created it.Digital signatures rely on certain types of encryption to ensure authentication. Encryption is the process of taking all the data that one computer is sending to another and encoding it into a form that only the other computer will be able to decode. Authentication is the process of verifying that information is coming from a trusted source. These two processes work hand in hand for digital signatures.How do I get a Digital Signature?Digital Signature Certificate (DSC) is a secure digital key that certifies the identity of the holder, issued by a signNowing Authority (CA). There are many companies provide Digital Signature , i.e.SIFYeMudhra(n)codeThese companies gives LRA to several companies that are basically known as LRA. You may directly apply online and purchase from your local authority.signNow - offers a 14 day free trial and 3 types of pricing plans starting from $9.99 when paid monthly. All plans include sending unlimited amount of documents for signature. Available for Mac, iOS, Windows, Android and Web-browser.signNow - offers a 14 day free trial and 2 types of pricing plans starting from $29 when paid monthly. All plans include sending unlimited amount of documents for signature. Available for web-browser, iOS and Android.signNow - offers a 30 day free trial and 3 types of pricing plans starting from $15 when paid monthly. The number of document sends included each month differs by plan type. Available for Web-browser, iOS and Android.signNow - offers a 14-day free trial and 3 types of pricing plans starting from $15 per month when paid monthly. All plans include fair user restrictions to sign documents and send them for signature. Available for web-browser, iOS and Android.signNow - offers a 14-day free trial and 3 types of pricing plans starting from $15 per month when paid monthly. Unlimited document sending is subject to fair use thresholds. Available for Web-browser, iOS and Android.signNow - offers a free trial and 2 pricing plans starting from $16 per month when paid annually. All plans include sending unlimited amount of documents for signature. Available for web-browser, iOS and Android.Digital Signature for E-tenderingThere are three types of digital signature certificates depending on the validation of identity and type of use. They are:Class I DSC – Individuals get it for validating the email identification of the users and in situations where risk is minimal and here the signature is stored in software.Class II DSC – Business organizations or individuals use this digital signature certificate to validate the information given by the subscriber in the application against the information available in a trusted consumer database and in other such situations where security risk is moderate. In this case a hardware cryptographic device is used for storing the signature.Class III DSC – This digital certificate is directly issued by the signNowing authority and it is required that the person applying for DSC must be present at the signNowing authority’s premises and prove his/her identity in front of the authority and the security risk involved in this case is very high. In this case also a hardware cryptographic device is used for storing the signature.The Necessity of Digital Signature CertificatesFor e-filing of the income tax returns by any individual, the Government of India has made it mandatory to affix digital signatures to the income tax returns documents. For affixing the digital signature one must have digital signature certificates issued by licensed certification authority.In addition, Ministry of Corporate Affairs has set the mandatory guidelines for the companies directing them to file all reports, applications and forms using a digital signature only and this again requires a digital signature certificate.For GST also a company must verify its GST application by affixing a digital signature using digital signature certificate in order to get registered for GST.These days many Government procedures, filling different applications, amendments and forms require digital signatures made by using digital signature certificates.Benefits of Digital Signature CertificatesSaves Money & Time: As there is no need of physical presence you can digitally sign your PDF files and other documents using DSC anywhere & anytime. You need not sign your paper documents and then scan them to send them across through internet if you follow the above given option. You can save the money which would otherwise be spent on printing and scanning the document. You can also go green by saving paper.Secured Data: The digitally signed documents are tamper proof as the digital signatures are secured with a private key and public key and they cannot be edited after digitally signing the document.Authentic: Digitally signed documents are authentic and the receiver can be completely sure about the sender’s identity and integrity. The receiver can easily execute the information in the document without worrying about the document being forged.Certificate (DSC) is essential for companies and organizations that take part or intend to take part in eTendering processes on various Government sites. If a organisation going to apply for any Government eTender needs to have a Class 3 Digital Signature Certificate registered in the name of a representative who is authorized to submit online offers for e-Tendering applications.How to apply digital signature ?We enable compliance with legal and regulatory requirements for end-to-end electronic transactions for any kind of E-Business.What Documents required for Class 3 Digital Signature ?Documents required for Class 3 Digital SignatureApplication Form (Duly Signed)Recent Passport Size Photograph (Pasted on the Application form and Signed across the Photo)Identity ProofPAN CARD * (Income Tax F Filing Portal requires PAN Encrypted DSC)PassportDriving LicensePhoto ID Issued by Central Or State GovernmentVoter IDAadhar CardApply for Digital SignatureAddress ProofPassportDriving LicenseLatest Utility Bills - Not Older than 3 Months (Telephone, Electricity, Water, Tax, LIC)Ration CardVoter IDBank Account Statement ( Not Older than 2 Months)Service Tax/ VAT registration CertificateProperty tax/ Municipal tax ReceiptProof of Right to do Business (Any one of the Following)Certificate of IncorporationMemorandum of Association & Articles of associationRegistered Partnership deedValid Business licenses like VAT , Service Tax RegistrationLicense under shop and Establishment Act (For Proprietorship Concerns)PAN Card of the Company/FirmProof of Right to do Business (Any one of the Following)Latest annual Report / BalancesheetLatest Income Tax ReturnsOrganization Bank Details on Banks Letter Head/ Latest Bank statement attested by BankAuthorization Letter in Favor of the applicationAll Documents to be Self Attested by the applicant & Attested by the Authorised Signatory of the Business with Stamp & Seal. For More information about Best Digital Signature company in kanpurDifferent software solutions exist for different platforms, hence I am going to give one (the most common one) for each one of them:Windows: Open the PDF in signNow and click the “Fill & Sign” button in the right pane.Mac: Open the PDF in Preview, click the Toolbox button, then click SigniPhone and iPad: Open the PDF attachment in Mail, then click “Markup and Reply” to sign.iPhone and Android: Download signNow Fill & Sign, open the PDF, and tap the Signature button.Chrome: Install the signNow extension, upload your PDF, and click the Signature button.And you are good to go!!
-
Which kinds of business requires e-signatures?
What is Digital Signature? And Benefits of Digital Signature CertificatesA digital signature is basically a way to ensure that an electronic document (e-mail, spreadsheet, text file, etc.) is authentic. Authentic means that you know who created the document and you know that it has not been altered in any way since that person created it.Digital signatures rely on certain types of encryption to ensure authentication. Encryption is the process of taking all the data that one computer is sending to another and encoding it into a form that only the other computer will be able to decode. Authentication is the process of verifying that information is coming from a trusted source. These two processes work hand in hand for digital signatures.How do I get a Digital Signature?Digital Signature Certificate (DSC) is a secure digital key that certifies the identity of the holder, issued by a signNowing Authority (CA). There are many companies provide Digital Signature , i.e.SIFYeMudhra(n)codeThese companies gives LRA to several companies that are basically known as LRA. You may directly apply online and purchase from your local authority.signNow - offers a 14 day free trial and 3 types of pricing plans starting from $9.99 when paid monthly. All plans include sending unlimited amount of documents for signature. Available for Mac, iOS, Windows, Android and Web-browser.signNow - offers a 14 day free trial and 2 types of pricing plans starting from $29 when paid monthly. All plans include sending unlimited amount of documents for signature. Available for web-browser, iOS and Android.signNow - offers a 30 day free trial and 3 types of pricing plans starting from $15 when paid monthly. The number of document sends included each month differs by plan type. Available for Web-browser, iOS and Android.signNow - offers a 14-day free trial and 3 types of pricing plans starting from $15 per month when paid monthly. All plans include fair user restrictions to sign documents and send them for signature. Available for web-browser, iOS and Android.signNow - offers a 14-day free trial and 3 types of pricing plans starting from $15 per month when paid monthly. Unlimited document sending is subject to fair use thresholds. Available for Web-browser, iOS and Android.signNow - offers a free trial and 2 pricing plans starting from $16 per month when paid annually. All plans include sending unlimited amount of documents for signature. Available for web-browser, iOS and Android.Digital Signature for E-tenderingThere are three types of digital signature certificates depending on the validation of identity and type of use. They are:Class I DSC – Individuals get it for validating the email identification of the users and in situations where risk is minimal and here the signature is stored in software.Class II DSC – Business organizations or individuals use this digital signature certificate to validate the information given by the subscriber in the application against the information available in a trusted consumer database and in other such situations where security risk is moderate. In this case a hardware cryptographic device is used for storing the signature.Class III DSC – This digital certificate is directly issued by the signNowing authority and it is required that the person applying for DSC must be present at the signNowing authority’s premises and prove his/her identity in front of the authority and the security risk involved in this case is very high. In this case also a hardware cryptographic device is used for storing the signature.The Necessity of Digital Signature CertificatesFor e-filing of the income tax returns by any individual, the Government of India has made it mandatory to affix digital signatures to the income tax returns documents. For affixing the digital signature one must have digital signature certificates issued by licensed certification authority.In addition, Ministry of Corporate Affairs has set the mandatory guidelines for the companies directing them to file all reports, applications and forms using a digital signature only and this again requires a digital signature certificate.For GST also a company must verify its GST application by affixing a digital signature using digital signature certificate in order to get registered for GST.These days many Government procedures, filling different applications, amendments and forms require digital signatures made by using digital signature certificates.Benefits of Digital Signature CertificatesSaves Money & Time: As there is no need of physical presence you can digitally sign your PDF files and other documents using DSC anywhere & anytime. You need not sign your paper documents and then scan them to send them across through internet if you follow the above given option. You can save the money which would otherwise be spent on printing and scanning the document. You can also go green by saving paper.Secured Data: The digitally signed documents are tamper proof as the digital signatures are secured with a private key and public key and they cannot be edited after digitally signing the document.Authentic: Digitally signed documents are authentic and the receiver can be completely sure about the sender’s identity and integrity. The receiver can easily execute the information in the document without worrying about the document being forged.Certificate (DSC) is essential for companies and organizations that take part or intend to take part in eTendering processes on various Government sites. If a organisation going to apply for any Government eTender needs to have a Class 3 Digital Signature Certificate registered in the name of a representative who is authorized to submit online offers for e-Tendering applications.How to apply digital signature ?We enable compliance with legal and regulatory requirements for end-to-end electronic transactions for any kind of E-Business.What Documents required for Class 3 Digital Signature ?Documents required for Class 3 Digital SignatureApplication Form (Duly Signed)Recent Passport Size Photograph (Pasted on the Application form and Signed across the Photo)Identity ProofPAN CARD * (Income Tax F Filing Portal requires PAN Encrypted DSC)PassportDriving LicensePhoto ID Issued by Central Or State GovernmentVoter IDAadhar CardApply for Digital SignatureAddress ProofPassportDriving LicenseLatest Utility Bills - Not Older than 3 Months (Telephone, Electricity, Water, Tax, LIC)Ration CardVoter IDBank Account Statement ( Not Older than 2 Months)Service Tax/ VAT registration CertificateProperty tax/ Municipal tax ReceiptProof of Right to do Business (Any one of the Following)Certificate of IncorporationMemorandum of Association & Articles of associationRegistered Partnership deedValid Business licenses like VAT , Service Tax RegistrationLicense under shop and Establishment Act (For Proprietorship Concerns)PAN Card of the Company/FirmProof of Right to do Business (Any one of the Following)Latest annual Report / BalancesheetLatest Income Tax ReturnsOrganization Bank Details on Banks Letter Head/ Latest Bank statement attested by BankAuthorization Letter in Favor of the applicationAll Documents to be Self Attested by the applicant & Attested by the Authorised Signatory of the Business with Stamp & Seal. For More information about Best Digital Signature company in kanpurDifferent software solutions exist for different platforms, hence I am going to give one (the most common one) for each one of them:Windows: Open the PDF in signNow and click the “Fill & Sign” button in the right pane.Mac: Open the PDF in Preview, click the Toolbox button, then click SigniPhone and iPad: Open the PDF attachment in Mail, then click “Markup and Reply” to sign.iPhone and Android: Download signNow Fill & Sign, open the PDF, and tap the Signature button.Chrome: Install the signNow extension, upload your PDF, and click the Signature button.n short, “best” varies by your specific need - and there are dozens of comparison vectors. The 2 most important, IMHO, are do you needA “standing order” doc that can be easily signed anytime by anyone, such as an injury waiver at a karate school / trampoline park / etc- that sort of thing. The signor is not pre-defined. For that, we (SwiftCloud) may well be best, but there are dozens to compare, and important to consider is volume, HIPAA medical compliance, integration to marketing, etc.Specific doc / signor - such as a real estate sales contract. The parties are pre-defined, and automation can be added to flow from group 1 (say, “the seller(s)”) to group 2 (seller’s agent, for example) to group 3 (the buyer(s) consecutively or concurrently.The #1 reason to use e-signature is to save time + integration on the data i.e. so marketing is 100% automated for example, and reducing time-to-close which results in higher sales pull-through rates. Don’t get me wrong, saving money on paper, printer, ink, printer jams, etc. is important - but that’s a money saver, not a money maker. Marketing and sales will actually create new revenue for you, so to not use electronic signature is for most businesses, downright neglectful. Granted, I’m a bit biased, but happy to do a formal study to prove it with real numbers, should anyone be so inclined.And you are good to go!!
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
How to make an electronic signature from a scan?
How to make an esign document expire?
Get more for eSignature Presentation for Legal Free
Find out other eSignature Presentation for Legal Free
- Canlearn repayment assistance login form
- Aireco com credit application form
- Laboratory sop examples form
- Zoo application form
- Tsoa pdf form
- Business certificate dba form chemung county government
- Dj le 250b 66472921 form
- Jcrs authorship form
- Athlean xero download form
- Baptist health letterhead form
- Big tex dump trailer parts manual form
- Iowa ownership and disclosure form
- Mdr 501 form
- Old dominion university power of attorney form
- Heritage western cape application form
- Pima county deq notice of transfer form
- Certificate of motor insurance form
- Sunday catechism question paper pdf form
- 6105 marine corps form
- Singapore polytechnic entrance exam form