Industry sign banking mississippi pdf secure
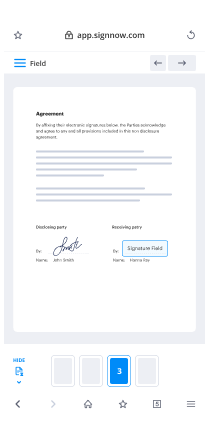
um my name is vladislav mladna for just vladi if you have some questions to me and this is fabian and we are allowed today to talk about how to break pdf security or more special about how to break the cryptography operations in pdf files we are a large team from university on bohom minster and hackman gamberha so um as i mentioned we will talk about cryptography in pdf files does it work all right okay let's try that again okay perfect this talk will consist of two parts the first part is about digitally signed pdf files and how can we recognize such files if we open them we see the information regarding the that the file was signed and all verification procedures were valid and more information regarding the signature validation panel and information about who signed this file this is the first part of the talk and i will present this topic and the second part is regarding pdf encrypted files and how can we recognize such files if we you try to open such files the first thing you see is the password prompt and after entering the correct password the file is decrypted and you can read the content within this file if you open it with adobe additional information regarding if this file is secured or not is displayed further and this is the second part of our talk and fabian we will talk how can we break the pdf encryption so before we start with the attacks on signatures or encryption we first need some basics and after six slides you will be experts regarding pdf files and you will understand everything about it but um maybe it's a little bit boring so be patient there are only six slides so the first is quite easy pdf files are um the first specification was in 1993 and almost at the beginning uh pdf cryptography operations like signatures and encryption was already there the last version is pdf 2.0 and it was released in 2017 and according to adobe 1.6 billion files um are on the web and perhaps more exchange beyond the web so basically pdf files are everywhere and that's the reason why we considered this topic and tried to find or to analyze the security of the features if we have some very simple file and we open it with adobe reader the first thing we see is of course the content hello world in this case and additional information regarding the focus page and how many pages this document has but what would happen if we don't use a pdf viewer and you just use some text editor we used the notepad plus plus to open and um later manipulate the files so i will zoom this thing this file and the first thing we see is that we can read it perhaps it's quite um quite funny and um but we can still extract some information from of this file for example some information regarding the pages and here you can see the information that one page the the pdf file consists of one page but more interesting is that we can see the content of the file itself so the lessons we learned is that we can use a simple text editor to view and edit pdf files and for our attacks we use only this text editor so let's go to the details how pdf files are structured and how they are processed pdf files consists of four parts header body and body is the most important part of the pdf files um this the body contains the entire information presented to the user and two other sections extra section and trailer very important thing about processing pdf files is that their process not from the top to the bottom but from the bottom to the top so the first thing is the pdf viewer analyzes or processes is the trailer so let's start um doing that what information is starting this trailer basically there are two very important informations on the first side this is the information what is the root element of this pdf so which is the first object which will be processed and the second important information is where the xref section starts it's a just a byte offset pointing to the position of this extra sections within the pdf file so this pointer as mentioned before points to the xref section but what is the extra section about the extra section is a catalog pointing or holding the information where the objects defined in the body are contained or the byte positions of this object so how can we read this weird x-ray section the first thing the first information we extract is that the first object which is defined here is the object with the id 0 and we have five further elements or objects which are defined so the first object is here the first entry is the byte position within the file the second is its generation number and the last character points if this object is used or not used so reading it reading this x-ray section we extract the information that the object with the d0 is the posit at the byte position zero and it's not in use so the first the object with the id one is at the position nine and so on and so forth so for the object with a d4 and the object number comes from counting it zero one two three and four so the object with the d4 um can be fined at the position at offset and is in use in other words the pdf viewer knows where each object will be fined and can properly displace it and process it now we come to the most important part the body and i mentioned it that in the body the entire content which is presented to the user is contained so let's see object 4 0 is this one and as you can see it contains the world hello world the other objects are referenced too so each pointer points exactly to the starting position of each of the objects and how can we read this object you see we have object starting with the id number with then the generation number and the word opt so you can now um you now know where the object is starts and when it ends now how can we process this body as i mentioned before in the trailer there was a reference regarding the root element and this element was with the id one and generation number zero so we now we start reading the document here and we have a catalog and a reference to some pages pages is just a description of all the pages contained within the file and what can we see here is that we have this number count one so we have only one page and a reference to the page object which contains the entire information description of the page if we have multiple pages then we will have here multiple elements then we have one page and here we have the contents which is a reference to the string we already saw perfect if you understand this then you know everything or almost everything about pdf files now you can just use your editor and open such files and analyze them then we need one feature i forgot the last part the most simple simple one the header it's just one line stating which version is used for example in our case 1.4 for the last version of adobe here will be stated 2.0 now we need this one feature called incremental update and i call this feature do you know this features highlighting something in the pdf file or putting some sticky notes technically it's called incremental update i just call it reviewing master and bachelor thesis of my students because this is exactly the procedure i follow i just read the text and highlight something and store the information i put at it technically by putting such a sticky note this additional information is appended after the end of the file so we have a body update which contains exactly the information only of the additionally of the new objects and of course new x-ray section and of a new trailer pointing to this new object okay we are done how can considering incremental update um we sell that it is used to put for for mainly for sticky notes or highlighting but we observed something which is very important because in incremental update we can um redefine existing objects for example we can define redefine the object with the d4 and put new content so we replace in this manner the world hello world with uh with another sentence and of course the x-ray section and the trailer point to these new objects so this is very important so we we are not with incremental update we are not stick to only um adding some highlighting or notes we can redefine already existing content and perhaps we need this for the attacks we will present so let's talk about pdf signatures first we need a difference between electronic signature and digital signature electronic signature from a technical point of view is just an image i just um routed it on my pc and put it into the file there is no cryptographic protection it could be me lying on the beach doing something from cryptographic point of view is the same it does not provide any security any cryptographic security what we will talk here is about digitally signed files so if you open such files um you have the additional information regarding um the validation about the signatures and who signed this pdf file so as i mentioned before this talk will concentrate only on this digitally signed pdf files how what kind of process is behind digitally signing pdf files imagine we have this abstract overview of a pdf document we have the header body extra section and trailer and we want to sign it what happens is that we take this pdf file and via incremental update we put additional information regarding the there is a new catalog and more important a new signature object containing the signature value and information about who signed this pdf file and of course there is a xref section and trailer and relevant for you the entire file is now protected by the pdf signature so manipulations within this area should not be possible right yeah let's talk about this how why it's not possible and how can we break it first we need attack a scenario what we want to achieve as an attacker we assumed in our research that the attacker possess this signed pdf file this could be an old contract receipt or um in our case a bill from amazon and if we open this file the signature is valid so everything is green no warning are thrown and everything is fine what we try to do is to take this file manipulate it somehow and then send it to the victim and now the victim expects to receive a digitally signed pdf file so just tripping the digital signature is a very trivial scenario and we did not consider it because it's trivial we considered that the victim expects to see that there is a signature and it is valid so no warning are thrown and the entire left side is exactly the same from the novel normal behavior but on the other side the content was exchanged so we um we manipulated the receipt and exchanged it with another content the question is now how can we do it on a technical level and we came up with three attacks um incremental saving attacks signature wrapping and universal signature forgery and i will now introduce the techniques and how these attacks are working the first attack is the incremental saving attack so i mentioned before that via incremental saving core by incremental updates we can add and remove and even redefine already existing objects and the signature still stays valid why is this happening consider now again our case we have some header body xrf table and trailer and the file is now signed and the signature protects only designed area so what would happen if i put a sticky note or some highlighting an incremental update happens if i open this file usually this happens we have the information that this signature is valid when it was signed and so on and so forth so our first idea was to just put new body updates redefine already existing content and with the xraf table and trailer we point to the new content this is quite trivial because it's a legitimate feature in pdf files so we didn't expect to be quite successful and we were not so successful um but the first idea we applied this attack we opened it and we got this message so it's kind of a weird message because uh an experienced user sees valid but the document has been updated and you should know what does this exactly mean but we did not consider this attack as a successful because um there's there the warning is not the same or the status of the signature validation is not the same so what we did is to evaluate this first against this trivial case against all that all the viewers we have and libreoffice for example was vulnerable against this trivial attack on this was the only viewer which was vulnerable against this trivial variation but then we asked ourselves okay the other viewers are quite secure but how do they detect this incremental updates and from developer point of view the laziest thing we can do is just to check if another extra tailor a table and trailer were added after the signature was applied so we just put our body updates but just deleted the other two parts this is not a standard compliant pdf file it's broken but our hope was that the pdf viewer fix this kind of stuff for us and are that these viewers are error tolerant and we were quite successful because the verification logic just checked is there an extra table and trailer after the signature was applied no okay everything is fine the signature is valid no warning was thrown but then the application logic so that incremental updates were applied and fixed this for us and processed this body updates and no warning was thrown some of the viewers required to have a trailer i don't know why it was a black black box testing so we just removed the x-ray table but the trail was there and we were able to broke further pdf viewers the most complex variation of the attack was the following we had the pdf viewers checked if every incremental update contains a signature object but they did not check if this signature is covered by the incremental update so we just copy pasted the signature which was provided here here and we just forced the pdf viewer to validate this signed content twice and still our body updates were implemented were processed and for example foxhit or masterpdf were vulnerable against this kind this type of attack so the violation of our attacks we consider it in uh as part of our evaluation um 22 different viewers among others adobe with different versions foxhead and so on and as you can see 11 of 22 were vulnerable against incremental saving so 50 and we were quite surprised because we saw that the developers so that incremental updates could be dangerous regarding the signature validation but we were still able to bypass um their considerations we had a full signature bypass means that there is no possibility for the victim to detect the attack a limited signature bypass means that the victim if the victim clicks on one at least one additional window and explicitly wants to validate the signature then the viewer was vulnerable but the most important thing is by opening the file there was a status message that the signature validation and all signatures are valid so this was the first layer and the viewers were vulnerable against this so let's talk about the second attack class we called it signature wrapping attack and this is the most complex attack of the all three classes and now we have to go a little bit into the details how pdf signatures are made so imagine now we have a pdf file we have some header and the original document the original document contains the header the body the extra section and so on and so forth and we want to sign this document technically again an incremental update is provided and we have a new catalog here we have some other objects for example um certificates and so on and the signature objects and we will now concentrate on this signature object because it's essential for the attack we want to to carry out and the signature object contains a lot of information but we want for this attacks only two elements are relevant the contents and the byte range the contents contains the signature value it's a pica cs7 container containing the signature value and the certificates used to validate the signature and the byte range the byte range contains four different values and what how these values are being used the first two a and b define define the first signed area and this is here from the beginning of the document until the start of the signature value why we need this because the signature value is part of the side area so we need to exclude the signature value from the document computation and
this is how the byte range is used the first part is and from the beginning of the document until the signed the signature value starts and after the signature ends until the end of the file um is the second area specified by the two digits c and d so now we have everything protected besides the signature value itself what we wanted to try is to create additional space for our attacks so our idea was to move the second signed area and how can we do it so basically we can do it by just defining another byte range and as you can see here the byte range points from area a to b so this area we didn't made any manipulation in this part right it was not modified at all so it's still valid and the second part the new c value and the next d bytes we didn't change anything here right so basically we didn't change anything in the signed area and the signature is still valid but what we created was a space for some malicious objects um sometimes we needed some padding and a new x-ray section pointing to these malicious objects important thing was that this malicious x-ray sections the position is defined by the trailer and since we cannot modify this trailer this position is fixed so this is the only limitation of the attack but it works like a charm and the question is now how many uh pdf viewers were volume against this attack and as you can see this is the signature wrapping column 17 out of 22 applications was were vulnerable against this attack this was a quite expected result because the attack was complex we saw that many developers didn't were not aware of this threat and um that's the reason why so many vulnerabilities were there now to the last class of attacks universal signature forgery and we called it universal signature forgery but i prefer to use another definition for this attacks i call them stupid implementation flaws um we are coming from the pen testing area and i know a lot of you are pen testers too and many of you have experienced quite interesting experience with zero bytes null values or some kind of weird values and this is what we tried in this kind of attacks just try to do some stupid values or remove references and see what happen considering the signature there are two different um important elements the contents containing the signature value and the byte range pointing to what is exactly signed so what would happen if we removed the contents our hope was that the information regarding the signature is still shown by the viewer as valid without validating any signature because it was not possible and by just removing the signature value is quite obvious idea and we were not successful with this kind of attack but let's proceed with another values like for example contents without any value or contents like equals null or zero bytes and considering this last version we had two viewers which were vulnerable against this attack and um another um another case is uh for example by removing the byte range by removing this byte range we have some signature value but we we don't know what is exactly signed so um we tried this attack and of course byte range without any value or null bytes or byte range with a minus or negative negative numbers and usually this last crashed very a lot of years but the most interesting is that adobe made this mistake by just removing the byte range we were able to bypass the entire security we didn't expect this behavior but it was a stupid implementation flaw allowing us to do anything in this document and all the exploits we show in our presentations were made on adobe with this attack so let's see what were the results of this attack as you can see only four of 22 viewers were vulnerable against this attack and only adobe unlimited for the others there was limitation because if you click on the signature validation um then warning was thrown it was very easy for adobe to fix and as you can see adobe didn't mistake um made any mistake regarding incremental saving and signature wrapping but regarding universal signature forgery they were vulnerable against this attack and this was the hope of our approach in summary we were able to break 21 of 22 pdf viewers the only thanks the only secure pdf viewer is adobe 9 which is um deprecated and has remote code execution the only the only users allowed to use them or are using it are linux users because this is the last version available for linux and that's the reason why you consider it so i'm done with the talk about pdf signatures and now fabian can talk about pdf encryption thank you yes okay now that we've dealt with signatures let's talk about another cryptographic aspect in pdfs and that is encryption and some of you might remember our pdf x vulnerability from earlier this year it's of course an attack with a logo and it presents two novel tech techniques targeting pdf encryption that have never been applied to pf encryption before so one of them is the so-called direct acceleration where we break the cryptography without even touching the cryptography so knife has no ciphertex manipulation here the second one are so called malleability gadgets and those are actually targeted modifications of the ciphertext of the document but first let's take a step back and let again take some keywords in so pdf uses is okay well is is good nothing can go wrong right so let's go home encryption is fine well of course we didn't stop here but take a closer look so they use cbc mode of operation so cipher block chaining and what's more important is that they don't use any integrity protection so it's unintegrity protected iscbc and you might remember this scenario from the attacks against encrypted emails so against openpgp and s mime it's basically the same problem but first who actually uses pdf encryption you might ask for one we found some local banks in germany use encrypted pdfs as a drop-in replacement for s9 or open pgp because their customers might not want to deal with um set with the setup of encrypted email second one where some drop-in plugins for encrypted email as well so there are some companies out there that produce a product that you can put into your outlook and you can use encrypted pdf files instead of encrypted email we also found that some scanners and medical devices were able to send encrypted pdf files via email so you can set a password on that machine and they will send the encrypted pdf via email and you have to put in the password some other way and lastly we found that some governmental organizations use encrypted pdf documents for example the us department of justice allows for the sending in some claims via encrypted pdfs and i've exactly no idea how you how they get the password but at least they're allowed so as we are from academia let's take a step back and look at our attacker model so we've got alice and bob alice wants to send document to bob and she wants to send it over an unencrypted channel or a channel she doesn't trust so of course she decides to encrypt it second scenario is they want to upload it to a shared storage for example dropbox or any other shared storage and of course they don't trust the storage so again they use end-to-end encryption so let's assume that this shared storage is indeed dangerous or malicious so alice will of course again upload the encrypted document to the attacker in this case we'll perform some targeted modification of that and will send the modified document back to bob who will happily put in the password because from his point of view it's undistinguishable from the original document and the original plain text will be leaked back to the attacker breaking the confidentiality so let's take a look at the first attack on how we did that that's the direct acceleration so breaking the cryptography without touching any cryptography as i like to say but first encryption in up in a nutshell pdf encryption so you have seen the structure of a pdf document there's a header with a version number there's a body where all the interesting objects live so there's our confidential content that we want to actually to actually exfiltrate as an attacker and finally there's xrf table and the trailer so what changes if we decide to encrypt this document well actually not a whole lot so instead of the confidential data of course there's now some encrypted ciphertext okay and the rest pretty much remains the same the only thing that is added is a new value in the trailer that tells us how to decrypt this data again so there's pretty much of the structure left unencrypted and we thought about why is this and we took a look at the standard so this is an excerpt from the pdf specification and i've highlighted the interesting parts for you encryption is only applied to strings and streams well those are the values that actually can contain any text in a document and all other objects are not encrypted and that is because well they want to allow random access to the whole document so no passing the whole document before actually showing page 16 of the encrypted document well that seems kind of reasonable so but that also means that the whole document structure is unencrypted and only the streams and strings are encrypted this reveals a lot of information to an attacker that he or she shouldn't have probably that's for one the number and size of pages that's the number and size of objects in the document and that's also including any links so any hyperlinks in document that are actually there so that's a lot of information an attacker probably shouldn't have so next we thought maybe we can do some more stuff can we add our own unencrypted content and we took a look at the standard again and found that there are so called crypt filters which provide finer granularity control of the encryption this basically means as an attacker i can change a document to say hey only strings in this document are encrypted and streams are unencrypted that's what the identity filter is for i have no idea why they decided to add that to a document format but it's there so that means there's support for partial encryption and that means attacker's content can be mixed with actual encrypted content and we found 18 different techniques to do that in different readers so there's a lot of ways to do that in the different readers so let's have a look at the demo so we have this document this encrypted document we put in our password and get our secret message we now open it again in a text editor we see in object 40 down here there's the actual cipher text of the object so the message and we see it's is encrypted with a 32-byte key so it's is 256. okay now we decide to add a new object that contains well plain text and well we simply add that to the contents array of this document so we say display this on the first page save the document reopen it and we'll put in our password and oh well this is indeed awkward okay so now we have broken the integrity of an encrypted document well you might think maybe they didn't want any integrity in their encrypted files maybe that's the use case people have i don't know but we thought maybe we can somehow exfiltrate the plain text this way so again we took a step back and looked at the pdf specification and the first thing we found were so called submit form actions and that's basically in the same as form on a website you can put in data you might have seen this in a contract in a pdf contract where you can put in your name and your address and so on and so on and the data that is saved inside of that is saved in strings and streams and now remember that is everything that is encrypted in a document and of course you can also send that back to an attacker or well to a legitimate use case of course while clicking a button but clicking buttons is pretty lame so we again looked at the standard and found the so called open action and that is an action for example submitting a form that can be performed upon opening a document so how might this look this is how a pdf form looks already with the attack applied so we've got an url here that is unencrypted because all strings in this document are unencrypted and we've got the value object2o where the actual encrypted data lives so that is the value of the form field and what will happen on the attacker side as soon as this document is opened well we'll get a post request with the confidential content let's have a demo again we have this document we put in our password it's the original document you have already seen we reopen it in a text viewer or a text editor again see it's encrypted and we decide to change all strings to the identity filter so no encryption is applied to strings from now on and then we add a whole blob of information for the open action and for the form so this will be open this will be performed as soon as the document is opened there's a ul p df and the value is the encrypted object 40. we start an http server on the domain we specified we open the document put in the password again and as soon as we open the document adobe will helpfully show us a warning but they will already click the button for remembering that for the future and if you accept that you will see your secret message on the attacker server and that is pretty bad already okay the same works for hyperlinks so of course there are links in pdf documents and as on the web we can define a base url for hyperlinks so we can save all urls from this document start with http p.e f and of course we can define any object as a url so any object we prepare this way can be sent as a url and that will of course trigger get request upon opening the document again if we defined an open action for the same object so again pretty bad and breaks the confidentiality and of course everybody loves javascript and pdf files and that works as well okay let's talk about ciphertext attacks so actual cryptographic attacks no more not touching the crypto so you might remember the e-fail attacks on openbgp and s mime and those had basically three prerequisites one were ciphertext many abilities so it's called mediability gadgets that's why we need ciphertex variability and we've got no integrity protection that's a plus then we need some known plain text for actual targeted modifications and we need an exfiltration channel to send the data back to an attacker well acceleration channels are already dealt with as we have hyperlinks and forms so we can already check that nice let's talk about ciphertext mediability or or what we call gadgets so some of you might remember this from crypto101 or whatever lecture you ever had on cryptography this is the decryption function of cbc so cypher blockchaining and it's basically you've got your ciphertext up here and your plain text down here and it works by simply decrypting a block of ciphertext xoring the previous block of text onto that and you'll get the plain text so what happens if you decide to change a single bit in the cipher text for example the first bit of the initialization vector well that same bit will flip in the actual plain text wait a second what happens if we happen to know a whole plain text block well we can ixor that onto the first block and basically get all zeros or what we call a gadget or a blank sheet of paper because we can write on that by taking a chosen plain text and ignoring that onto this result and this way we can for example construct urls in the actual ciphertext or in the actual resulting plain text what we can also do with this gadget is gadgets is moving them somewhere else in the document cloning them so we can have multiple gadgets at multiple places in the cipher text but remember if you do that there's always other launch effect of cbc's so you will have some random bytes in here but the url still remains in place okay that's ciphertext mediability done as i've said we need some plain text we need to have some known plaintext and as the pdf standard has been pretty helpful up until now in breaking pdf encryption let's take a look again and with what we found where permissions so pdf document can have different permissions for the author and the user of the document this basically means the author can edit the document and the users might not be able to do that and of course people started to change with that well it started to
amper with that value if it was left unencrypted so in the newest version it was decided this should be encrypted as a 16 byte value so we've got 16 bytes how do they look well at first we need room for extension we need lots of permissions then we put four bytes of the actual permission value that is also an unencrypted formula document then we need one byte for encrypted metadata and for some reason we need some acronym adb i'll leave it to you to figure out what that stands for and finally we've got four random bytes because we have to fill up 16 bytes and we have run of out of ideas okay we take all of that encrypt it and oh well we know a lot of that and that is basically known plain text by design which is bad let's look at how this looks in a document so you see the perms value i've marked it down here that is the actual extended value i've shown you on the last slide and above that you see the unencrypted value that's inside this pumps value so the minus four in this case it's basically a bit field on the right side you see the actual encrypted contents and helpfully all of this is encrypted under the same document white key in the newest version of the specification and that means we can reuse this plain text anywhere in the document we want and we can reuse this to build gadgets to send that last point up for you adobe decided to add permissions to the pdf format and people started tampering with them so they decided to encrypt these permissions to prevent tampering and now known plain text is available to attackers all right so that's basically all of the prerequisites done and let's again have a have a demo so we again open this document put in our password well as soon as chrome decides to open this document we put in our password it's the same as before now i've prepared a script for you because i really can't do this live and it basically does what i've told you it's getting a blank gadget from the pumps value it's generating a url from that it's generating a field name so that it will look nice on the server side we regenerate this document and put a form in there we start a web server open this modified document put in the password again and oh well chrome doesn't even ask so as soon as this document is opened in chrome and the password is put in we'll get our secret message delivered to the attacker okay so we took a look at 27 viewers and found all of them vulnerable to at least one of our attacks so some of them work with no user interaction as you have seen in chrome some work with user interaction in specific cases as you've seen with adobe with a warning but generally all viewers were attackable in one way or the other so what can be done about all of this well you might think signatures might help that's usually the first point people bring up a signature on the encrypted file will help well no not really why is that well for one a broken signature does not prevent opening the document so it will still be exfiltrated as soon as the password is put in signatures can be stripped because they are not encrypted and as you have seen before they can also be forged in most viewers signatures are not the answer closing filtration channels is also not the answers because the answer because for one it's hard to do and how would you even find all excitation channels in eight patented pages standard and i mean we have barely scratched the surface here of excitation channels and should we really move forms and hyperlinks from documents and should we move javascript okay maybe we should and finally if you have to do that please ask the user before connecting to a web server so let's look at some vendor reactions apple decided to do exactly what i've told you to add a dialog to warn the user and even show the whole url with the encrypted plain text and google decided to stop trying to fix the unfixable in chrome they fixed the automatic exfiltration but there's really nothing they can do about the standard so this is a problem that has to be done in the standard and that is basically that for mitigating wrapping attacks we have to deprecate partial encryption and disallow access from unencrypted to encrypted objects and against the gadget attacks we have to use authenticated encryption like is gcm okay and adobe has told us that they will be escalating this to the iso working group that's now responsible for the pdf standard and this will be taken up in the next revision so that's a win in my book thank you so much guys that was really awesome uh please queue up by the microphones if you have any questions we still have some time left for q a um but i think your research is really really interesting because it opens my mind to like how would this actually be able to be misused in practice like and and i don't know like what's your take i guess since you've been working so much with this you must have some kind of idea as to what devious things you could come up with i mean it's still an attacker scenario that requires a lot of resources and a very motivated attacker so this might not be very important to the normal user let's be real here so most of us are not targeted by the nsa i guess so you need an active attacker an active man in the middle to actually perform these attacks great thank you and then i think we have a question from microphone number four please uh yes you said that the next standard might have a fix do you know a time frame on how long it takes to build such a standard well no we don't really know we have talked with adobe and they told us they will show the next version of the standard to us before actually releasing that but we have no time frame at all for them okay thank you thank you microphone number five please thank you for the very interesting talk um you showed in the first part that the signature has like these four numbers with the byte range and why is this like four numbers not part of the signature is there a technical reason for that because the byte offset is predictable it is the byte range is protected by the signature but we just defined the second one and just moved the signed one to be validated later so there are two byte ranges okay but only but only the first one the manipulated one will be processed thank you thank you so much microphone number four please um oh this is way too high for me okay i have an answer and a question for you uh you mentioned during the talk that you weren't sure how the department of justice distributes the passwords for encrypting pdfs the answer is in plain text in a separate email or as the password of the week which is distributed through various means that is also what the department of homeland security does and the military is somewhat less stupid um as a question i have roughly a half terabyte of sensitive pdfs that i would like to scan for your attack and also for redaction failures do you know of any fast feasible ways to scan documents for uh the presence of this kind of attack i don't know of any tools but i mean scanning for the gadget attacks is actually possible if you try to do some entropy detection so because you reuse ciphertext you will have less entropy in your ciphertext but that's pretty hard to do diode acceleration should probably be detectable by scanning simply for words like identity or the other 18 different techniques that we provided in the paper but i don't know of any tools to do that automatically thank you great thank you and microphone number two please thank you for very interesting presentation i have one suggestion and one question for the mitigation scheme if you simply run your pdf reader in a virtual machine that's firewalled away so your firewall will let you to anybody going out but for the signature forgeries i had an idea i'm not sure if this is actually a stupid idea but did you consider faking the certificate because presumably the signature is protected by the certificate you make up your own sign it with that does it catch it and how we consider it but not in this paper um we assumed that the certificates and the entire chain of trust for this part is totally secure it was just an assumption to just concentrate only on attacks we we already found so perhaps there there will be further research provided by us in the next months and years we might just hear more from you in the future thank you so much and now questions from the internet please um uh i have two questions to the first part of your talk um from the internet the first one is uh you mentioned a few reactions but can you give a bit more detail about your experience with vendors while reporting these issues yeah we for the first time we started um we we asked the third team from bsi setbund um to help us because there were a lot of affected vendors and we were not able to to to provide the support in them in a feasible way so they supported us the entire way we first created a report with containing the exact description of the vulnerabilities and all the exploits then we distributed it to the bsi and they contacted the vendors and just proxied the communication and there was a lot of communication so i'm not aware of the entire communication but only about the technical stuff where we were asked to just um retest the the fix and so on so there was a reaction um from adobe fox it and a lot of viewers reacted on our attacks and contacted us but not everybody thank you so much unfortunately that's the only time that we have available for questions today i think you guys might stay around for a couple of minutes just if someone has any more questions fabian icing and vladislav thank you so much it was very interesting please give them a great round of applause thank you you