Draw eSignature Form Computer
Make the most out of your eSignature workflows with airSlate SignNow
Extensive suite of eSignature tools
Robust integration and API capabilities
Advanced security and compliance
Various collaboration tools
Enjoyable and stress-free signing experience
Extensive support
Keep your eSignature workflows on track
Our user reviews speak for themselves






How to create a digital signature using airSlate SignNow
In the contemporary digital landscape, the capability to create a digital signature is crucial for optimizing document signing procedures. airSlate SignNow provides an intuitive platform that enables individuals and businesses to generate, transmit, and oversee electronic signatures effectively. With its powerful features, it serves as a perfect answer for those aiming to streamline their signing operations.
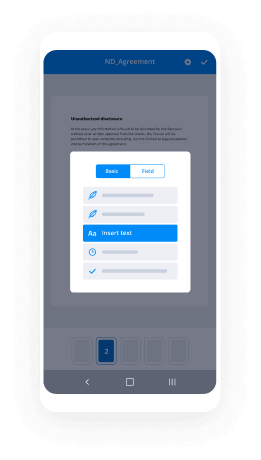
Instructions to create digital signature with airSlate SignNow
- Launch your web browser and go to the airSlate SignNow website.
- Either register for a complimentary trial or log into your current account.
- Choose the document you would like to upload for signing.
- If you intend to use this document regularly, consider transforming it into a reusable template.
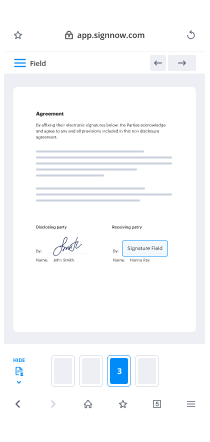
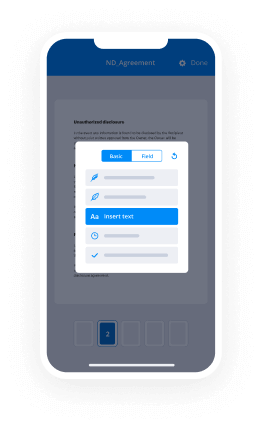
- Access the uploaded document and make necessary adjustments, such as adding fillable fields or inserting needed information.
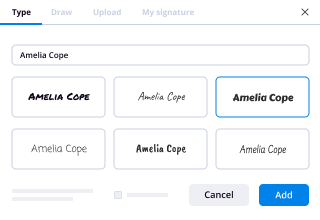
- Include your electronic signature and create signature fields for other signers.
- Click the 'Continue' button to set up and send an eSignature invitation.
By utilizing airSlate SignNow, you can signNowly improve your document signing experience. The platform not only saves time but also guarantees that your signing process is secure and adheres to industry regulations.
Ready to enhance your document management? Start your complimentary trial with airSlate SignNow today and enjoy the advantages of an easy-to-use electronic signature solution!
How it works
Rate your experience
-
Best ROI. Our customers achieve an average 7x ROI within the first six months.
-
Scales with your use cases. From SMBs to mid-market, airSlate SignNow delivers results for businesses of all sizes.
-
Intuitive UI and API. Sign and send documents from your apps in minutes.
A smarter way to work: —how to industry sign banking integrate
FAQs
-
What is the process to draw a computer signature using airSlate SignNow?
To draw a computer signature with airSlate SignNow, simply open the document you need to sign and select the signature field. You can choose the 'Draw' option, which allows you to use your mouse or touchscreen to create a custom signature. Once you're satisfied with your drawn signature, save it and place it within the document.
-
Are there any costs associated with drawing a computer signature on airSlate SignNow?
airSlate SignNow offers a range of pricing plans, including a free trial that allows users to explore the features, including the ability to draw a computer signature. Paid plans start at an affordable rate, providing additional features and enhanced capabilities for businesses looking to streamline their document signing process.
-
Can I save my drawn computer signature for future use?
Yes, airSlate SignNow allows you to save your drawn computer signature for future use. This feature makes it easy to sign documents quickly without having to redraw your signature every time. Simply save it in your account, and you can reuse it across multiple documents.
-
What are the benefits of using airSlate SignNow to draw a computer signature?
Using airSlate SignNow to draw a computer signature offers several benefits, including convenience, speed, and the ability to personalize your signature. This tool streamlines the signing process, reduces paperwork, and enhances the overall efficiency of document management.
-
Does airSlate SignNow integrate with other software for drawing computer signatures?
Yes, airSlate SignNow integrates seamlessly with various software applications, allowing users to draw computer signatures directly within their preferred platforms. This includes popular tools like Google Drive, Dropbox, and more, enhancing workflow efficiency and document handling.
-
Is it secure to draw a computer signature on airSlate SignNow?
Absolutely! airSlate SignNow prioritizes security and employs advanced encryption methods to protect your drawn computer signature and sensitive documents. This ensures that your signatures are safe and your data is secure during the eSigning process.
-
Can I draw a computer signature on mobile devices using airSlate SignNow?
Yes, you can easily draw a computer signature on mobile devices using the airSlate SignNow app. The mobile app is user-friendly and allows you to sign documents on the go, making it convenient to manage your signing tasks from anywhere.
-
Information Security: How can I get a Digital Signature?
Digital signatures are being widely used across the globe. There is a specific process to acquiring the signature. The way of acquisition is standard, no matter what country you’re trying to get the signature in. Digital signatures are created and issued by qualified individuals. For anyone to get a valid digital certificate, they must get it from a signNowing authority (CA). The signNowing Authority (CA) is a kind of Trust Service Provider - a third party provider designated and trusted by the country. It has the power of issuing citizens digital signatures. These CAs have rules and regulations they abide by. While in the USA, you can use the following CAs signNow US Globalsign Hello Sign When in the UK, you can use the following CAs signNow E-sign.co.uk signNow UK When you are in India, you can use the following CAs to get your digital signature certificate. eMudra Digital Signature India Government Approved signNowing Authorities These are some of the trusted sites that you can use to get your digital signature certificate in India, the UK, and the USA. They comply with every rule that governs electronic signatures, and you will get the best experience with them. Meanwhile, if you’re looking for e-signature software for your work, I recommend checking out signNow - with a high level of security, plenty of advanced features and overall ease of use, this application is a good fit for both small and medium-sized companies, startups, law-firms, and individual use as well. With signNow, you can: MANAGE SIGNATURE TASKS ● Visual progress bar - Monitor signature tasks by intuitively checking all signers’ status ● Timeline of Personal Activities - Display and record activities of all your personal tasks ● Void signature requests - Cancel signature tasks with one tap ●Search tool - Find your documents easily by searching with names of people or documents ASSIGN SIGNATURE TASKS TO MULTIPLE SIGNERS ●Invite multiple signers by adding them straight from your contact list or entering their email accounts ● Assign various fields to signers in a designated order, including signatures, texts, and dates ● Send documents to multiple signers at one time ● Show your signers where to fill in at a glance IMPORT DOCUMENTS TO START SIGNING ●Get documents from camera, photos, or the iOS file app ●Obtain documents from various cloud services, including Dropbox, Google Drive, and more ●Open-in documents from email attachments and the web PERSONALIZE YOUR SIGNATURES ● Create signatures with free-hand drawing ● Make stamps by using your camera or photos ● Pre-fill your personal information and quickly drag and drop it to the document ● Add signatures, initials, texts, and dates to documents All these features keep your documents well-organized, while the ability to track the entire signing process eases the overall task. With top-notch security, legally-binding audit trails and 2-factor authentication, this application will improve your workflow and save plenty of both time and money. Plus, the multi-platform option gives you the freedom to work across various devices. Disclaimer: I am part of Kdan’s team, and my answers might be a bit biased.
-
How do I register a trademark license? How do I create a digital signature?
If you want to register your trademark internationally, you will have to carefully consider in which countries you do. For example, it is usually unnecessary to register in 3 classes internationally, and one class is enough. The costs to register trademarks internationally are dependent on the country.As far as online signatures:It’s rather easy! All you need to do is go to Sign PDF Online with DigsignNower. Follow the instructions below and when you’re down, download the final image with the signature to your device.(Works on mobile devices as well!)Here’s a step-by-step guide, it only takes a few seconds to create a digital signature.1. Upload a fileStart out by simply clicking the choose file link to upload the PDF, Word, TXT, IMG, TXT or XLS document that you want to sign off. Alternatively, you can also grab it right from your desktop and drop it as shown in the image below:In just a few seconds your file will be fully available once the upload is completed.2. Apply your editsOnce you’re in, you will be able to select the type of edits you want to apply to your document.This tool is fully equipped with everything you need not only to create an electronic signature but also to fill out your forms online by adding text, selecting checkboxes, inserting the current date or even initialing where necessary.2.1 Create a free electronic signatureHover the mouse over the areas where you want to apply the edits.Feel free to sign documents the way you like. This signature maker tool offers three different options to create electronic signatures:A ) Draw an e-signature using a mouse or touchpad.B) Type your name, or scan an image of your signature.C) And last but not least, upload it to the document.2.2 Fill out the documentAs stated before, you can also add check marks, dates, text or initials in any page of your documents. Simply select the type of function you want to use, select the area and type in the information. Once you’re done click add.3. Download your document for free!When ready, clickto proceed. Our free tool will create a new file with the same format that can be downloaded completely for free without any type of registration!Click download and save the file on your computer.Here’s also a quick video demonstration on how to use this tool!
-
How do I add a digital signature in a WhatsApp image?
All you need to do is go to Sign PDF Online with DigsignNower. Follow the instructions below and when you’re down, download the final image with the signature to your device.(Works on mobile devices as well!)1. Upload a fileStart out by simply clicking the choose file link to upload the PDF, Word, TXT, IMG, TXT or XLS document that you want to sign off. Alternatively, you can also grab it right from your desktop and drop it as shown in the image below:In just a few seconds your file will be fully available once the upload is completed.2. Apply your editsOnce you’re in, you will be able to select the type of edits you want to apply to your document.This tool is fully equipped with everything you need not only to create an electronic signature but also to fill out your forms online by adding text, selecting checkboxes, inserting the current date or even initialing where necessary.2.1 Create a free electronic signatureHover the mouse over the areas where you want to apply the edits.Feel free to sign documents the way you like. This signature maker tool offers three different options to create electronic signatures:A ) Draw an e-signature using a mouse or touchpad.B) Type your name, or scan an image of your signature.C) And last but not least, upload it to the document.2.2 Fill out the documentAs stated before, you can also add check marks, dates, text or initials in any page of your documents. Simply select the type of function you want to use, select the area and type in the information. Once you’re done click add.3. Download your document for free!When ready, clickto proceed. Our free tool will create a new file with the same format that can be downloaded completely for free without any type of registration!Click download and save the file on your computer.Here’s also a quick video demonstration on how to use this tool!
-
What are the best electronic signature (e-signature) services?
Sometimes we really don’t understand what we mean under “best”, even this question doesn’t elaborate what the best service means? Which criteria the author believes the service fits the best? price?best design? Reliability?Let’s better talk about “suitable” for this moment and current needs.As the previous answers mentioned, do you need the service to be available on all major platforms or a signature that will stand up in court?Do you need a free simple solution, a feature-rich service that charges on the amount of signatures/documents signed or on monthly basis?Do you need to work with your documents on the go with low or no internet connection (while travelling, in the airport or plane)?And you can ask yourself with tons of such questions to create a matrix of features-service to choose the one you need. Or you can use 3rd party platforms like Alternativeto to initially select the provider you are interested in.When we conducted a closed beta testing for signNow recently, one of the goals was to understand the main criterias SMB owners from US use to choose a solution or switch to another one.We interviewed more than 230 businesses and what’s interesting, while the top factor goes to Security&data privacy, price or for example, digital signature availability is not in Top-3 of choices. Speed of an app/solution and multiplatform availability (works in web browser as well as on Mac, iPhone/iPad, Android and Windows devices) are what values higher.So, if there is a need to sign/send documents on Mac, iphone/ipad, android, windows and web browser and to work with documents offline, signNow is alternative to go with. We are still in beta, implementing some major requests from our beta users, but will be launching this September.And, signNow is free while in beta.
-
What are the cyber security laws that everyone must know?
According to Information Technology Act 2000(IT Act 2000) and its Amendment here are some of the list of law :OFFENCES:65. Tampering with computer source documents.Whoever knowingly or intentionally conceals, destroys or alters or intentionally or knowingly causes another to conceal, destroy, or alter any computer Source code used for a computer, computer programme, computer system or computer network, when the computer source code is required to be kept or maintained by law for the time being in force, shall be punishable with imprisonment up to three years, or with fine which may extend up to two lakh rupees, or with both.Explanation.–For the purposes of this section, “computer source code” means the listing of programmes, computer commands, design and layout and programme analysis of computer resource in any form.66. Computer related offences.–If any person, dishonestly or fraudulently, does any act referred to in section 43, he shall be punishable with imprisonment for a term which may extend to three years or with fine which may extend to five lakh rupees or with both.Explanation.–For the purposes of this section,–(a) the word “dishonestly” shall have the meaning assigned to it in section 24 of the Indian Penal Code (45 of 1860)(b) the word “fraudulently” shall have the meaning assigned to it in section 25 of the Indian Penal Code (45 of 1860).66A. Punishment for sending offensive messages through communication service, etc.–Any person who sends, by means of a computer resource or a communication device,–(a) any information that is grossly offensive or has menacing character; or(b) any information which he knows to be false, but for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred or ill will, persistently by making use of such computer resource or a communication device;(c) any electronic mail or electronic mail message for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages,shall be punishable with imprisonment for a term which may extend to three years and with fine.Explanation.–For the purpose of this section, terms “electronic mail” and “electronic mail message”means a message or information created or transmitted or received on a computer, computer system,computer resource or communication device including attachments in text, images, audio, video and anyother electronic record, which may be transmitted with the message.66B. Punishment for dishonestly receiving stolen computer resource or communication device.–Whoever dishonestly received or retains any stolen computer resource or communication device knowingor having reason to believe the same to be stolen computer resource or communication device,shall be punished with imprisonment of either description for a term which may extend to three years or with fine which may extend to rupees one lakh or with both.66C. Punishment for identity theft.–Whoever, fraudulently or dishonestly make use of theelectronic signature, password or any other unique identification feature of any other person,shall be punished with imprisonment of either description for a term which may extend to three years andshall also be liable to fine which may extend to rupees one lakh.66D. Punishment for cheating by personation by using computer resource.–Whoever, by meansof any communication device or computer resource cheats by personating, shall be punished withimprisonment of either description for a term which may extend to three years and shall also be liable tofine which may extend to one lakh rupees.66E. Punishment for violation of privacy.–Whoever, intentionally or knowingly captures, publishesor transmits the image of a private area of any person without his or her consent, under circumstancesviolating the privacy of that person, shall be punished with imprisonment which may extend to three yearsor with fine not exceeding two lakh rupees, or with both.Explanation.–For the purposes of this section–(a) “transmit” means to electronically send a visual image with the intent that it be viewed by a person or persons;(b) “capture”, with respect to an image, means to videotape, photograph, film or record by any means;(c) “private area” means the naked or undergarment clad genitals, public area, buttocks or female breast:(d) “publishes” means reproduction in the printed or electronic form and making it available for public;(e) “under circumstances violating privacy” means circumstances in which a person can have a reasonable expectation that–(i) he or she could disrobe in privacy, without being concerned that an image of his private area was being captured; or(ii) any part of his or her private area would not be visible to the public, regardless of whetherthat person is in a public or private place.67. Punishment for publishing or transmitting obscene material in electronic form.–Whoever publishes or transmits or causes to be published or transmitted in the electronic form, any material whichis lascivious or appeals to the prurient interest or if its effect is such as to tend to deprave and corruptpersons who are likely, having regard to all relevant circumstances, to read, see or hear the matter contained or embodied in it, shall be punished on first conviction with imprisonment of either descriptionfor a term which may extend to three years and with fine which may extend to five lakh rupees and in theevent of second or subsequent conviction with imprisonment of either description for a term which mayextend to five years and also with fine which may extend to ten lakh rupees.67A. Punishment for publishing or transmitting of material containing sexually explicit act, etc., in electronic form.–Whoever publishes or transmits or causes to be published or transmitted in theelectronic form any material which contains sexually explicit act or conduct shall be punished on firstconviction with imprisonment of either description for a term which may extend to five years and withfine which may extend to ten lakh rupees and in the event of second or subsequent conviction withimprisonment of either description for a term which may extend to seven years and also with fine whichmay extend to ten lakh rupees.67B. Punishment for publishing or transmitting of material depicting children in sexually explicit act, etc., in electronic form.–Whoever,–(a) publishes or transmits or causes to be published or transmitted material in any electronic formwhich depicts children engaged in sexually explicit act or conduct; or(b) creates text or digital images, collects, seeks, browses, downloads, advertises, promotes,exchanges or distributes material in any electronic form depicting children in obscene or indecent or sexually explicit manner;or(c) cultivates, entices or induces children to online relationship with one or more children for and on sexually explicit act or in a manner that may offend a reasonable adult on the computer resource;or(d) facilitates abusing children online, or(e) records in any electronic form own abuse or that of others pertaining to sexually explicit actwith children,shall be punished on first conviction with imprisonment of either description for a term which may extendto five years and with fine which may extend to ten lakh rupees and in the event of second or subsequentconviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees:Provided that provisions of section 67, section 67A and this section does not extend to any book,pamphlet, paper, writing, drawing, painting representation or figure in electronic form–(i) the publication of which is proved to be justified as being for the public good on theground that such book, pamphlet, paper, writing, drawing, painting representation or figure is theinterest of science, literature, art or learning or other objects of general concern; or(ii) which is kept or used for bonafide heritage or religious purposes.Explanation–For the purposes of this section, “children” means a person who has not completedthe age of 18 years.80. Power of police officer and other officers to enter, search, etc.–(1) Notwithstanding anythingcontained in the Code of Criminal Procedure, 1973 (2 of 1974), any police officer, not below the rank of a1[Inspector], or any other officer of the Central Government or a State Government authorised by theCentral Government in this behalf may enter any public place and search and arrest without warrant anyperson found therein who is reasonably suspected of having committed or of committing or of beingabout to commit any offence under this Act.Explanation.–For the purposes of this sub-section, the expression “public place” includes any publicconveyance, any hotel, any shop or any other place intended for use by, or accessible to the public.(2) Where any person is arrested under sub-section (1) by an officer other than a police officer, suchofficer shall, without unnecessary delay, take or send the person arrested before a magistrate havingjurisdiction in the case or before the officer-in-charge of a police station.(3) The provisions of the Code of Criminal Procedure, 1973 (2 of 1974) shall, subject to theprovisions of this section, apply, so far as may be, in relation to any entry, search or arrest, made underthis section.85. Offences by companies.–(1) Where a person committing a contravention of any of the provisionsof this Act or of any rule, direction or order made there under is a company, every person who, at the timethe contravention was committed, was in charge of, and was responsible to, the company for the conductof business of the company as well as the company, shall be guilty of the contravention and shall be liableto be proceeded against and punished accordingly:Provided that nothing contained in this sub-section shall render any such person liable to punishmentif he proves that the contravention took place without his knowledge or that he exercised all due diligenceto prevent such contravention.(2) Not with standing anything contained in sub-section (1), where a contravention of any of the provisions of this Act or of any rule, direction or order made thereunder has been committed by acompany and it is proved that the contravention has taken place with the consent or connivance of, or isattributable to any neglect on the part of, any director, manager, secretary or other officer of the company,
-
Does anyone know under which section of the law comes cyber crime or bsignNowing of data on the internet?
The Information Technology Act 2000 (amended in 2008)The Information Technology Act was first drawn up in 2000, and has been revised most recently 2008. The Information Technology (Amendment) Bill, 2008 amended sections 43 (data protection), 66 (hacking), 67 (protection against unauthorised access to data), 69 (cyberterrorism), and 72 (privacy and confidentiality) of the Information Technology Act, 2000, which relate to computer/cybercrimes.Section 43 [Penalty and Compensation for damage to computer, computer system, etc.] amended vide Information Technology Amendment Act 2008 reads as under:If any person without permission of the owner or any other person who is in-charge of a computer, computer system or computer network:accesses or secures access to such computer, computer system or computer network or computer resource (ITAA2008)downloads, copies or extracts any data, computer data base or information from such computer, computer system or computer network including information or data held or stored in any removable storage medium;introduces or causes to be introduced any computer contaminant or computer virus into any computer, computer system or computer network;damages or causes to be damaged any computer, computer system or computer network, data, computer data base or any other programmes residing in such computer, computer system or computer network;disrupts or causes disruption of any computer, computer system or computer network;denies or causes the denial of access to any person authorized to access any computer, computer system or computer network by any means;provides any assistance to any person to facilitate access to a computer, computer system or computer network in contravention of the provisions of this Act, rules or regulations made there under;charges the services availed of by a person to the account of another person by tampering with or manipulating any computer, computer system, or computer network;destroys, deletes or alters any information residing in a computer resource or diminishes its value or utility or affects it injuriously by any means (Inserted vide ITAA-2008); andSteals, conceals, destroys or alters or causes any person to steal, conceal, destroy or alter any computer source code used for a computer resource with an intention to cause damage, (Inserted vide ITAA 2008) he shall be liable to pay damages by way of compensation to the person so affected. (change vide ITAA 2008)Critique: In comparison to the laws enacted in other countries, this provision still falls short of a strong data protection law. In most other countries data protection laws specify:the definition and classification of data types;the nature and protection of the categories of data;that equal protection will be given to data stored offline and data stored manually;that data controllers and data processors have distinct roles;clear restrictions on the manner of data collection;clear guidelines on the purposes for which the data can be put and to whom it can be sent;standards and technical measures governing the collection, storage, access to, protection, retention, and destruction of data;that providers of goods or services must have a clear opt - in or opt - out option; andin addition, most countries provide strong safeguards and penalties against bsignNowes of any of the aboveSection 66 [Computer Related Offences] amended vide Information Technology Amendment Act 2008 reads as under:If any person, dishonestly, or fraudulently, does any act referred to in section 43, he shall be punishable with imprisonment for a term which may extend to two three years or with fine which may extend to five lakh rupees or with both.Explanation: For the purpose of this section,-the word "dishonestly" shall have the meaning assigned to it in section 24 of the Indian Penal Code;the word "fraudulently" shall have the meaning assigned to it in section 25 of the Indian Penal Code. [Section 66 A] [Punishment for sending offensive messages through communication service, etc.] (Introduced vide ITAA 2008):Any person who sends, by means of a computer resource or a communication device,-any information that is grossly offensive or has menacing character; orany information which he knows to be false, but for the purpose of causing annoyance, inconvenience, danger, obstruction, insult, injury, criminal intimidation, enmity, hatred, or ill will, persistently makes by making use of such computer resource or a communication device;any electronic mail or electronic mail message for the purpose of causing annoyance or inconvenience or to deceive or to mislead the addressee or recipient about the origin of such messages (Inserted vide ITAA 2008) shall be punishable with imprisonment for a term which may extend to three years and with fine.Explanation: For the purposes of this section, terms "Electronic mail" and "Electronic Mail Message" means a message or information created or transmitted or received on a computer, computer system, computer resource or communication device including attachments in text, image, audio, video and any other electronic record, which may be transmitted with the message.[Section 66 B] [Punishment for dishonestly receiving stolen computer resource or communication device] (Inserted Vide ITA 2008):Whoever dishonestly receives or retains any stolen computer resource or communication device knowing or having reason to believe the same to be stolen computer resource or communication device, shall be punished with imprisonment of either description for a term which may extend to three years or with fine which may extend to rupees one lakh or with both.[Section 66C] [Punishment for identity theft] (Inserted Vide ITA 2008):Whoever, fraudulently or dishonestly make use of the electronic signature, password or any other unique identification feature of any other person, shall be punished with imprisonment of either description for a term which may extend to three years and shall also be liable to fine which may extend to rupees one lakh.[Section 66D] [Punishment for cheating by personation by using computer resource] (Inserted Vide ITA 2008):Whoever, by means of any communication device or computer resource cheats by personation, shall be punished with imprisonment of either description for a term which may extend to three years and shall also be liable to fine which may extend to one lakh rupees.[Section 66E] [Punishment for violation of privacy] (Inserted Vide ITA 2008):Whoever, intentionally or knowingly captures, publishes or transmits the image of a private area of any person without his or her consent, under circumstances violating the privacy of that person, shall be punished with imprisonment which may extend to three years or with fine not exceeding two lakh rupees, or with bothExplanation - For the purposes of this section--“transmit” means to electronically send a visual image with the intent that it be viewed by a person or persons;“capture”, with respect to an image, means to videotape, photograph, film or record by any means;“private area” means the naked or undergarment clad genitals, pubic area, buttocks or female breast;“publishes” means reproduction in the printed or electronic form and making it available for public;“under circumstances violating privacy” means circumstances in which a person can have a reasonable expectation that:he or she could disrobe in privacy, without being concerned that an image of his private area was being captured; orany part of his or her private area would not be visible to the public, regardless of whether that person is in a public or private place.[Section 66F] [Punishment for cyber terrorism]:(1) Whoever,-(A) with intent to threaten the unity, integrity, security or sovereignty of India or to strike terror in the people or any section of the people by –denying or cause the denial of access to any person authorized to access computer resource; or attempting to penetrate or access a computer resource without authorisation or exceeding authorized access; orintroducing or causing to introduce any Computer Contaminant and by means of such conduct causes or is likely to cause death or injuries to persons or damage to or destruction of property or disrupts or knowing that it is likely to cause damage or disruption of supplies or services essential to the life of the community or adversely affect the critical information infrastructure specified under section 70, or(B) knowingly or intentionally penetrates or accesses a computer resource without authorization or exceeding authorized access, and by means of such conduct obtains access to information, data or computer database that is restricted for reasons of the security of the State or foreign relations; or any restricted information, data or computer database, with reasons to believe that such information, data or computer database so obtained may be used to cause or likely to cause injury to the interests of the sovereignty and integrity of India, the security of the State, friendly relations with foreign States, public order, decency or morality, or in relation to contempt of court, defamation or incitement to an offence, or to the advantage of any foreign nation, group of individuals or otherwise, commits the offence of cyber terrorism.(2) Whoever commits or conspires to commit cyber terrorism shall be punishable with imprisonment which may extend to imprisonment for life’.Critique: We find the terminology in multiple sections too vague to ensure consistent and fair enforcement. The concepts of ‘annoyance’ and ‘insult’ are subjective. Clause (d) makes it clear that phishing requests are not permitted, but it is not clear that one cannot ask for information on a class of individuals.Section 67 [Publishing of information which is obscene in electronic form] amended vide Information Technology Amendment Act 2008 reads as under:Whoever publishes or transmits or causes to be published in the electronic form, any material which is lascivious or appeals to the prurient interest or if its effect is such as to tend to deprave and corrupt persons who are likely, having regard to all relevant circumstances, to read, see or hear the matter contained or embodied in it, shall be punished on first conviction with imprisonment of either description for a term which may extend to two three years and with fine which may extend to five lakh rupees and in the event of a second or subsequent conviction with imprisonment of either description for a term which may extend to five years and also with fine which may extend to ten lakh rupees.[Section 67 A] [Punishment for publishing or transmitting of material containing sexually explicit act, etc. in electronic form] (Inserted vide ITAA 2008):Whoever publishes or transmits or causes to be published or transmitted in the electronic form any material which contains sexually explicit act or conduct shall be punished on first conviction with imprisonment of either description for a term which may extend to five years and with fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees.Exception: This section and section 67 does not extend to any book, pamphlet, paper, writing, drawing, painting, representation or figure in electronic form-the publication of which is proved to be justified as being for the public good on the ground that such book, pamphlet, paper, writing, drawing, painting, representation or figure is in the interest of science, literature, art, or learning or other objects of general concern; orwhich is kept or used bona fide for religious purposes.[Section 67 B] Punishment for publishing or transmitting of material depicting children in sexually explicit act, etc. in electronic form:Whoever,-(a) publishes or transmits or causes to be published or transmitted material in any electronicform which depicts children engaged in sexually explicit act or conduct or(b) creates text or digital images, collects, seeks, browses, downloads, advertises,promotes, exchanges or distributes material in any electronic form depicting children inobscene or indecent or sexually explicit manner or(c) cultivates, entices or induces children to online relationship with one or more children forand on sexually explicit act or in a manner that may offend a reasonable adult on the computer resource or(d) facilitates abusing children online or(e) records in any electronic form own abuse or that of others pertaining to sexually explicit act with children, shall be punished on first conviction with imprisonment of either description for a term which may extend to five years and with a fine which may extend to ten lakh rupees and in the event of second or subsequent conviction with imprisonment of either description for a term which may extend to seven years and also with fine which may extend to ten lakh rupees:Provided that the provisions of section 67, section 67A and this section does not extend to any book, pamphlet, paper, writing, drawing, painting, representation or figure in electronic form-(i) The publication of which is proved to be justified as being for the public good on the ground that such book, pamphlet, paper writing, drawing, painting, representation or figure is in the interest of science, literature, art or learning or other objects of general concern; or(ii) which is kept or used for bonafide heritage or religious purposes Explanation: For the purposes of this section, "children" means a person who has not completed the age of 18 years. [Section 67 C] [Preservation and Retention of information by intermediaries]:(1) Intermediary shall preserve and retain such information as may be specified for such duration and in such manner and format as the Central Government may prescribe.(2) Any intermediary who intentionally or knowingly contravenes the provisions of sub section (1) shall be punished with an imprisonment for a term which may extend to three years and shall also be liable to fine.Critique: This provision adequately protects both the corporate and the citizen in a positive way.Section 69 [Powers to issue directions for interception or monitoring or decryption of any information through any computer resource] amended vide Information Technology Amendment Act 2008 reads as under:(1) Where the central Government or a State Government or any of its officer specially authorized by the Central Government or the State Government, as the case may be, in this behalf may, if is satisfied that it is necessary or expedient to do in the interest of the sovereignty or integrity of India, defense of India, security of the State, friendly relations with foreign States or public order or for preventing incitement to the commission of any cognizable offence relating to above or for investigation of any offence, it may, subject to the provisions of sub-section (2), for reasons to be recorded in writing, by order, direct any agency of the appropriate Government to intercept, monitor or decrypt or cause to beintercepted or monitored or decrypted any information transmitted received or stored through any computer resource.(2) The Procedure and safeguards subject to which such interception or monitoring or decryption may be carried out, shall be such as may be prescribed.(3) The subscriber or intermediary or any person in charge of the computer resource shall, when called upon by any agency which has been directed under sub section (1), extend all facilities and technical assistance to –(a) provide access to or secure access to the computer resource generating, transmitting, receiving or storing such information; or(b) intercept or monitor or decrypt the information, as the case may be; or (c) provide information stored in computer resource.(4) The subscriber or intermediary or any person who fails to assist the agency referred to in sub-section (3) shall be punished with an imprisonment for a term which may extend to seven years and shall also be liable to fine.[ Section 69B] Power to authorize to monitor and collect traffic data or information through any computer resource for Cyber Security:(1) The Central Government may, to enhance Cyber Security and for identification, analysis and prevention of any intrusion or spread of computer contaminant in the country, by notification in the official Gazette, authorize any agency of the Government to monitor and collect traffic data or information generated, transmitted, received or stored in any computer resource.(2) The Intermediary or any person in-charge of the Computer resource shall when called upon by the agency which has been authorized under sub-section (1), provide technical assistance and extend all facilities to such agency to enable online access or to secure and provide online access to the computer resource generating, transmitting, receiving or storing such traffic data or information.(3) The procedure and safeguards for monitoring and collecting traffic data or information, shall be such as may be prescribed.(4) Any intermediary who intentionally or knowingly contravenes the provisions of subsection(2) shall be punished with an imprisonment for a term which may extend to three years and shall also be liable to fine.Explanation: For the purposes of this section,(i) "Computer Contaminant" shall have the meaning assigned to it in section 43(ii) "traffic data" means any data identifying or purporting to identify any person, computer system or computer network or location to or from which the communication is or may be transmitted and includes communications origin, destination, route, time, date, size, duration or type of underlying service or any other information.Critique: Though we recognize how important it is for a government to protect its citizens against cyberterrorism, we are concerned at the friction between these provisions and the guarantees of free dialog, debate, and free speech that are Fundamental Rights under the Constitution of India.Specifically:a) there is no clear provision of a link between an intermediary and the information or resource that is to be monitored.c)the penalties laid out in the clause are believed to be too harsh, and when read in conjunction with provision 66, there is no distinction between minor offenses and serious offenses.e) the ITA is too broad in its categorization of acts of cyberterrorism by including information that is likely to cause: injury to decency, injury to morality, injury in relation to contempt of court, and injury in relation to defamation.Section 72 [BsignNow of confidentiality and privacy] amended vide Information Technology Amendment Act 2008 reads as under:Save as otherwise provided in this Act or any other law for the time being in force, any person who, in pursuant of any of the powers conferred under this Act, rules or regulations made there under, has secured access to any electronic record, book, register, correspondence, information, document or other material without the consent of the person concerned discloses such electronic record, book, register, correspondence, information, document or other material to any other person shall be punished with imprisonment for a term which may extend to two years, or with fine which may extend to one lakh rupees, or with both. [Section 72 A] Punishment for Disclosure of information in bsignNow of lawful contract (Inserted vide ITAA-2008):Save as otherwise provided in this Act or any other law for the time being in force, any person including an intermediary who, while providing services under the terms of lawful contract, has secured access to any material containing personal information about another person, with the intent to cause or knowing that he is likely to cause wrongful loss or wrongful gain discloses, without the consent of the person concerned, or in bsignNow of a lawful contract, such material to any other person shall be punished with imprisonment for a term which may extend to three years, or with a fine which may extend to five lakh rupees, or with both.General Notes and Critiques:As general notes on the ITA and data protection we find that the Act is lacking in many ways, including:there is no definition of “sensitive personal data or information” and that term is used indiscriminately without.the provisions and protections cover only electronic data and not stored data or non-electronic systems of mediain the absence of a data controller, liability is often imposed on persons who are not necessarily in a position to control datacivil liability for data bsignNow arises where negligence is involvedcriminal liability only applies to cases of information obtained in the context of a service contract.**I am neither a student of law nor attached in any way to the legal system. This is excerpted from Cybercrime and Privacy and merely reproduced here for the sake of convenience.
-
What is the process of the e-Tendering registration?
e-Tendering is a procedure of obtaining the things electronically utilizing web. This office definitely lessens the acquirement process duration and decreases the vast majority of the circuitous expenses in the event that you enroll on e-Tendering, you can have entry to the tenders data,empower you to buy delicate calendars and submit them on the web.Free and reasonable cooperation is conceivable with more straightforwardness.Enrollment for Tender Registration is extremely straightforward as:Go to Tenders Page and simply top off the enrollment frame arranged by us .We will empower your ID on e-Tendering.Subsequent to enrolling on e-Tendering,you are given client ID and secret word.You can only login to the site utilizing this data.You can utilize your record anyplace on the planet. It simply require a PC with above Pentium II setup and a web association.Secret word is encoded at the database level. It is known just to you.Indeed,even the System Administrator does not know your watchword. As a part of the security approach,we encourage you to change the secret word much of the time.Subsequent to enrolling on e-Tendering,you would frequently sign into your record and can discover the data in regards to tenders.You will likewise get a mail notice with respect to the production of the delicate notice.The delicate can be downloaded from the e-Tendering webpage on paying the essential expense. You can fill the delicate archives and submit online alongside the examined endorsements required for the tender.Drawings are a piece of the delicate reports. While downloading the delicate records, these drawings were additionally downloaded.In the wake of enrolling on e-Tendering, you are furnished with required space online for putting away your data as examined duplicates, for example, encounter testaments and so forth. You could go to "Alter Profile" and join/transfer any number of archives/certificates.Once stacked, these can be utilized more than once for every future delicate.BG/DD taken for EMD are checked and ought to be appended to the specialized offered amid accommodation. The firsts can be given over to the office amid the specialized offer opening.After presenting your delicate, you will get a receipt mail giving the status of the accommodation.At the point when your offer is opened you will get a mail warning illuminating the subtle elements, for example, the offer has been opened by the official, office and date and time of opening.
Trusted esignature solution— what our customers are saying
Get legally-binding signatures now!
Frequently asked questions
How do i add an electronic signature to a word document?
What is an eSign message?
How to do an electronic signature for court?
Get more for Draw eSignature Form Computer
- Can I eSign Montana Employee Incident Report
- eSign Hawaii CV Form Template Online
- eSign Idaho CV Form Template Free
- How To eSign Kansas CV Form Template
- eSign Nevada CV Form Template Online
- eSign New Hampshire CV Form Template Safe
- eSign Indiana New Hire Onboarding Online
- eSign Delaware Software Development Proposal Template Free
Find out other Draw eSignature Form Computer
- Amenity form
- Ignition interlock program non owned vehicle installation approval created 312 washington state patrol impaired driving section form
- Oklahoma insurance department state of oklahoma surplus lines insurance broker form sl3c quarter ampamp ok
- Cleveland clinic discharge papers form
- Charles p allen form
- 61 1re form
- Transcript student request form
- Application to vary suspend or attachment order cancel justice govt form
- Cfis form
- Member companies of western world insurance group western form
- Australia nhvr road train form
- Brentalb application the brealtyb company ltd form
- Mobile county probate court forms
- Npi instructions form
- Post secondary student support program onionlake form
- Guilbault bol form
- Amadeus movie worksheet pdf form
- Discretionary housing payment halifax form
- L r reed melbourne form
- Fl school transcript request form